Hosting, Hardware & Networking
Making IT happen, anywhere.
Local boots on the ground is key for quick, cost-effective business expansion. Our international network of technical teams, data centers, and logistic centers, makes it all a breeze – from an offshore office or server to equipping your newest recruit for remote work. We plan, execute, and hand you the key to state-of-the-art infrastructure, optimized for your every demand.

Go Beyond Legacy Solutions
We at GlobalDots hunt for the most cutting edge and relevant technologies out there.
Once tested and found qualified we bring you the most certified innovative products out there for every pressing use case.

Our Hosting, Hardware & Networking Partners
-
Dots
A powerful ITAM software, combined with a world-class logistics network
-
Corporate IT
Servers for on-premise data storage and networking, plus all endpoint devices and peripherals – both for offices and remote teams.
-
Colocation & Hosting
The full range of data storage & networking services: dedicated & managed web hosting, managed physical & virtual data centers, including support, migration, and managed services.
-
Internet & Connectivity
A complete internet connection & security solution to support enterprise networking worldwide.
-
Hardware (Procurement as a Service)
Taking the load of negotiation, benchmarking and purchase off your teams while leveraging our powerful commercial position.
-
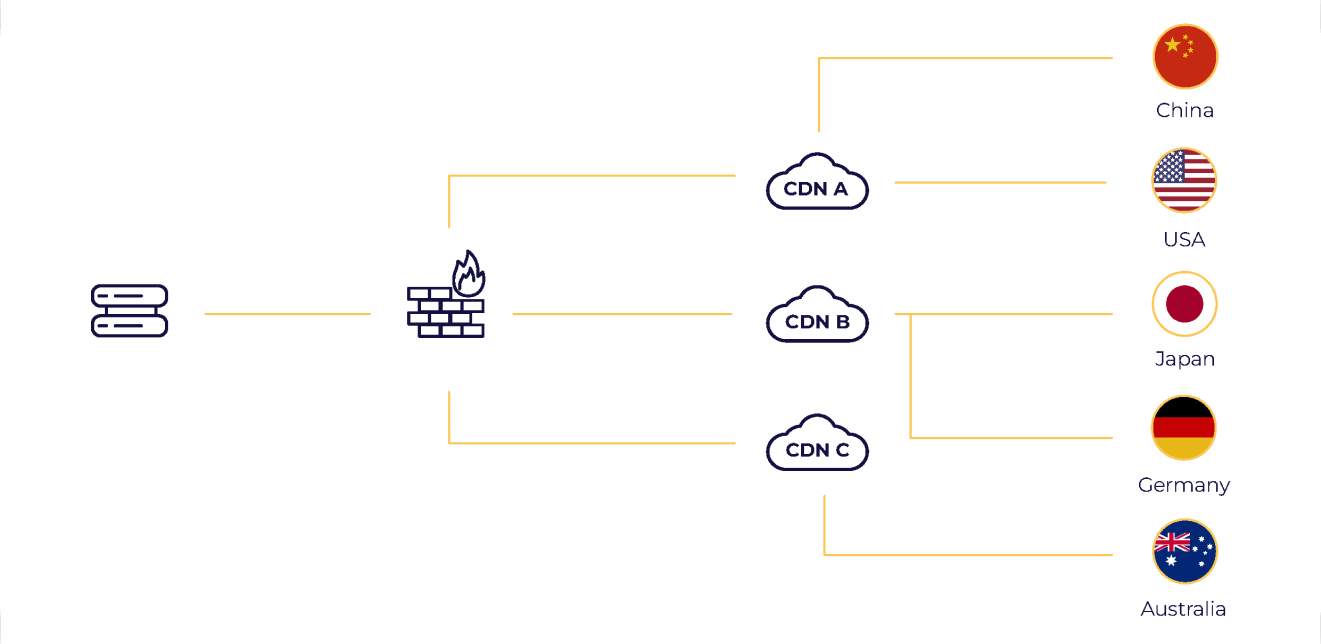
China Connectivity
One contact for the full suite of Mainland China colocation, networking, connectivity, and security, all by licensed providers.
-
Network Operations Center (NOC)
Flexible, modular network service solution delivered by experts, 24/7/365
-
SD-WAN and SASE
Experience enterprise networking as a cloud-based service, dramatically reducing complexity and TCO.
What makes a global-scale IT partner
As you shut offices down and grow your remote teams, one partner handling both processes simultaneously, on both technical and logistical aspects, is priceless.

Strategizing your data storage according to your business needs & plans, choosing the right hardware, then customizing and configuring it, gets the full load off your shoulders.

Tap into the Cloud’s agility and speed benefits by choosing a partner capable of supporting hybrid infrastructures or full cloud migration and managed services.

To quickly and cost-effectively execute global expansion, seek a partner with local connections on your geos of interest: to vendors, technical teams, and logistics service providers.

Stay Cloud-to-Date
The world of cloud changes quickly. Stay up-to-date with the latest trends & innovation, extensively explored in our resource library.
-
Zero Trust Access ManagementOperational Insights from a Zero Trust and Email Security Roundtable
This blog is based on a closed roundtable discussion on Zero Trust and email security, where practitioners shared how these controls are implemented and operated in real-world environments. Not a conference. Not a product showcase. Just open conversations about what works, what breaks, and what needs to be adapted once theory meets reality. Across very […]
-
Cloud SecurityThe Security Blind Spot: Business Logic Failures and How to Catch Them
Security leaders know the drill: vulnerability scanners run their course, reports stack up, and yet attackers still slip through. What’s going wrong? We sat down with Yosef Yekutiel, CISO & Data Privacy Officer at MaccabiDent, at GlobalDots’ recent “Red Team Reality Check” event to unpack this gap, and how modern offensive security can fill it. […]
-
Monitoring, Logging & ObservabilityHow NetRefer Cut Observability Costs by €96,000 Per Year in Just 3 Months with GlobalDots
Overview NetRefer, a leading iGaming affiliate marketing platform, utilized Azure cloud-native monitoring tools. Shortcomings needed to be resolved, and the business required next-generation observability. Problems that needed to be solved: Through GlobalDots’ expertise in selecting and implementing the right observability solution, NetRefer achieved €96,000 in annual savings and gained real-time observability across their entire platform […]
-
Web SecurityVulnerability Assessments vs. Penetration Testing: Key Differences, Use Cases & Best Practices
They’re not interchangeable. A vulnerability assessment identifies known flaws at scale. A penetration test mimics an actual attacker probing for impact. Yet many teams treat them the same. They substitute one for the other, check a compliance box, and move on as if they’re covered. They’re not. And that gap shows up later in real-world […]
-
Web SecurityWeb Application Firewalls (WAFs): The Evolving First Line of Defense in Cloud Security
Modern applications are built for speed, not simplicity. Containers, microservices, and cloud-native deployments have blown up the security perimeter. Traditional tools can’t keep up with this complexity. That’s why Web Application Firewalls (WAFs) matter. But the WAF of 2025 isn’t just an appliance sitting in front of a static website. It’s a flexible, cloud-aware security […]
-
FinOpsHow Labguru Slashed Cloud Storage Costs While Boosting Performance
Customer Overview Founded in 2007, Labguru, the flagship product of BioData, is a versatile and unified cloud-based data management platform that supports a wide range of laboratory and research activities. Trusted by over 750 global customers – including national research institutes, academic institutions, pharmaceutical companies, and innovative biotech startups – Labguru plays a pivotal role […]
-
FinOpsGaming Company SuperPlay Reduces ElastiCache TCO with Strategic Optimization
About the Customer: SuperPlay is a leading Israeli gaming company that develops and publishes mobile games for a global audience. The company specializes in creating engaging social casino and casual gaming experiences, reaching millions of players worldwide. As a technology-driven gaming company, SuperPlay relies on robust cloud infrastructure to deliver seamless gaming experiences to their […]
-
Web SecurityWhat is an API Security Audit?
In January 2024, a misconfigured API exposed 650,000 private messages. These included passwords and internal communications. No exploit chain. No zero-day. Just a public-facing endpoint with no authentication. This wasn’t an isolated incident. From T-Mobile and Twitter (now X) to Kronos Research and the US Treasury, attackers have consistently used APIs as entry points. They […]
-
Web SecurityThe Ultimate API Security Checklist for 2025
APIs are now the top attack vector in enterprise apps. In 2024 alone, breaches tied to APIs cost an average of $4.88 million, and that number is rising fast. Attackers exploit gaps in API authentication, input validation, and outdated endpoints to compromise systems. Legacy controls no longer suffice, and the OWASP API Top 10 outlines […]
-
Web Security10 API Security Best Practices for 2025
APIs are the backbone of today’s interconnected software. They power everything from mobile apps and SaaS platforms to internal microservices and partner integrations. But their rapid growth has left many security teams flat-footed. In 2025, many attackers prefer to exploit API misconfigurations hiding in plain sight. What used to be fringe cases (token leakage, zombie […]
-
Web SecurityAPI Security in 2025: Practical Assessment & Modern Protection Strategies
APIs are no longer an edge case. In 2025, they’re a core requirement for maintaining trust, compliance, and operational continuity. As organizations build more API-driven systems—from customer apps to internal microservices—the exposure risk compounds. And quickly, too. Even mature security teams are finding that traditional tools can’t keep pace with the volume, velocity, and nuance […]
-
DevOps & Cloud ManagementMVP to Production-Grade: How to Fix Scaling Bottlenecks Before They Break You
This webinar & podcast are built for founders, CTOs, and VPs navigating the critical shift from MVP to production-grade infrastructure. Learn how to avoid scaling pitfalls, build resilient systems without over-hiring, and make the right decisions now to support rapid, sustainable growth. Join us to unlock practical strategies and real-world lessons from companies that have […]
-
Web SecuritySAST vs DAST vs IAST: Application Security Testing Explained
A great majority of security flaws are introduced during development, but most aren’t found until much later, when they’re costlier to fix. That delay is precisely why application security testing (AKA AppSec testing) needs to occur early, frequently, and at multiple layers. SAST, DAST, and IAST are designed to do just that. But too often, […]