The website experience that consumers value most
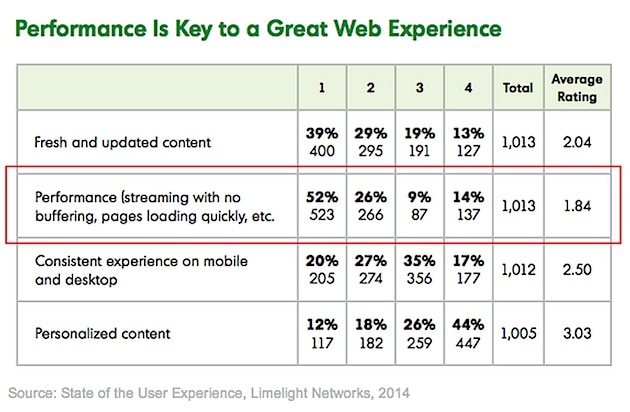
52% of the US consumers say high performance is the quality they value most in website experience, according to Limelight Networks’ recent report. Website performance is the most important digital eperience, meaning that no buffering streams and fast loads go ahead of fresh and updated content. These are some of the report’s key findings:
- 59% of respondents say they will wait no more than five seconds for a webpage to load before becoming frustrated and leaving the site.
- 37% say they will leave and buy a product from a competitor if a website is slow, and 26% say they might/are not sure.
- 50% of respondents say most of the time they use either a smartphone or a tablet to access websites; 85% use a mobile device at least some of the time to access websites.
- 44% of respondents are willing to wait longer for a website to load on a mobile device; 40% expect websites to be equally fast to load on mobile and desktop.
A high performing website is key to a great web experience. 60% of consumers abandon the site if it takes more than 5 seconds to load. While laptops are still the most used device, 50% users use a smartphone or a tablet to access sites and 40% consumers expect websites to be equally as fast on mobile as to desktop.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Read more at MarketingProfs.
You can download the full report here.
Google Now Factoring HTTPS Support Into Ranking; CloudFlare On Track to Make it Free and Easy
Google announced that they will start taking into account whether a site supports HTTPS connections in their ranking algorithm. Your site’s HTTP support should be your priority if you care about your Search Engine Optimization. In a very fast response, CloudFlare pushed a new code allowing to load SSL certificates on demand, meaning that a certificate only needs to be in a data center, not on a particular server, before HTTPS traffic needing the certificate is directed to that server. When a request is received, the server can now dynamically retrieve the correct certificate even if it hasn’t been previously loaded into memory, allowing to continue to shift traffic to manage the network even if the SSL certificates for millions of domains are being managed.
Read the full report at CloudFlare blog and official Google blogs here or here.
HTTP/2.0 and DASH: planning tomorrow’s improved video delivery
HTTP traffic has grown extensively due to the immense growth of multimedia traffic. It could be seen as the protocol to deploy new services and applications and it is also heavily used by the industry, providing advanced features for modern internet architectures:
- It is a content centric protocol that decouples names from addresses through DNS
- It provides caching elements and middle boxes as reverse and forward proxies
- It enables scalable and flexible content deployment with content distribution, already leveraged by Content Distribution Networks (CDN)
HTTP streaming solutions such as Microsoft Smooth Streaming and Apple HTTP Live Streaming do not use HTTP/1.1 pipelining with persistent connections, which could increase the streaming performance by up to 30 percent. However, there are not many proxies that support HTTP/1.1 pipelining with persistent connections, due to the Head-of-Line (HoL) blocking problem.
For RTTs that are typical for mobile access connections, the link usage only ranges from 75% to 85%, caused by TCP slow start that influences every segment request. HTTP/1.1 resolves this issue with persistent connections and pipelining, enabling RTT tolerance and link usage higher than 93% for fixed and mobile access connection. HTTP/2.0 offers these functionalities implicitly, while in case of HTTP/1.1 it is not possible to use these features at any time due to proxies and servers that do not support these features, as they are optional and not mandatory.
Check the full report at StreamingMedia.
Evolving web threats demand new approaches to security
DDoS attacks are on the rise in Asia Pacific with over 1,153 attacks being reported and 188 countries recording online threat and malicious activity in 2013. The main concern with security is the lack of adoption and the inability of businesses to adapt and change according to the security landscape. Attacks are damaging and force organizations to regularly audit their security solutions and update tools to be in line with best practices. Most of the enterprises rely on web application firewalls which can often lead to lagging data performance and poor user experience.
Organizations today need a well-rounded security solution that will scale reliably and evolve itself to provide protection from a growing list of online threats. With the attacks evolving and increasing, the solution is to employ a trusted third-party supplier with the technology, skill and experience to defend critical business applications against attacks and to deliver external and internal company networking.
Full article at InformationWeek.
Major security vulnerability in WordPress, Drupal could take down websites
WordPress and Drupal are used by millions of websites. The latest statistics from W3Techs shows WordPress alone powers nearly 23% of the web. The vulnerability uses a well-known XML Quadratic Blowup Attack — and when executed, it can take down an entire website or server almost instantly. Both WordPress and Drupal have released patches for their applications. Users and web hosts simply need to upgrade to the latest version to protect against the vulnerability.
The vulnerability uses what is called an XML Quadratic Blowup Attack, it just repeats one large entity with tens of thousands of characters over and over again. The attacker needs to fingerprint the available memory limit on the victim’s server. A successful attack will bring down the system. The attack will have zero success if it overwrites the PHP limit, simply because the server will reject the overwrite. WordPress 3.7 introduced automatic updates to help protect it’s users from DDoS’ Blowup Attacks.
Read the full article at Mashable and be sure to upgrade!







