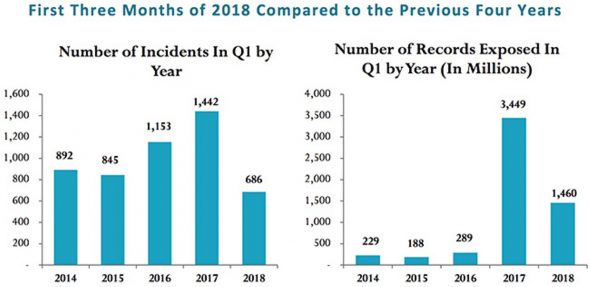
After year over year increases in the number of reported data breaches, Risk Based Security has released the results of their Q1 2018 Data Breach QuickView Report, showing the number of breaches disclosed in the first three months of the year fell to 686 compared to 1,444 breaches reported in Q1 2017. The number of records compromised in the quarter remained high, with over 1.4 billion records exposed.
Shifting tactics also appears to have played a role in the decrease. Cryptomining malware and cryptojacking has been a part of the threat landscape since early 2017. However the spike in the value of cryptocurrencies that took place in January fueled a rapid expansion into the theft of computing resources.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Beyond the number of breaches reported, many of the trends observed throughout 2017 continued to be evident in the first three months of 2018. For example, the top 5 breach types that dominated recent reports – hacking, skimming, inadvertent disclosure on the Internet, phishing and malware – all remained the top breach types into 2018.
Read more: Help Net Security






