The third quarter of 2017 had its share of cyber security disasters and we’ve made sure to report on each and every network or application attack that happened during these months in our quarterly State of the Internet Security Report, where everything presented in this article is illustrated in greater detail.
Though we haven’t seen attacks of the same magnitude as the ones generated last year, the Mirai botnet is neither gone nor forgotten. This quarter has also seen two attacks that exceeded 100 Gbps, with one reaching 104 Gbps and a second measuring 109 Gbps.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

One of key points this quarter was also the Yahoo breach update, which affected a whooping number of 3 billion accounts on the platform instead of previously reported 1 billion.
Equifax, a major credit reporting company also announced it was compromised and that they’ve exposed sensitive data of 146 million US citizens.
Merck, a pharmaceutical giant and FedEx have announced losses in excess of $300 million each from the impact of NotPetya malware campaign this quarter as well.

The Emerging Trends
There’s an interesting mix of changes going on in regards to DDoS trends this quarter. While the overall attacks are up 8% compared to the previous quarter, they’re still down 3% from the same time the previous year.
Also, after trending downward for the past couple quarters, the median attack size trended upward in the third quarter, returning to the record levels of 2016.
Surprisingly, the highest number of unique IP addresses involved in DDoS attacks came from Germany this time, while in Q2 the largest number of IP addresses originated from Egypt.
When looking at the DDoS attack frequency across industry verticals in the third quarter, the Gaming industry suffered a lion’s share, with 86% of DDoS attacks being directed at their assets, up from 82% in the previous quarter.
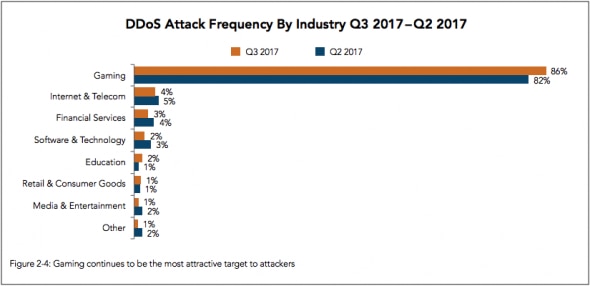
To see full information about emerging trends click here to download the full report.
Distributed Denial of Service Activity
The momentum continued from the last quarter into this one as well and this resulted in a significant increase of the total number of DDoS attacks – 69% more web alerts recorded year over year. Specifically, the jump happened in September and the average number of attacks per target rose to a new high for 2017 of 36 per target.
There are speculations that the spike in September’s traffic can potentially be explained as correlating with the return of students to school. While these are only speculations, it is possible the rise in attacks traffic could be linked to students sharing information and trying new techniques that they might have learned during the summer break in North America, the UK and Europe, among other places.
The top three vectors for Q3 were UDP fragments, DNS and NTP, as shown below:
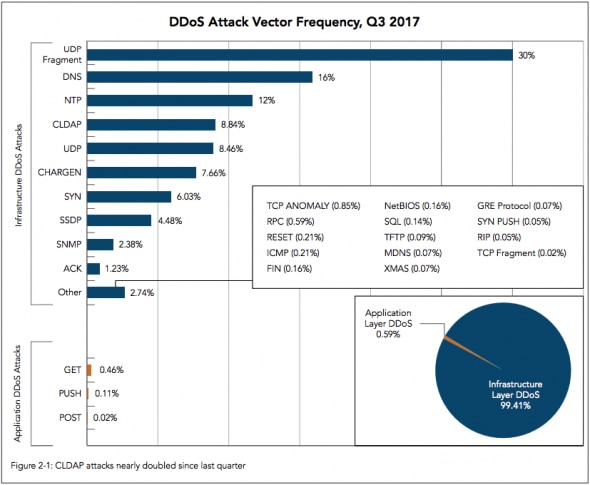
Click here to see the full report
Web Application Attacks
There was a significant jump in web attacks as well. Overall the number rose by 30% in Q3 while the number of attacks in the US jumped 48% over what was documented in Q2. The overall number jumped 69% year over year.
SQL injection attacks are still prevalent which means organizations haven’t taken the necessary precautions to sanitize data input and protect their applications. Given that this is now well known, attackers will use this information to continue to exploit these vectors to gain access to systems.
Most of the web application attacks this quarter came from US, Russia and the Netherlands as shown below:
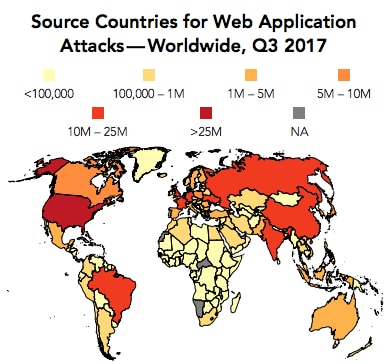
Click here to see the full report
Looking Forward
Both monetary and emotional aspects, which are the most prevalent motivators of attack dynamics, will strongly influence the behavior in the fourth quarter. The most important leverage for cyber criminals will be the fact that the final quarter is critical for merchants, making the merchants more likely to pay an extortion letter threatening an attack.
On the other hand, defenders are getting better at working together and sharing important information to help detect and combat attacks. GlobalDots will continue to bring cutting-edge insight into the ever-changing landscape of attacks and attack tools – delivering the insight to help you and your team protect your organization.
The original report and the research behind it is originally created and conducted by the Akamai research team and you can download the full report by clicking here.






