For doing business in today’s digital era, online presence is a critical ingredient. In one form or another, at one point even your local brick and mortar shop will find a way to leverage the almighty Internet. Now, let’s say your business relies heavily on online revenue. After setting everything up, you get your first sales, things start to expand, traffic flows in, analytical data looks great, you invest in infrastructure and performance, grow further, convert, write, attend conferences… If you’re good at what you do, you’ll build a certain reputation within your market. People then start to look up to you as an authority. And the more you become relevant, the more people will look. All of which is great, but as you attract attention of those you want to reach, you and your business will certainly appear on the radar of cybercriminals as well. That moment will come sooner or later and we want you to be prepared when it comes.
Beside sheer cyber-vandalism, there are also those that will look for ways to extract profit from you and your business. To do so, they aim for where they can hurt the most – your website. If you’ve build a reputation, and revenue flows in from your online assets it is likely that your web properties will become a target for nefarious acts. There’s an increasingly popular method used by hackers – the “evergreen” among criminals, that is ransom.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.


Tweet this: When you’re good at online business you appear on cybercriminal radars
The Rise of Cyber Ransom
Over the last years cyber ransom became an increasingly popular method of digital crime. To be fair, it never disappeared, rather remained dormant only to rise and make the headlines again. Reports from tech companies like Incapsula and CloudFlare also show a rise in cyber ransom activities. A 2016 survey conducted by Corero Network Security showed that well over 80% of IT professionals expect their companies to become targets of some form of digital ransom. A more worrying fact is that 43% of them stated they believe their company could end up paying the ransom demand.
From the attacker’s perspective, it’s a matter of simple economics. It’s relatively easy for them to access the resources necessary to attack a website. Then they proceed to use the resources as a threat to a large number of companies asking for a relatively modest ransom. If only a few of them end up paying, the hacker’s efforts become highly profitable. Cyber ransom activities are simply leveraging human psychology – some people are going to pay the demanded amounts just to avoid the trouble and spending valuable time. For SMEs it gets even more frustrating as they often don’t have technical support or professionals to turn to.

Tweet this: 80% of IT professionals expect their companies to become targets of cyber ransom
The ransom demand is usually expressed in bitcoins as the cryptocurrency is impossible to track. It’s important to note that with cyber ransom threats there are no guarantees that the attackers won’t eventually go through with an attack, or try again after a certain amount of time. Next we’ll cover the two main types of cyber ransom as well as the differences and links between them:
- DDoS Ransom
- Ransomware
The Links and Difference Between DDos Ransom and Ransomware
In the realm of cyber threats, distributed-denial-of-service (DDoS) ransom attacks and ransomware hold a rather high position on the list of top IT security concerns. They are both relatively easy to launch but can end up quite expensive for the victims to mitigate. We’re talking about DDoS ransom when a cyber criminal threatens to launch a DDoS attack to bring a company’s site down unless a certain fee is paid.
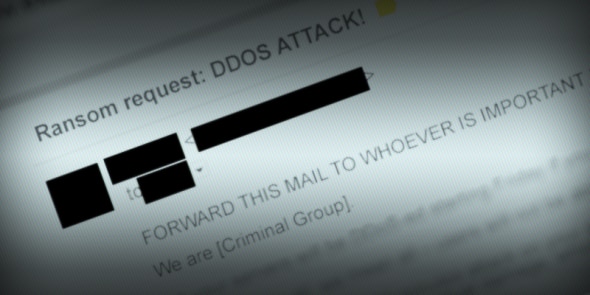
Ransomware, on the other hand, are malicious crypto-softwares whose purpose is to encrypt all files on an infected machine. The criminals then demand a ransom fee to restore access to the files. DDoS attacks are troubling enough as they are. They can result in costly downtimes, missed revenues and damaged brand reputation. However, a ransomware attack is often the more feared one. The encrypted data can end up permanently lost and it can cost a company tens of thousands of dollars in extorted money with no guarantees that the files will ever be restored. Also, ransomware can target consumers as well but will then demand a much less expensive fee.
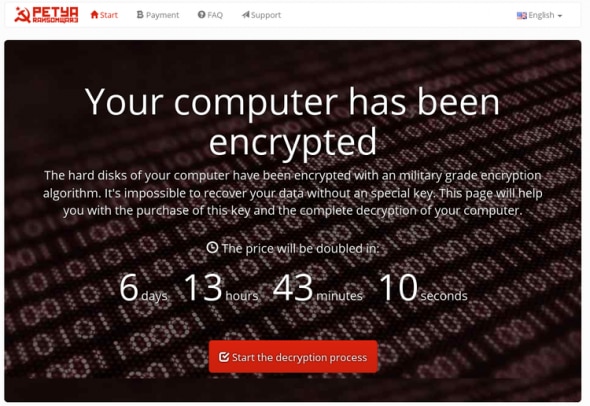
Tweet this: RANSOMWARE – DDoS is often used as a decoy for network infiltration
Although the two types of cyber ransom are executed differently, there have been cases where the two were closely linked. Hackers are getting increasingly sophisticated, and often a DDoS is used as a decoy for network infiltrations, where then a ransomware gets deployed. A low-bandwidth DDoS can be short in duration and volume, so it can easily slip under the radar of IT staff and DDoS mitigation solutions. A five minute window can be more than enough for a hacker to take down firewalls and use penetration techniques to map a network and successfully install ransomware.
What To Do
Unfortunately, most solutions focus on recovering from a cyber ransom attack, rather than preventing it. In terms of prevention, a proactive approach is the safest bet. A DDoS solution that detects even the smallest attacks could be the edge that your IT security staff needs to have a complete overview on possible network intrusions. Generally, it is strongly advised to avoid paying anything if a hacker tries to extract a ransom fee out of you. As said, there are no guarantees that your site or machines won’t be attacked anyway. Also, by paying the ransom, one could easily set himself as a preferred target for future extortions.
If you do receive a ransom note, make sure that your network is prepared for a DDoS event. Bear in mind that cyber criminals often look for vulnerable targets and may have already detected your company as such. Performing security procedures, reporting to relevant authorities and contacting security experts should minimize the potential risks of cyber ransom. At GlobalDots we recently had one such company under cyber ransom threats that approached us. By the time the ransom demand was required to be paid, they already had the best solutions and know-how in place. Needless to say, the hackers didn’t get even close to get what they wanted.

There’s another thing to keep in mind in case of cyber ransom threats. In the worst case scenario, the attackers will manage to knock your assets offline. Which is why you have to make sure you have alternative communication channels with your partners and customers. Social networks come in handy in that kind of situation, and people are often sympathetic to companies that come under attack.
Final Thoughts
Cyber crime is an ever-evolving industry, and no threat should be taken loosely. With reputation and revenue at stake, one has to be aware of all the dangers that are lurking from the dark corners of the web. Becoming a victim of a cyber ransom scheme, however, can be avoided. Having a response plan is highly recommended and it will come in handy in case things take a bad turn. What were once criminal mastermind threats, today can be achieved by kids with criminal intents and Internet access. And with new and old methods of extortion being available to a larger number of people, online security becomes an increasingly important segment when doing business. If you feel unprotected and think your online business could become a target for cyber ransom, feel free to reach out to our experts here at GlobalDots. We can help you with everything web performance and security related.






