As Kubernetes gained widespread adoption in production environments, it became more attractive to attackers. Its distributed and dynamic nature made it a favorite for scalable and flexible containerized applications, but it also introduced some vulnerabilities and misconfigurations that can be exploited.
For an attacker looking to exploit a Kubernetes cluster, reconnaissance is a critical first step. This is where they map the environment, identify entry points, and plan exploits.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

In this article, you’ll look over the shoulder of an attacker to learn the Kubernetes reconnaissance playbook so you can secure your Kubernetes clusters against these threats.
Setting the Scene for Reconnaissance in Kubernetes
Reconnaissance is how attackers gather critical information about a Kubernetes cluster — its structure, components, and potential weaknesses. Speaking of components, we need to understand what they are and how they interconnect to fully grasp how attackers conduct recon.
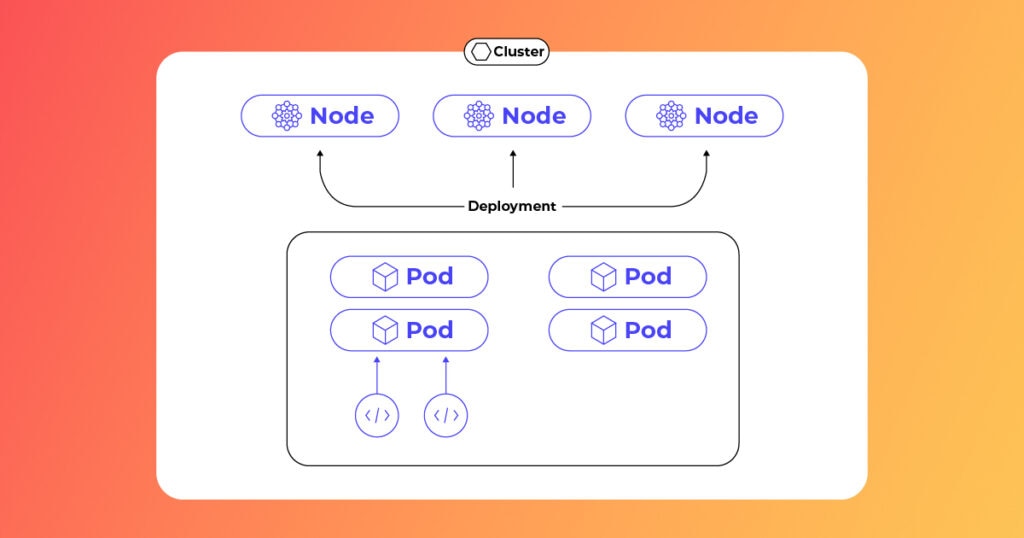
The components include:
- Container: Containers are lightweight, portable units that encapsulate application code and its dependencies. While they are designed to be isolated, misconfigurations can expose critical information, such as:
- Kubernetes API server IP addresses (KUBERNETES_SERVICE_HOST).
- Ports used by the cluster (KUBERNETES_SERVICE_PORT).
- Service credentials or access tokens inadvertently embedded in application config files.
- Pod: A pod is the basic deployable unit in Kubernetes, consisting of one or more containers that share storage and network resources. Attackers often focus on pods to explore inter-container communications.
- Service Account: Service accounts act as digital identities for pods, enabling them to interact with the Kubernetes API. Over-permissioned service accounts can be exploited to access cluster-wide resources. Attackers use service account tokens to:
- Query the Kubernetes API for cluster-wide information.
- Execute commands on other pods, gaining lateral access.
- Deployment: Deployments manage pods and ensure they run according to specified configurations. Attackers may target deployments to manipulate the application’s scale or behavior.
- Namespace: Namespaces logically partition the cluster, grouping resources for different teams or environments. By enumerating namespaces, attackers can gain a better understanding of the cluster’s organization.
- Node: Nodes are physical or virtual machines that host pods. They provide the compute power behind the cluster and may expose vulnerabilities through misconfigurations or outdated software.
- Cluster: A cluster is a collection of nodes working together as a cohesive unit, orchestrated by Kubernetes to deploy, manage, and scale containerized applications. Attackers focus on clusters to map resources and identify weak points.
The Kubernetes Reconnaissance Playbook
After gaining access to a container, whether through phishing attacks, unsecured network endpoints, or some other way, attackers deploy a series of commands and tools to perform reconnaissance:
1. Locating Kubernetes-related files
Attackers search the file system for directories containing Kubernetes data:
root@container:/# find / 2>/dev/null | grep -i kube
/run/secrets/kubernetes.io /run/secrets/kubernetes.io/serviceaccount /run/secrets/kubernetes.io/serviceaccount/namespace
/run/secrets/kubernetes.io/serviceaccount/ca.crt
/run/secrets/kubernetes.io/serviceaccount/tokenFinding these files confirms the presence of Kubernetes and reveals sensitive details like the service account token.
2. Enumerating environment variables
With the environment variables listed, attackers can find cluster-specific information:
root@container:/# env | grep -i kube KUBERNETES_SERVICE_PORT_HTTPS=443
KUBERNETES_SERVICE_PORT=443 KUBERNETES_PORT_443_TCP=tcp://10.33.144.1:443
KUBERNETES_PORT_443_TCP_PROTO=tcp KUBERNETES_PORT_443_TCP_ADDR=10.33.144.1 KUBERNETES_SERVICE_HOST=10.33.144.1 KUBERNETES_PORT=tcp://10.33.144.1:443
KUBERNETES_PORT_443_TCP_PORT=443This will reveal the Kubernetes API server’s IP, which attackers can use to query the cluster.
3. Querying the Kubernetes API
Using service account tokens, attackers can query the API to map the cluster.
Common API paths queried include:
- Namespaces: /api/v1/namespaces
- Pods in a Namespace: /api/v1/namespaces/$NAMESPACE/pods
- Nodes: /api/v1/nodes
# Get namespaces
https://$KUBERNETES_SERVICE_HOST/api/v1/namespaces/
# Get pods inside a namespace
https://$KUBERNETES_SERVICE_HOST/api/v1/namespaces/$NAMESPACE/pods
# Get service accounts
https://$KUBERNETES_SERVICE_HOST/api/v1/serviceaccounts
# Get nodes
https://$KUBERNETES_SERVICE_HOST/api/v1/nodes
# Get deployments
https://$KUBERNETES_SERVICE_HOST/apis/apps/v1/deployments
# Run a command on node curl -X POST -k -H
"Content-Type: application/json" \ -H
"Authorization: bearer
$(cat /run/secrets/kubernetes.io/serviceaccount/token)" \ https://$KUBERNETES_SERVICE_HOST/api/v1/namespaces/$NAMESPACE/pods/$POD/exec?command=/bin/bash&stdin=true&stderr=true&stdout=true&tty=true4. Network scanning
Network scans reveal accessible endpoints and open ports within the cluster:
5. Searching for docker socket files
Some containers may mount the Docker socket (docker.sock), allowing attackers to execute Docker commands and potentially escalate privileges:
root@container:/# find / -name docker.sockWhat can you do to secure your Kubernetes cluster from an attacker’s recon?
How to Defend Against Kubernetes Reconnaissance
Securing Kubernetes against reconnaissance requires a proactive and multi-layered approach that shields your cluster from potential exploits.
Start by hardening your Kubernetes configurations. Restrict access to sensitive files and directories to prevent attackers from finding the critical data they contain. Implement strict Role-Based Access Control (RBAC) policies to ensure service accounts have only the permissions they need. No more than that. This way, you significantly reduce the risk of privilege escalation.
You also want to make it a habit to audit Kubernetes API access and logs regularly. Spotting unusual activity early can stop threats before they escalate into serious incidents.
Next, focus on network segmentation to limit an attacker’s ability to move laterally within your cluster. Apply network policies to control how pods communicate with each other and with external networks.
This isolation is crucial. For example, if an attacker compromises one pod, strong segmentation prevents them from accessing others. Adding ingress and egress rules further tightens security by restricting unnecessary traffic. These measures create a controlled network environment that makes reconnaissance efforts head-scratchingly difficult for attackers.
Monitoring is another prime defense strategy. It ensures threats are identified and neutralized before they escalate. To achieve this, deploy runtime security tools that detect anomalous activity in real time. Imagine spotting unauthorized API queries or unusual system calls early on. These are subtle, early signs of recon.
You can also use technologies like eBPF, which offers comprehensive visibility into both system and network events. With eBPF, you gain the ability to monitor threats as they happen, keeping an eye on your cluster’s health without impacting performance or adding operational overhead.
Finally, turn to cloud-native security platforms for comprehensive protection. These platforms, such as the partners we work with at GlobalDots, offer continuous monitoring and real-time threat detection across Kubernetes layers 3, 4, and 7. They don’t just alert you to problems; they help you prioritize risks by cutting through the noise to highlight the most critical issues.
Additionally, their automated response capabilities let you neutralize threats quickly, ensuring your Kubernetes environment stays resilient.
Combining these proactive measures forms a rigid defense that keeps your clusters secure and operational.
In Summary…
With immense power and flexibility in Kubernetes comes unique security challenges. Attackers’ reconnaissance efforts exploit vulnerabilities and misconfigurations to map the environment and plan their exploits.
But with your newfound understanding of their recon playbook and implementing strong security practices, you can proactively defend your clusters.
This blog post was written in collaboration with Upwind






