23rd November, 2017
5 Min read
The internet is a very complicated place consisted of millions of servers containing millions upon millions of websites and data.
Each of these servers has their name – and that name is their IP address. Without IP addresses there wouldn’t be a way to identify which server you need to access in order to get to the website that contains the content you need.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

We can look at these IP addresses as phone numbers which you need to dial in order to communicate with the required servers. In this article we will be talking about Domain Name System (DNS) which is the ‘public phonebook of the internet’ and how enterprise networks can get their infrastructure secured from sophisticated attacks that exploit this ‘public phonebook’ system.
How Does the Domain Name System Work?
To understand how exactly you can protect your business from exploitable flaws the DNS system has firstly we need to understand how it works.
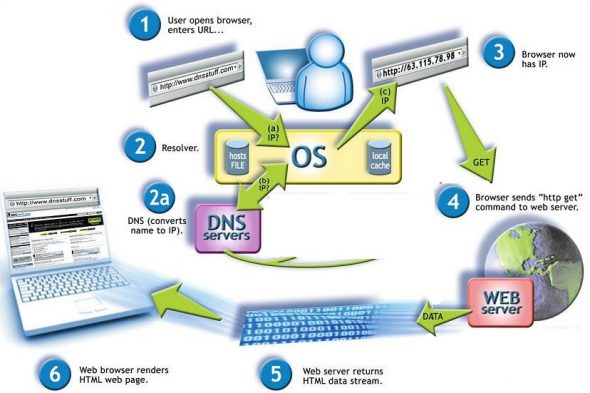
A DNS server resolves names to numbers. To be more specific – if you were to input globaldots.com in your web browser, a DNS server would need to find the IP address associated with that name. In this case, that IP address is 198.102.746.4.
The way a DNS server does this is by recursion – if it doesn’t have an IP address of the required website already stored in its cache it contacts the next DNS server in order to find it and that server in turn returns the address which then comes back to your web browser.
When your web browser has the IP address it can successfully communicate with the server.
Here’s a picture of the whole process, simplified for the purposes of this article:
Recursive DNS and Associated Threats
As we’ve already mentioned, DNS servers are set-up to function recursively by default (we can call them rDNS or Recursive DNS servers as well) and this is the most common weakness that many of today’s hackers exploit.
Why is rDNS easily exploitable:
- It’s ubiquitous – DNS is the core protocol used to perform requests of every kind on the Internet – from web browsing to email to online retail to online computing and it is openly available to anyone on the planet
- It’s open – a DNS server cannot evaluate whether the resource it is connecting to is good or bad, users can inadvertently connect to malicious domains
- It’s unprotected – Firewalls don’t typically inspect DNS port 53, which is used to listen to queries from DNS clients
All recursive DNS exploits start with an infected user’s machine which can be infected by a variety of tactics.
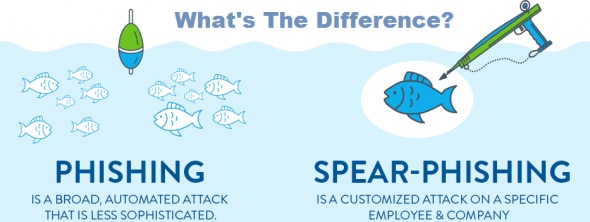
The most common delivery mechanism for this kind of malware are phishing and spear phishing attacks – when a user downloads a malicious attachment or is prompted to click an embedded link. However, the mentioned malware can also gain access to the user’s computer by a malicious download, an infected USB key or even through a compromised domain directly.
Once the malware is on the user’s machine, it will try to contact its command and control center (CnC, also known as C2 or C&C) to send back information about the infected device. This CnC center is actually a server from which the hacker can instruct the malware (automatically) to start doing malicious activities such as downloading remote access tools, additional software components, or updates that exploit the unpatched vulnerabilities of the compromised device.
Not only that, if it so happens that the CnC server has gained access to the end-user machine on the targeted network it can start to spread on all endpoint devices inside that network.
To make it even worse, hackers have created several different tactics to make securing your network even harder like DGAs (Domain Generation Algorithms) and Fast Fluxing.
Domain Generation Algorithms prevent the network detection techniques companies started using like a predefined list of malicious domain names the network users are unable to access. DGA generate a large number of domain names used as rendezvous points with their CnC servers.
Fast fluxing prevents IP-based access control lists from working by taking advantage of the fact that DNS allows an administrator to register a number of IP addresses to a single host name for purposes of load balancing. Fast flux can be used to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies.
Data extraction is also possible through DNS requests. CnC servers, once the computer is infected, are able to extract sensitive data through a process called DNS tunneling. In tunneling, cyber criminals use DNS to smuggle data out of the enterprise by breaking it up into small chunks, hiding them in a DNS query and sending them to a rogue authoritative DNS server they control remotely.
How Securing rDNS Proactively Protects Your Network
Using an rDNS security solution, organizations can achieve a wide range of benefits:
Significantly improve defenses and close DNS security gaps
Recursive DNS security solutions block DNS requests to malware drop sites, malware CnC servers and ransomware sites. They also protect the client from data exfiltration by using the unique and up-to-date threat intelligence.
All ports and protocols secured
As opposed to conventional security solutions which only monitor port 80 (HTTP) traffic or port 443 (HTTPS) traffic the recursive DNS security solutions watches over DNS requests as well.
Attacks are stopped before the IP connection happens
If a DNS request is not served with a corresponding IP address, there’s no connection to begin with. Ideally, this is where blocking should occur since the price of mitigation and detection rise later in the cycle of a typical attack.
Reduced noise
Typically IT security teams get a lot of alerts of possible threats. By stopping threats at a DNS level, organizations see fewer events which makes sure their time is better spent.
Improved HTTPS performance
Nearly all of global internet traffic today is encrypted which means this type of traffic is exploited more and more by malicious actors. Monitoring encrypted traffic is processor intensive because it governs that organizations need to decrypt and inspect it. By using recursive DNS security, the amount of HTTPS traffic is reduced, so fewer traffic needs to be inspected.
Easy set up
Cloud-based recursive DNS security solutions can be configured and deployed in minutes without the need for hardware.
Conclusion
For many enterprises, their recursive DNS is a major gap in their security efforts that many cyber criminals are happy to exploit.
By deploying a recursive DNS security solution, your organization can close your DNS security gaps and significantly improve your security defences. Not only do recursive DNS security solutions secure all ports and protocols, but they also block DNS requests to malware drop-sites, ransomware sites, and malware CnC. Because this blocking occurs farther away from the network perimeter, it reduces the cost of remediation. These solutions even simplify security management by reducing false alarms and improve HTTPS performance by reducing the amount of HTTPS traffic that needs to be inspected.
In case you want to discuss your recursive DNS security options, or simply want to know more about getting the most out of your security and performance implementations, you can talk to one of our in-house GlobalDots experts. They can help you with anything web performance and security related.






