Does your cloud platform feel like the Wild West? Do you have multiple admins running around causing havoc because you can’t keep tabs on them all? Well you’re not alone and help is at hand. Enter the world of Software Defined Operations or SDO.
Now for those not indoctrinated into the world of SDO already, it may sound like some business jargon invented to keep people in jobs. In fact, nothing could be further from the truth – a properly defined SDO actually reduces the need for head count and gets your business running like a well-oiled machine.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

What is Software Defined Operations?
OK, think of it like this. You have a company policy that says ’All S3 content must be encrypted at rest’. You’re the manager and you individually tell every sysadmin that they are not to create S3 buckets that aren’t encrypted. A month later you check your S3 buckets only to find 30% of them do not have encryption enabled.
The problem here is humans and governance – the two just don’t mix. In society we have the same problem, but to counteract it we employ a police service to keep law and order. SDO is the police force of the digital world. With SDO you can set a policy that says you must encrypt S3 buckets, and when an admin breaks this policy it is either auto-rectified or deleted. The end result is that sysadmins working on systems or platforms cannot break the rules, even if they wanted to!
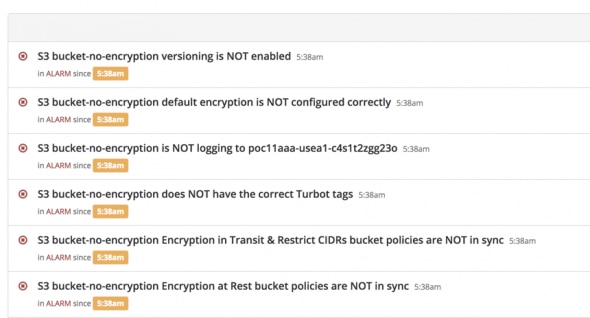
SDO alert dashboard:
How does it work?
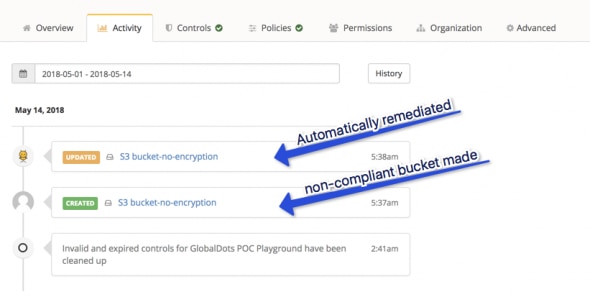
SDO works by integrating directly with your cloud platform and becoming the gatekeeper of the system. By installing this higher level of privilege it means that even admins cannot do something that is outside of the SDO police. Every action taken by someone or something is fed back to the system and either remediated, or triggers an alarm for another operator to make a decision on. SDO works by defining what is and what is not acceptable, and stops your platform from slipping into non-compliance.
SDO Automatic remediation:
What are the benefits?
A well designed SDO architecture will save a cast amount of time typically spent on making sure your infrastructure is compliant. Without SDO GlobalDots has typically seen that around 30% – 40% of DevOps time is wasted making sure other platform admins are adhering to company policy, or fixing errors. With SDO in place sysadmins, and even employees of other companies, can be allowed to self serve on your platform without fear that are going to create a digital mess.
How can it help?
With the new GDPR regulation every company has an obligation to ensure public data is stored in a compliant way. With SDO a Chief Information Security Officer (CISO) can sleep well at night knowing that their company has not fallen foul of EU regulations. Moreover SDO provides a time saving framework that empowers developers and sysadmins to be creative and operate under a self serve environment without compromising cloud security and best practice. If you’re tired of hearing the sound of your own voice, repeating the company policies until your blue in the face, then SDO is for you!
If you’re interested in grabbing the reigns of your cloud and enforcing control the smart way then contact GlobalDots for a free demonstration.






