It can’t have escaped everyone’s attention, since the move to the cloud the number of data breaches has gone through the roof. In this article, I’m going to run through why this is happening, why workplace policy won’t fix it, and what your organization can do to reduce the risk of being next.
Why so many data breaches in the cloud?
The simple answer here is autonomy. In the days before cloud computing all servers and infrastructure were set up and configured by an operations team.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

The process was ultimately cumbersome, slow, and overall frustrating to most businesses. Cloud computing allowed developers and other teams within businesses to set up their own infrastructure without too much knowledge of networking, firewall rules and other security practices.
This means that projects get off the ground much quicker and businesses are more agile. It also means that the operations team, who used to act as the police department of IT, have also lost visibility of what is going on. Or, more likely, there’s so much going on they can’t possibly keep track of what’s been built and where misconfigurations and security risks are.
Why don’t security policies work?
A classic mistake made by many organizations is to make something publicly accessible and with open access. This could be a database, storage bucket, or any other easily accessible data store. This really is the easiest thing to remedy, you simply have a policy that says ‘do not open up data storage to the general public’. Problem fixed.
The issue with this is, as all parents of young children know, you can say something until you’re blue in the face but someone, somewhere, will still misconfigure data storage so it’s accessible publicly. There are just simply too many possibilities for misconfiguration, too many users in an organization with the power to spin up infrastructure and too few IT administrators to keep track. You need an automated system to keep you in line and alert you.
How can I protect my cloud against misconfiguration?
It has taken a little while for software companies to catch up and until recently you have needed an army of scripts and custom alerts to keep your infrastructure in check. The good news is that cloud workload protection tools are becoming more mature. The latest iterations of cloud tools are exactly what industries have been crying out for.
If you have been doing this in-house until now it’s time to reconsider the benefits of an off-the-shelf solution, they will undoubtedly offer greater coverage than you are able to muster on your own.
What are the features of cloud protection tools?
Let’s look at 4 of the main features
1. Excessive permissions
It’s only too common for users to be given too much privilege and/or for services to be granted roles that they do not need. Software now analyses user’s permissions, highlights where users or services have been over-provisioned and makes recommendations to resolve it.
2. Exposed assets
As mentioned earlier one of the most common faults is to leave assets exposed to the public, these can now be automatically screened and captured:
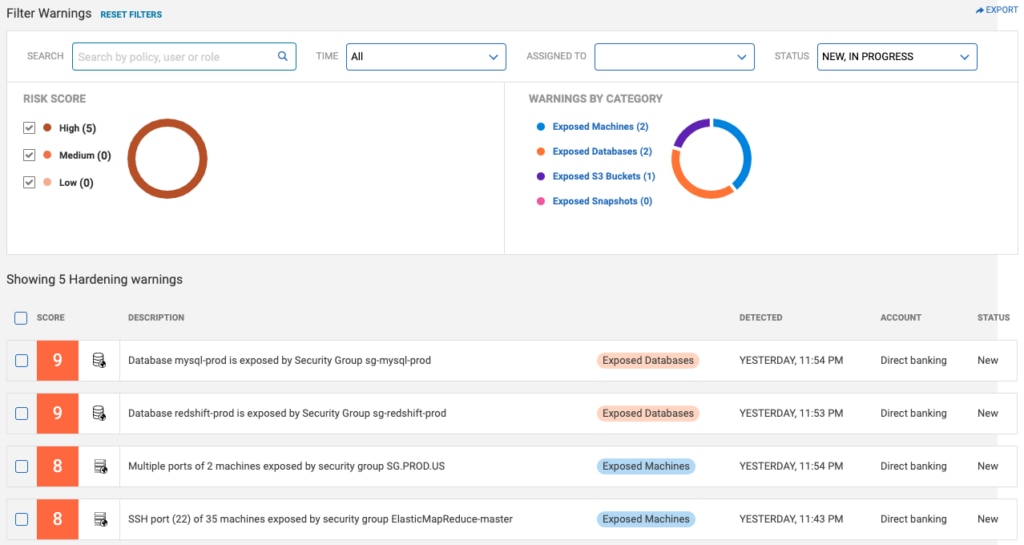
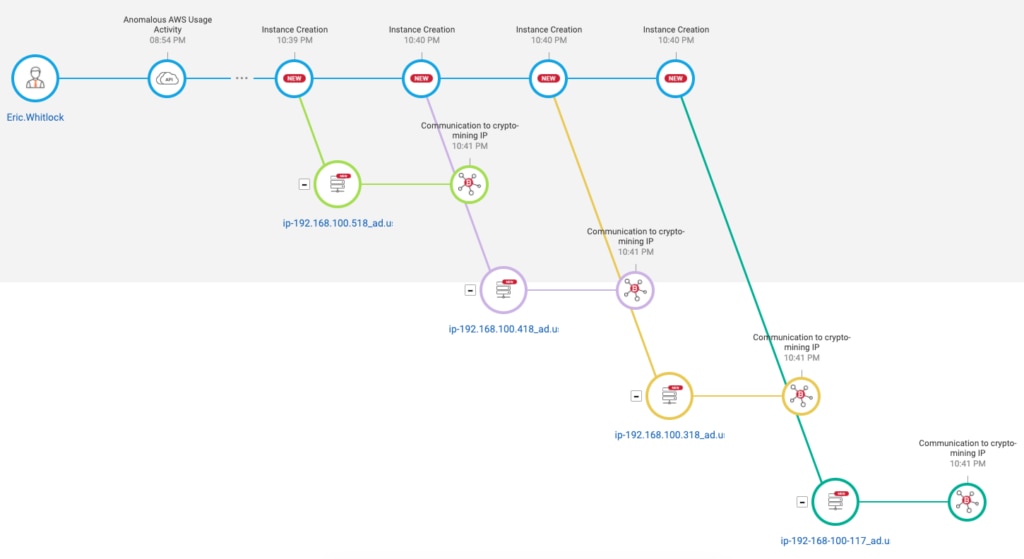
3. Attack summaries
By plugging into flow logs and cloud trial systems the latest protection software can provide you with a step-by-step analysis of what unusual activities have been happening in your account. Below we see an example of a compromised user account being used to setup a crypto mining server and communicate to an external IP:
4. Compliance reports
If anyone has ever had to prove to an auditor that they have met this or that ISO standard, then they’ll know what a pain it is to track this and to prove this. With cloud protection software you get out of the box ISO standards reports and CIS compliance reports.
This means with virtually no effort you can track and trace things like the use of a root user, if MFA tokens are being used and if certain ports are open (to name a few):
What’s the main advantage of these tools?
It has taken a while for security firms to learn what a good cloud platform looks like. Now that these companies have an understanding of what cloud platforms should look and behave like, it has become much easier to spot misconfigurations in yours. We also have machine learning and AI to more easily spot anomalies in your platform.
The end result is very smart insights into your security posture with almost no administrative overhead on your behalf. These tools only need to plug into your audit trail and within a day they provide rich insight into what’s really happening in your estate. No more “we should be OK” … followed by a nasty surprise!
Sounds interesting, how do I find out more?
Luckily, as of the time of writing this, vendors are offering free POC’s to prove the value. No commitment to buy and very easy to setup.
If you have any questions, contact us today to help you out with your performance and security needs.






