Overview
Phishing continues to be a major attack vector, and it’s surprising just how many security incidents and breaches start with an employee clicking on a link in a carefully crafted phishing email (and sometimes doing the same with a not-so-well crafted phishing email — see this example).
There’s still a general perception that phishing attacks are more of a risk to consumers than businesses. To an extent that’s true — enterprises deploy security tools to block phishing attacks and now most employees receive ongoing phishing-awareness training. Consumers, on the other hand, may rely on their ISP for protection and are more susceptible to scams (no, the government does not want to give you a tax refund).
But there’s been a major change. According to research published by Akamai, there was a rapid increase in enterprise traffic related to remote working in 2020 — that’s not terribly surprising. What is likely more surprising is that the research also showed a dramatic increase in the consumption of services such as streaming, gaming, and social media from enterprises remotely connected devices.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

This can be explained by changes in the way our personal and professional lives have blurred, and that many users are now using the same device for work and play. This means that phishing attacks targeted at consumers or businesses now carry equal risk for an enterprise. In other words, it doesn’t matter if an employee’s laptop is compromised as a result of a phishing attack designed to steal their personal bank account details or their employee credentials — the end result is a compromised device that is connecting to the enterprise’s network.
Let’s now take a look at what Akamai observed in the phishing landscape last holiday season.
Phishing Trends Over the Holiday Season
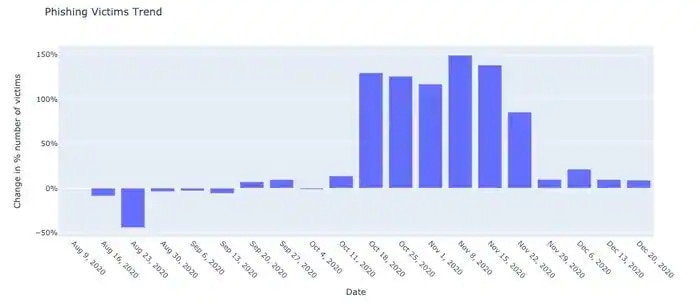
Based on Akamai platform traffic, we can see that the number of phishing attack victims increased dramatically from the second half of October to the end of November. During that six-week period, there was an increase of nearly 150% in phishing victims. We attribute that increase to the following reasons: the state of mind of internet users and the motivation for cybercriminals to launch more attacks.
Users are more vulnerable to phishing attacks over that six-week period as the holiday shopping season leads to higher levels of engagement with scams, specifically those that offer deals and coupons — we all want a bargain. Because victims are potentially more susceptible to scams, the holiday season leads cybercriminals to execute a variety of nefarious activities and launch all kinds of phishing campaigns as their potential success rates will improve the more they try.
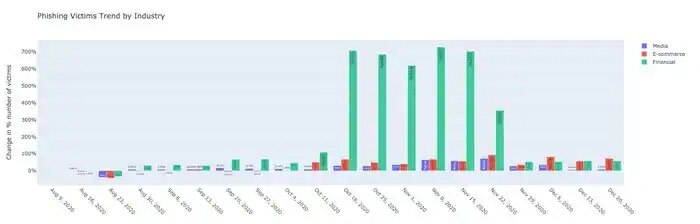
A look at the leading targeted industries by growth in the number of victims shows that media, e-commerce, and financial services showed significant increases over the same time frame. However, much more noticeable are phishing attacks targeted at financial services with an increase of more than 700% in victims compared with the previous weeks. The increase in financial scams can be explained by cybercriminals’ efforts to maximize their campaign activity over the holiday season as victims are more engaged and as compromised financial credentials are highly valuable.
Minimizing the Risk of Phishing Attacks
There are a number of things enterprises can do to improve their defenses against phishing attacks.
- Ensure that phishing training is ongoing and is adapted to cover the need to be vigilant about consumer-based attacks.
- Review existing phishing protections — Akamai has observed that phishing is no longer just an email problem. Attacks are increasingly being launched via social media and messaging apps. So looking at approaches to mitigate these attack vectors is key.
- Consider tools that can identify and block requests to brand-new phishing pages in real-time and at the point of request; even if the page has never been seen before. These types of tools provide an additional layer of real-time protection.
- Introduce Zero Trust to your organization if you’re not there yet. Start with this short guide for quick orientation.
Contact us to start your Zero Trust journey today, and finish it quicker than you imagine.
Originally published by Akamai Technologies






