21st April, 2021
42 Min read
DDoS Mitigation & Protections services are a crucial part of any internet business strategy. At GlobalDots we analyze, implement and maintain Security for variety of companies, from Fortune 500 to startups and small-to-medium enterprises. Since the topic is broad and many of our customers ask very specific questions, we decided to put together this resource page for everyone to learn more about DDoS attacks. We hope you’ll enjoy this article – feel free to share it with your colleagues or ask our specialists anything you want to know about your website security.
Chapter 1: What is a DoS/DDoS Attack
With the rising popularity of websites and web based applications has come a corresponding boom in the numbers, types, magnitudes and costs of attacks that specifically target the vulnerabilities of these systems. First in the category are Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. They are also the most costly cyber crimes and account for more than 55% of all annual cyber crime.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Akamai predicts that by 2020 the average DDoS attack will generate 1.5 Tbps of network traffic. Also, they warn about repetitive nature of these attacks, explaining that if your company has been the target of a DDoS attack, there’s a 1 in 4 (25%) chance that you’ll be attacked again within a 3 months and greater than a 1 in 3 (36%) chance that you’ll be targeted again within a year.
Denial of service does what its name suggests: it renders a website unavailable to users, but a successful one will hit an entire online user database. In a DoS attack, a perpetrator can use a single Internet connection to exploit a software vulnerability or flood the target with fake requests and finally cause that the site is made unavailable and prevent it from responding to requests from the legitimate users.
Or, the attack can be launched from multiple connected devices that are distributed across the internet, in an orchestrated Distributed Denial of Service attack, or DDoS.
The first step in launching a Distributed Denial of Service (DDoS) attack is to recruit an army of bots. In order to turn a computer into a bot, attackers develop specialised malware which they spread to as many vulnerable computers as possible. Malware can spread via compromised websites, e-mail attachments, or through an organisation’s network. Any users tricked into running such malware will unintentionally turn their computer into a bot, and provide attackers with an access point to their computer.
Once a computer turns into a bot, it connects to the attacker’s control circuits and it begins to accept orders from these centralised machines. The orders from the commanding control servers include directions for launching an attack from bots malware to a particular target using selected attack methods. An army of bots is named a botnet and it usually consists of thousands of bots. Any time the botnet owners want to launch an attack, they send messages to their botnet’s control servers. Any affected machine in the botnet will comply by launching a coordinated, well timed distributed attack known as the Distributed Denial of Service.
Launching a large DDoS attack is not a difficult task to carry out. One doesn’t need to create its own botnet as various pay-for-hire DDoS services are available. Anyone using such a service can launch a powerful DDoS attack.
The Business Impact is Substantial
The business impact of the DDoS attack is substantial. With outage costs averaging $100,000 per hour, a DDoS attack can cost an Internet reliant company $1 million before the company even starts to mitigate the attack.
Some of the ways in which denial of service wrecks havoc on the internet is consuming network bandwidth, overwhelming available computational resources such as disk, memory, space or processor time, disrupting configuration information, or reseting information. Not to mention reputation damage, customer agitation and legal repercussions.
Those who launch DDoS attacks can be various adversaries, such as:
Extortionists – that disable website to demand ransom money,
Exfiltrators – that steal data they can monetise, either an intellectual property or credit card data,
Hacktivists – that aim to make a political statement (Anonymous for example),
Competitors – that can disable your site to gain advantage or scrape information on your site to determine and beat your pricing.
At both the network an application layer, an array of DoS and DDoS attacks occur. There are tools that can automate the process of an attack that allow even people with no technical background to quickly and easily threaten your website.
Chapter 2: Types of DDoS Attacks
Websites and applications live outside the data center in the cloud. It is not easy to protect such perimeter, today, but there are intelligent ways to get around these problems. One is to understand the profundity of these attacks. DDoS attacks target either the network layer or the application layer.
With network-layer attacks, the goal is to send malicious packets over different network protocols in order to consume target’s available bandwidth, and clog its internet pipes. With application layer attacks, however, the goal is to consume the computing resources, CPU and RAM, that a web server has at its disposal to process requests. There are state-exhaustion attacks, as well, that target the connection state tables in firewalls, web application servers, and other infrastructure components.
Network layer attacks are the ones we read often in the media and that are attributed to the disruption service on many major sites. SYN floods, ACK floods or UDP based amplification attacks can all be classified as network layer attacks. Network layer attacks are typically measured in Gbps (gigabits per second), for the amount of bandwidth they’re able to consume per second. As they “gan-rush” the website, they are also called volumetric attacks. Arbor reported on such attacks in 2015 and described 17% of all attacks they handled as bigger than 1GBps with the average size of the attack at 804 Mbps/ 272K pps. The big ones peaked at 335 Gbps.
Application layer attacks, however, can be small and silent compared to network layer attacks, but just as disruptive, and actually more complex to handle. Application layer attacks generally require a lot less packets and bandwidth to achieve the same goal: take down a site. Application layer assaults are measured in RPS (requests per second), for the amount of processing tasks initiated per second. They are executed by bots— inhuman visitors that are able to establish a TCP handshake to interact with a targeted application.
Network Layer
Let us focus at the network layer attacks, first. Basic attacks that occur here are those of simple flooding or those of amplification. Floods take advantage of specific protocols such as TCP, ICMP, or UDP to send large number of requests to a target and overload network capabilities.
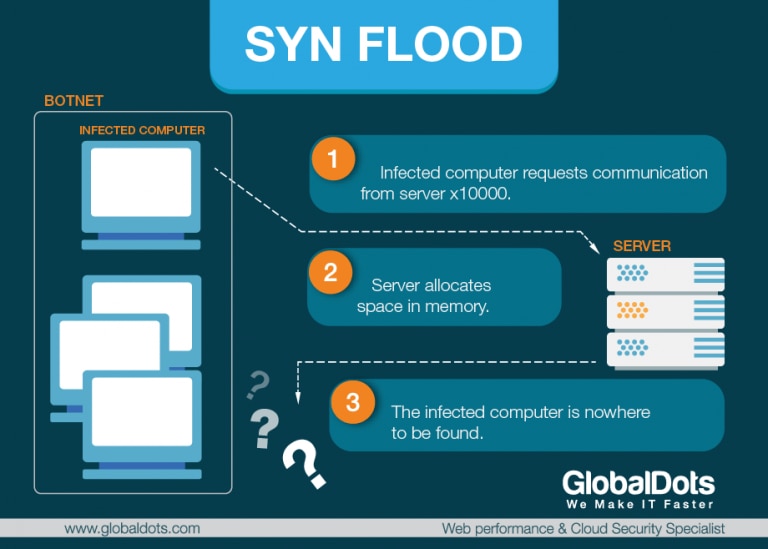
SYN Flood – SYN Flood is a popular example of a network layer DDoS attack. In its anatomy, the attacking system sends a TCP SYN request with a spoofed source IP address to a host. While the request looks legitimate, the spoofed address refers to a client that doesn’t exist so the final ACK message is never sent to the victim host.
A SYN flood DDoS attack exploits a known weakness in the TCP connection sequence (the “three-way handshake”) that usually runs like this: 1) the client requests a connection by sending a synchronise (SYN) message to the server, 2) the server acknowledges the request by sending acknowledging (SYN-ACK) message back to the client, 3) the client responds with a message (ACK) and the connection is established. In a SYN flood attack, the client will not respond to the server with the expected ACK code, or a server will send the SYN-ACK message to a falsified IP address which will not send the ACK back. The result of an attack is half open connections at the victim site.
These also bind the server’s resources so that no new legitimate connections can be made, resulting in denial of service. At that point, server will not be able to connect to any clients, whether legitimate or otherwise. The connections will be half open and consuming server resources. That’s why SYN flood attacks are sometimes also referred to as, “half-open” attacks.
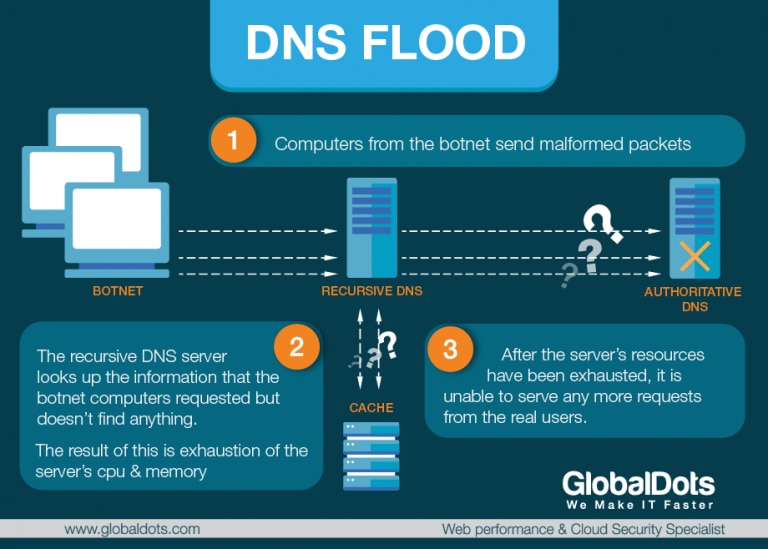
DNS Flood Attack – DNS servers are the roadmap of the internet that run a special-purpose networking software, feature a public IP address and contain a database of network names and addresses for Internet hosts. They communicate with each other using private network protocols and are organised in a hierarchy. In a DNS Flood type of a DDoS attack, an attacker targets one or more DNS servers and tries to overbear it with apparently valid traffic, overwhelming server resources and impeding the server’s ability to direct legitimate requests to zone resources (a DNS zone is a distinct portion of the domain name space in the Domain Name System).
DNS floods are symmetrical DDoS attacks that attempt to exhaust server-side assets (e.g., memory or CPU) with a flood of UDP requests, generated by scripts running on several compromised botnet machines. That’s why a DNS flood attack is sometimes referred to as a variant of a UDP flood attack. DNS servers rely on the UDP protocol for name resolution. To attack a DNS server with a DNS flood, the attacker runs a script, generally from multiple servers. These scripts send malformed packets from spoofed IP addresses. Since these attacks require no response to be effective, the attacker can send packets that are neither accurate nor even correctly formatted. The attacker can spoof all packet information, including source IP and make it appear that the attack is coming from multiple sources.
DNS Amplification Attack – Unlike DNS Floods, DNS amplification attacks are asymmetrical DDoS attacks in which the attacker sends out a small look-up query with spoofed target IP, making the spoofed target the recipient of much larger DNS responses. With these attacks, the attacker’s goal is to saturate the network by continuously exhausting bandwidth capacity. Vulnerabilities in DNS servers are exploited to turn initially very small queries into much larger payloads. This, in turn, brings the victim’s servers down.
The reflection is achieved by eliciting a response from a DNS resolvers to a spoofed IP address. During the attack, the perpetrator sends a DNS query with a forged IP address to an open DNS resolver, prompting it to reply back to that address with a DNS response. Because numerous forged queries are being sent out, and because DNS resolvers reply simultaneously, the victim’s network is overwhelmed.
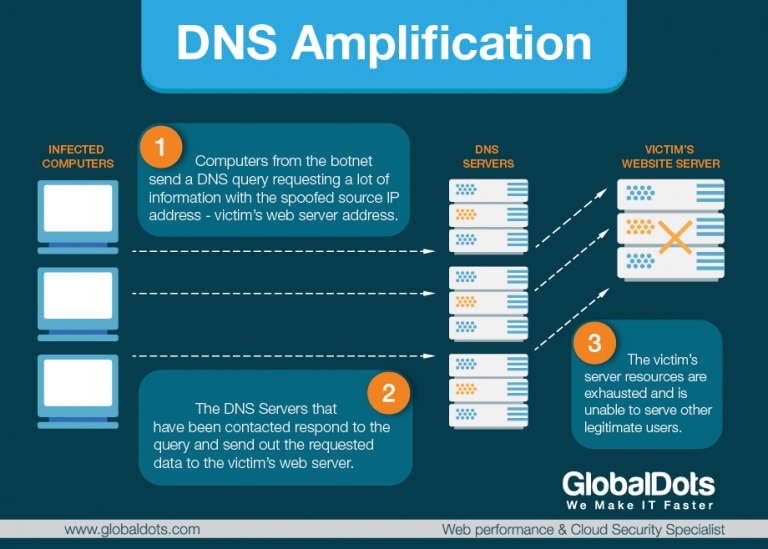
The attack is even more dangerous, if the reflection is amplified. This can be accomplished, for example, by using the EDNS0 DNS protocol extension while sending the DNS request, or by using the cryptographic feature of the DNS security extension (DNSSEC) to increase message size. Spoofed queries of the type “ANY”, that return all known information about a DNS zone in a single request, can also be used. A DNS request message, in this way, that is of some 60 bytes, can be pushed to elicit a response message of over 4000 bytes to the target server, resulting in a 70:1 amplification factor. This increases the volume of traffic the targeted server receives, and accelerates the rate at which the server’s resources will be drained. DNS amplification attacks generally relay DNS requests through one or more botnets, drastically increasing the volume of traffic directed at the targeted servers and making it much harder to track the perpetrator’s activity.
Ping Flood Attacks – A ping flood is a simple denial-of-service attack where the attacker overwhelms the victim with ICMP Echo Request, also known as pings or ping packets. This is most effective by using the flood option of ping which sends ICMP packets as fast as possible without waiting for replies. Most implementations of ping require the user to be privileged in order to specify the flood option. The attack is most successful if the attacker has more bandwidth than the victim. The attacker hopes that the victim will respond with ICMP Echo Reply packets, thus consuming both outgoing bandwidth as well as incoming bandwidth. If the target system is slow enough, it is possible to consume enough of its CPU cycles for a user to notice a significant slowdown. Additional methods for bringing down a target with ICMP requests include the use of custom tools or code, such as hping and scapy. This strains both the incoming and outgoing channels of the network, consuming significant bandwidth and resulting in a denial of service.
Ping of Death Attacks – In a POD type of attack, an attacker attempts to crash, destabilize or freeze the targeted computer or service by sending malformed or oversized packets while using a simple ping command. The ping command is usually used to test the availability of a network resource. It works by sending small data packets to the network resource. The ping of death takes advantage of this and sends data packets above the maximum limit, that is 65,536 bytes, that TCP/IP allows. Like other large but well-formed packets, a ping of death is fragmented into groups of 8 octets before transmission. However, when the target computer reassembles the malformed packet, a buffer overflow can occur, causing a system crash and potentially allowing the injection of malicious code. When fragmentation is performed, each IP fragment needs to carry information about which part of the original IP packet it contains.
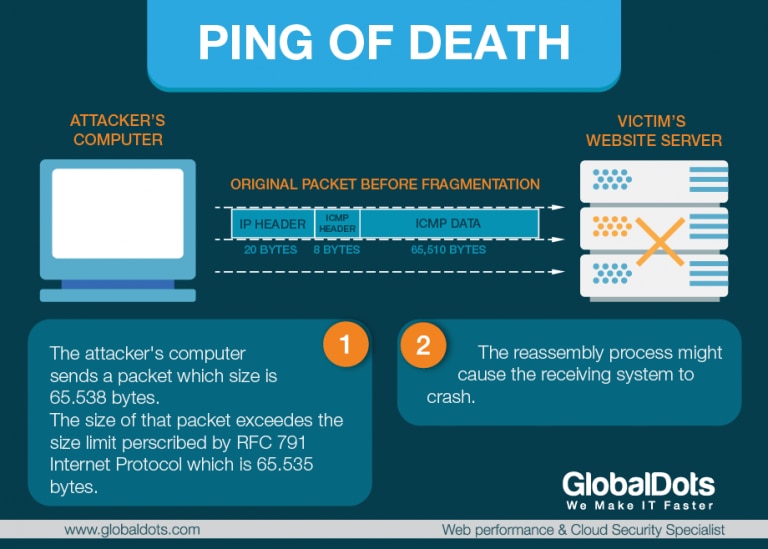
This information is kept in the Fragment Offset field, in the IP header. The field is 13 bits long, and contains the offset of the data in the current IP fragment, in the original IP packet. The offset is given in units of 8 bytes. This allows a maximum offset 65,528 ((213-1)*8). This means that an IP fragment with the maximum offset should have data no larger than 7 bytes, or else it would exceed the limit of the maximum packet length.
A malicious user can send an IP fragment with the maximum offset and with much more data than 8 bytes (as large as the physical layer allows it to be). When the receiver assembles all IP fragments, it will end up with an IP packet which is larger than 65,535 bytes. This may possibly overflow memory buffers which the receiver allocated for the packet, and can cause various problems, including denial of service. Ping of Death attacks are particularly effective because the attacker’s identity can be easily spoofed. Moreover, a Ping of Death attacker would need no detailed knowledge of the machine he was attacking, except for its IP address.
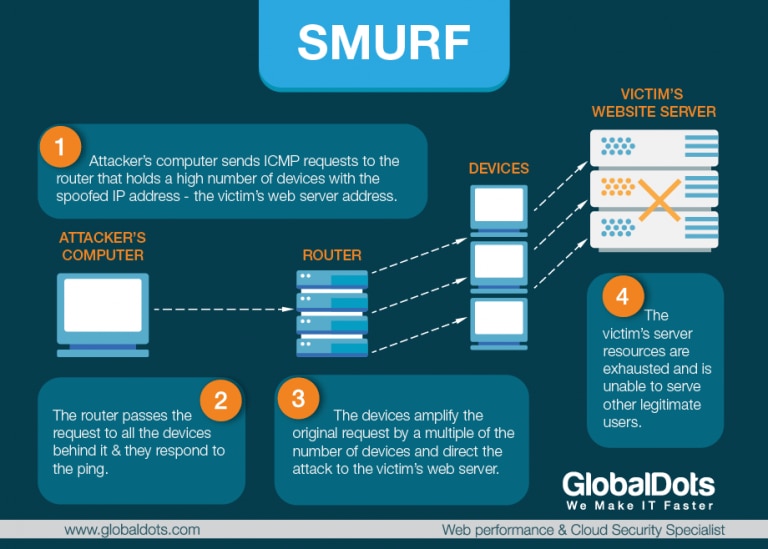
Smurf Attack – A Smurf attack is a form of a distributed denial of service (DDoS) attack that renders computer networks inoperable. The Smurf program accomplishes this by exploiting vulnerabilities of the Internet Protocol (IP) and Internet Control Message Protocols (ICMP). The attacker will send large number of IP packets with the source address faked, to appear to be the address of the victim. First, the malware creates a network packet attached to a false IP address — a technique known as “spoofing.”
Inside the packet is an ICMP ping message, asking network nodes that receive the packet to send back a reply. These replies, or “echoes,” are then sent back to network IP addresses again, setting up an infinite loop. A smurf attack amplifies a single ping 255 times and relies on misconfigured network devices that allow packets to be sent to all computer hosts on a particular network via the broadcast address of the network, rather than a specific machine. When combined with IP broadcasting — which sends the malicious packet to every IP address in a network — the Smurf attack can quickly cause a complete denial of service. It’s possible to accidentally download the Smurf Trojan from an unverified website or via an infected email link. Typically, the program will remain dormant on a computer until activated by a remote user. If a Smurf DDoS attack does succeed, it can cripple company servers for hours or days, resulting in lost revenue and customer frustration.
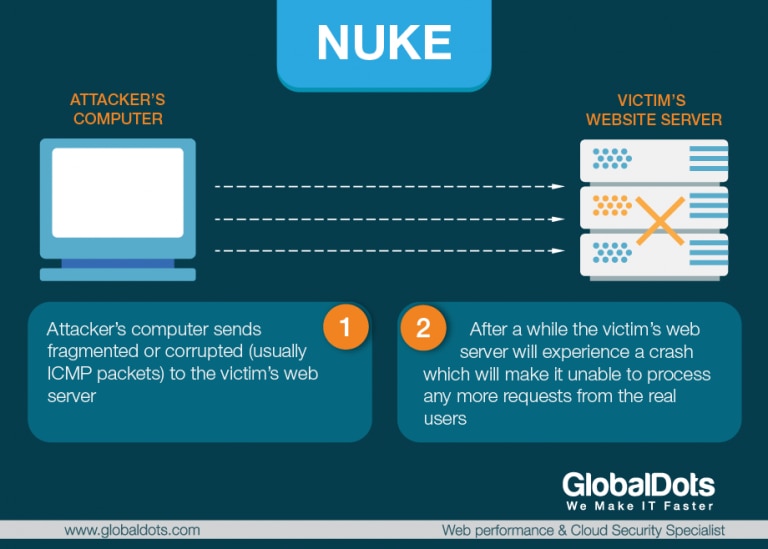
Nuke Attack – Nuke attack sends corrupt and fragmented ICMP packets via a modified ping utility to the target, repeatedly sending the corrupt data to slow down affected computer until it comes to a full stop. With enough volume, the attack can be successful. Eventually, the target machine goes offline or results in a crash or Blue Screen of Death in case of Windows. The most famous example of a Nuke attack was the 1997 WinNuke which exploited vulnerability in Windows 95. Years later, a newer version of WinNuke surfaced that affected Windows NT, 2000 and XP, but it was quickly patched by Microsoft. Nuke is an old type of DDoS attack and almost no modern operating systems are vulnerable to such an attack.
Teardrop Attack – A teardrop attack is a denial of service attack conducted by targeting TCP/IP fragmentation reassembly codes. This attack causes fragmented packets to overlap one another on the host receipt. The host then attempts to reconstruct them during the process but fails. As a result, the data packets overlap and quickly overwhelm the victim’s servers causing them to fail. This generally happens on older operating systems such as Windows 3.1x, Windows 95, Windows NT and some versions of the Linux.
One of the fields in an IP header is the “fragment offset” field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. If the sum of the offset and size of one fragmented packet differs from that of the next fragmented packet, the packets overlap. When this happens, a server vulnerable to teardrop attacks is unable to reassemble the packets – resulting in a denial-of-service condition.
Sophisticated low-bandwith Attack – Sophisticated low-bandwidth DDoS attacks use less traffic and increase their effectiveness by aiming at a weak point in the victim’s system design, that is, the attacker sends traffic consisting of complicated requests to the system. While it requires more sophistication and understanding of the attacked system, a low bandwidth DDoS attack has three major advantages in comparison to a high bandwidth attack: a) lower cost – since it uses less traffic; b) smaller footprint – hence it is harder to detect; and c) ability to hurt systems which are protected by flow control mechanisms.
An example of such attacks is an attack against HTTP servers by requesting pages that are rarely requested (forcing the server to search in the disk). Similar attacks can be conducted on search engines or on database servers by sending difficult queries that force them to spend much CPU time or disk access time. In fact, an example of such a sophisticated attack can be seen even in the classic SYN attack which aims hurting the TCP stack mechanism at its weakest point, the three-way- handshake process and its corresponding queue.
Application Layer
Tweet this: All Application layer DDoS attacks explained in detail
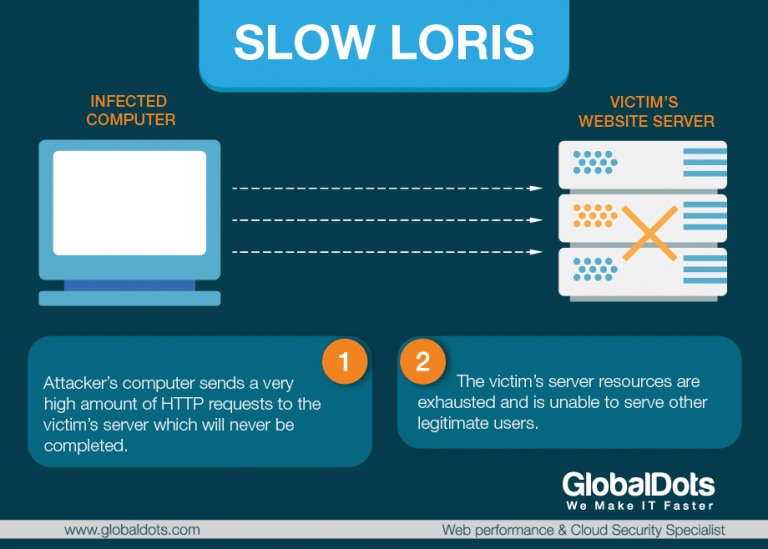
Slow Loris Attack – Slowloris is a DDoS toolkit that sends out partial requests to a target server in an effort to keep the connections open as long as possible. At the same time it does this, it sends out HTTP headers at certain intervals, which ramps up the requests, but never makes any connections. It doesn’t take long for this type of DDoS attack to take down a website. It requires minimal bandwidth to implement and affects the target server’s web server only, with almost no side effects on other services and ports. It works by opening multiple connections to the targeted web server and keeping them open as long as possible. It continuously sends partial HTTP requests, none of which are ever completed. Ultimately, the targeted server’s maximum connection pool is filled and additional connection attempts are denied.
When attacked sockets time out, Slowloris simply reinitiates the connections, continuing to max out the web server. It moves slow, but steadily, and can last for a long period of time. Designed for stealth as well as efficacy, Slowloris can be modified to send different host headers in the event that a virtual host is targeted, and logs are stored separately for each virtual host. More importantly, in the course of an attack, Slowloris can be set to suppress log file creation. This means the attack can catch unmonitored servers off-guard, without any red flags appearing in log file entries.
RUDY Attack – RUDY also known as “Are you dead yet?” or “R-U-Dead-Yet?” targets web applications by starvation of available sessions on the web server. It is a popular low and slow attack tool that is designed to crash a web server by submitting long form fields. The attack is executed via a DoS tool which browses the target website and detects embedded web forms. Once the forms have been identified, RUDY sends a legitimate HTTP POST request with an abnormally long content-length header field and then starts injecting the form with information, one byte-sized packet at a time. The information is sent in small chunks at a very slow rate, which explains “low and slow”. RUDY attack generates a slow rate and a low volume of traffic. Ultimately, it is very effective because it will exhaust the targeted server’s connection table, causing the server to crash. The RUDY tool exploits vulnerability in HTTP protocol.
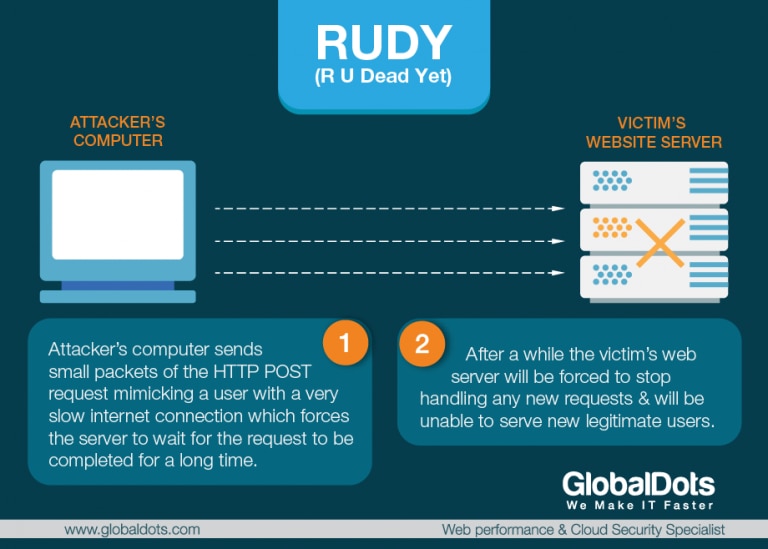
When a user fills in a web form, its web browser sends the data to a web server using an HTTP post request. When a legitimate user sends the data, it is sent over one or two packets to the web server and then the server closes the connection and moves to handle the next request. However, when an attacker uses the RUDY tool, the data from the form is broken into many packets where each packet contains only one byte of the data. The RUDY tool then sends packets in random time intervals preventing the web server from closing the connection, forcing it to wait for the request to be completed. A few thousands requests generated by the RUDY tool over several minutes will cause server to stop handling new requests. And prevent the service from legitimate users. Any website that contains web forms such as login information, feedback forms etc. is susceptible to a RUDY attack. RUDY manages to evade traditional anti DDoS mitigation systems, as it doesn’t generate volumetric traffic or high-rated packets. Each transaction is legitimate as it mimics behaviour of users with slow internet connections. Yet, it is a lethal attack on web servers.
XML Attack – An XML denial-of-service attack, or an XDoS attack, is a content-borne denial-of-service attack whose purpose is to shut down a web service or system running that service. It occurs when an XML message is sent with a multitude of digital signatures and a naive parser would look at each signature and use all the CPU cycles, eating up all resources. An XDoS attack will exhaust the system resources of the server hosting a web service when the server processes SOAP messages. Firstly, a network can be flooded with XML messages (instead of packets), in order to prevent legitimate users to network communication. Secondly, if the attacker floods the web server with XML requests, it will affect the availability of these web services. Thirdly, attackers manipulate the message content, so that the result web server gets crash. An XDOS attack mainly uses three strategies.
Other Attacks
Zero Day Attacks – Zero day attacks (or 0days) refer to all new attacks which are undisclosed, or to any previously unseen attack that common methods of DDoS mitigation may not be capable of handling. Because the attack is occurring before “Day 1” of the vulnerability being publicly known, it is said that the attack occurred on “Day 0” – hence the name. Also, because it will take an advantage of a bug or a problem (typically, of a software company) before the patch has been created.

Chapter 3: What is the Cost & How Many DDoS Attacks Happen a Day?
In the current landscape report from Incapsula, some trends are noticeable with DDoS attacks. For one, application layer attacks are growing more advanced with more and more bots that know how to pass standard security challenges. Network layer attacks are also growing more sophisticated with multi-vector attacks growing and perpetrators combining high Gbps and high Mpps attack vectors. In the case of application layer attacks, the expanded use of browser-like DDoS bots is reported. In addition, they also saw attackers exploring uncommon attack methods and uploading scripts to mount a multi-gigabit POST flood attack. In the case of network layer attacks, the trend translated into the increased use of high Mpps assaults. Further in the research it is documented that:
- Longest network layer attack lasted 48.5 hours
- Longest application layer attack lasted for 36 days
- Largest network layer attack peaked at 200+ gigabits per second
- Largest application layer attack peaked at 100,100 requests per second
- Highest attack rate for network layer attacks was 120+ million packets per second
Top targeting attacking countries in 2016 were South Korea accounting for 29.5% of the attacks, and Eastern Europe countries such as Russia with 10.8%, and Ukraine with 10.1%. Top targeted countries are US accounting for 50.3% of the attacks, United Kingdom with 9.2% and Japan with 6.7%. The following up are Ireland, Canada, Germany, France, Netherlands, Hong Kong and Australia.
It is interesting to take a look at the Digital Attack Map, a live data visualization of DDoS attacks around the globe, built through a collaboration between Google Ideas and Arbor Networks. The tool surfaces anonymous attack traffic data to let users explore historic trends and find reports of outages happening on any given day. You can select a country to view DDoS activity to or from that country, or view attacks by class, duration, or source/destination port.
Akamai’s State of the Internet infographic shows how DDoS attacks are frequented in terms of vectors with UDP fragment targeted 21% of the time, DNS 13% of the time and SYN flood occuring 10% of the time. Targeted industries are retail, gaming industries, software and technology companies, financial services, media and entertainment industries, internet and telephone companies, in that order.
According to ATLAS that uses lightweight honeypot sensors to detect and fingerprint the attacks launched by malicious sources on the Internet, 2,000 denial of service attacks are observed, on average, daily. You can observe the activity and profile of attacks here where they will sometimes read 10,000 per day.
We are witnessing a renaissance in DDoS attack tools and techniques that has led to tremendous innovation. The barrier to entry has been obliterated by new tools that enable anyone with an Internet connection to launch a DDoS attack. A 150$ can buy you a week long DDoS attack on the black market and this can, in turn, cost companies up to $1 million, depending on how internet reliant they are, and their security level standards. The cost will depend on several variables, such as the type of business you are in, the volume of your business that is online, the type of brand you are developing, the type of customers, as well as your competitors. There are even calculators that can help you come up with the mean cost in advance, relying on your annual revenue, annual revenue through online sales and the frequency of attacks in a given industry.
Another serious damage, besides the financial loss, happens along with the denial of service attack. Brand value is seriously eroded, operational costs can skyrocket, and you might have to invest in new people and technologies to manage the same risk better in the future.
Chapter 4: Tools for Launching DDoS Attacks
A botnet is a collection of devices or computers infected with malware that communicate with each other and are controlled centrally by a botmaster. The botmaster directs these machines using a command and control server – a central location from which infected machines receive instructions. Some botnets consist of hundreds of thousands, or even millions of, computers. Bots don’t always mean a bad piece of software, but they are at many times used for coordinating a DDoS attack. Botnets can be used for many different purposes as they allow a number of different computers to act in unison. In a case of DDoS attack, the so called slave machines are used to bombard a website with traffic at the same time. The botmaster can harness all of the computers to submit as many requests as possible to a single internet computer or service, to overload it and prevent it from servicing legitimate requests.
Low Orbit Ion Cannon (LOIC) sprang up as a result of a brainstorming between hackers on 4chan in 2004. They were searching for a simple and efficient tool for a future cyberwar. The existence of it became known much later to the public. In 2012, through LOIC, in an Operation Megaupload, Anonymous DDoSed the websites of UMG, the company responsible for the lawsuit against Megaupload as well as websites of US Department of Justice, US Copyright Office, FBI, MPAA, Warner Bros and HADOPI, all in one afternoon. LOIC makes mounting a DoS attack quick and simple. The software gives a potential attacker an intuitive graphical user interface. The hacker can use this interface to enter a URL, choose an attack method (TCP, UDP, HTTP), and submit the request. It will take about 60 seconds to download the tool and use it to open multiple connections to the target server and send a continuous sequence of messages.
High Orbit Ion Cannon is an upgrade to LOIC and it was developed during the conclusion of Operation Payback by the hacktivist collective Anonymous. HOIC has the ability to cause HTTP flood flow with low number of user agents with as few as 50 users being requested to successfully launch an attack, and co-ordination between multiple users leading to an exponential increase in damage. Also, instead of repeatedly sending out a single visit to a site from a fake user, HOIC targets sub pages. HOIC’s fake users visit sub pages (help, welcome pages) on a victim’s site and this tactic prevents some firewalls from recognising what is happening as an attack. HOIC also comes with a user friendly and easy to control GUI. The basic routine of the attack is to input the URL of the website, set the power option on low, medium or high. The attack is then launched by pressing the red button that says: “Fire the lazer!”.
Brobot is a name of a Russian script toolkit that was used to target US banks in 2012-2013 in the Operation Ababil. The DDoS attacks were massive and Akamai observed up to 20 banks being attacked in some weeks. Brobot, the botnet of choice for the Operation Ababil attacks is still out there and continues to present a major risk to the industry. The group behind this botnet identifies vulnerable software extensions on computers linked to high-bandwith websites and web-hosting data centres. It then compromises and controls these computers by inserting near-invisible embedded code into the extensions’ HTML. These high bandwidth botnet computers can then bombard websites with DDoS attacks as powerful as 190 Gbps.
Other tools can be seen used for specific attacks in Chapter 2 & Chapter 5.
Chapter 5: The Most Dangerous DDoS Attacks That Ever Happened
One of the first known and publicly documented DDoS attacks, although documentations vary, happened in September, 1996 against Panix, New York City’s oldest Internet service provider. A SYN flood was used to exhaust available network connections and prevent legitimate users to connecting to Panix servers. It took about 36 hours of frantic work by a globe-spanning group of Internet specialists to finally regain control of the Panix domains. In 2005, the “panix.com” domain name was hijacked again over a US long holiday weekend. It wrecked havoc for customers and Panix staff worked around the clock over the weekend to recover services after the rug was pulled out from under its business.

The next major milestone was the use of DDoS by the Electronic Disturbance Theater (EDT). Originating in the 90s, and attracting the attention of the media by the end of the decade, the hacktivist group described DDoS as akin to a “virtual sit-in.” One thing that separated them from their predecessors was their use of tools developed in-house, which allowed anyone outside of the organisation to join in. Their kit, called FloodNet, directed a user’s traffic to a target predetermined by the EDT, which included the websites of politicians and the White House. Those wishing to join the “sit-in” simply selected their target from a drop down menu, clicked attack, and waited while FloodNet automatically bombarded the offending server.

The biggest protest movement against the Church of Scientology was conducted by Anonymous in The Project Chanology that originated from the church’s attempt to remove the material from the highly-publicized interview of Tom Cruise, a prominent member of the church, on the internet in January 2008. It started with a YouTube “Message to Scientology” on January 21, 2008 and was followed by distributed denial of service attacks (DDoS), prank calls, black faxes and other methods due to their views of internet censorship implemented by Scientology. This was the result (seen on scientology.org):
In July 2009, a series of coordinated cyber attacks occurred against major government, financial websites and news agencies of both the United States and South Korea that involved the activation of botnet. The numbers of hijacked computers varied depending on the sources and include 50,000 from the Symantec’s Security Technology Response Group, 20,000 from the National Intelligence Service of South Korea, and more than 166,000 from Vietnamese computer security researchers as they analyzed the two servers used by the invaders.
In December 2010, the document archive website WikiLeaks, used by whistleblowers, came under intense pressure to stop publishing secret United States diplomatic cables. In response, Anonymous announced its support for WikiLeaks and launched DDoS attacks against Amazon, PayPal, MasterCard, Visa and the Swiss bank PostFinance, in retaliation for perceived anti-WikiLeaks behavior. This second front in the December offensive was performed under the codename Operation Avenge Assange. Due to the attacks, both MasterCard and Visa’s websites were brought down on December 8. A threat researcher at PandaLabs said Anonymous also launched an attack which brought down the Swedish prosecutor’s website when WikiLeaks founder Julian Assange was arrested in London and refused bail in relation to extradition to Sweden.

In 2011, around the Arab spring activities, the websites of the government of Tunisia were targeted by Anonymous due to censorship of the WikiLeaks documents and the Tunisian Revolution. Anonymous group took down at least eight government websites with DDoS attacks beginning on January 2. The Tunisian government responded by making its websites inaccessible from outside Tunisia. Tunisian police also arrested online activists and bloggers within the country and questioned them on the attacks. In turn, Anonymous’s website suffered a DDoS attack on January 5. Following up in 2011, during the Egyptian revolution, Egyptian government websites, along with the website of the ruling National Democratic Party, were hacked into and taken offline by Anonymous. The sites remained offline until President Hosni Mubarak stepped down. Anonymous also released the names and passwords of the email addresses of Middle Eastern governmental officials, in support of the Arab Spring. Countries targeted included officials from Bahrain, Egypt, Jordan, and Morocco.
On the weekend of February 5–6, 2011, Anonymous had successfully infiltrated the sites of HBGary Federal, the US security firm. Aaron Barr, the chief executive, stated earlier that he could exploit social media to gather information about hackers. In retaliation for Aaron Barr’s claims, members of the group Anonymous hacked the website of HBGary Federal and replaced the welcome page with a message stating that Anonymous should not be messed with, and that the hacking of the website was necessary to defend itself. Using a variety of techniques, including social engineering and SQL injection, Anonymous went on to take control of the company’s e-mail, dumping 68,000 e-mails from the system, erasing files, and taking down their phone system. The leaked emails revealed the reports and company presentations of other companies in computer security such as Endgame systems who promise high quality offensive software, advertising subscriptions of $2,500,000 per year for access to “0day exploits”. Among the documents exposed was a PowerPoint presentation entitled “The Wikileaks Threat”, put together by HBGary Federal along with two other data intelligence firms for Bank of America in December. The Anonymous group responsible for these attacks would go on to become LulzSec.

As already mentioned but we will repeat it in the timeline, in 2012, through LOIC, in an Operation Megaupload, Anonymous DDoSed the websites of UMG, the company responsible for the lawsuit against Megaupload as well as websites of US Department of Justice, US Copyright Office, FBI, MPAA, Warner Bros and HADOPI, all in one afternoon. On the day of launch, 10 high-profile government and music industry websites were reportedly brought down. By midnight on January 20th, AnonOps declared the operation a success with over 5,635 people using Low Orbit Ion Cannon to bring down the targeted sites.
In 2013, part of the Chinese Internet went down in what the government is calling the largest denial-of-service attack it has ever faced. According to the China Internet Network Information Center, the attack began at 2 a.m. Sunday morning and was followed by an even more intense attack at 4 a.m. The attack was aimed at the registry that allows users to access sites with the extension “.cn,”, and China has one of the most sophisticated filtering systems in the world.
In the same year, an Iranian hacking collective — Cyber Fighters of Izz ad-Din al-Qassam — has claimed credit for orchestrating sophisticated attacks that have overwhelmed the expensive security systems U.S. banks have put into place to keep their online banking services up and secure. The first wave of denial-of-service attacks attributed to the Cyber Fighters of Izz ad-Din al-Qassam began in September 2013 and lasted about six weeks. Knocked offline for various periods of time were Wells Fargo, U.S. Bank, Bank of America, JPMorgan Chase & Co. and PNC Bank. The second wave commenced in December and lasted seven weeks, knocking out mid-tier banks and credit unions. And a third wave of high-powered denial-of-service attacks commenced in March targeting credit card companies and financial brokerages. The attacks were a continuation of the Operation Ababil that originated in 2012. The operation was put into force as a revenge attack for an anti-Islam film that was uploaded to the Internet and, as stated by the group, insulted the prophet of Islam, Muhammed.
The theme for DDoS attacks in the first half of 2014 was volume, volume, volume, particularly prolific in the first half of 2014. Volumetric attacks occurred in more than 100 events over 100Gbps, and almost 5,800 20Gbps attacks, more than double the approximately 2,600 in all of 2013. Popular Web and mobile services Feedly and Evernote suffered the attacks. A hacker group named Lizard Squad also hit the websites of Xbox Live and PlayStation Network with DDoS attacks. Lizard Squad conducted a marketing campaign for promoting their DDoS tool, known as the Lizard Stresser, using which the group took down Sony’s PlayStation Network and Microsoft’s Xbox Live again in the year 2015 on Christmas Eve.
In 2015, Chinese activist site Greatfire.org which masks censored traffic into the country was under a sustained distributed denial of service (DDoS) attack that racked up to $30,000 a day in server costs. Website admin Charlie Smith reported that the DDoS attack was delivering 2.6 billion requests an hour. GreatFire alleged the attacks to be the handiwork of Beijing. The Cyberspace Administration of China labelled GreatFire a foreign “anti-China website”. In November the same year, the activists said authorities also used DNS poisoning against its content delivery network EdgeCast which caused mass outages and service interruptions.
In January 2016, the so-called New World Hacking group claimed responsibility for taking down both the BBC’s global website and Donald Trump‘s website. The group targeted all BBC sites, including its iPlayer on-demand service, and took them down for at least three hours on New Year’s Eve. The attack is described as what may have been the largest one in history, and it measured over 600 Gbps. Among IBM’s predictions in their recent insights relayed by various staff members, new types of DDoS attacks are confirmed to be emerging and should be prevalent during 2016.

Chapter 6: Defending Against DoS/DDoS Attacks
Against network layer attacks
Network based volumetric attacks have the effect of exhausting server resources and consuming available bandwidth. The end result is a denial of service to a legitimate user. Examples of volumetric attack vectors include User Datagram Protocol (UDP), Internet Control Message Protocol (ICMP) and other attacks that flood a network with spoofed requests. Thus, first thing to consider while defending on a network layer is to ensure enough network bandwidth to easily deal with massive amounts of traffic. If you are not able to purchase enough capacity on your own because it will go unused most of the time, many cloud services can get you access to the extra bandwidth you need to absorb the attack. Another thing is to filter the attack traffic to allow legitimate traffic and discard illegitimate one, such as excessive TCP SYN packets, floods of ICMP packets or UDP packets without application payloads.
Against application layer attacks
Application based attacks are more common than network-layer based attacks. Examples of application layer attacks include Slowloris and vulnerabilities in Web application servers and also many zero-day exploits fall into this category. These types of attacks can be harder to detect and harder to mitigate. Many application layer vulnerabilities can be avoided by so called good application “hygiene”. This means hardening applications through secure configuration and with timely updates and patches.
Throughout all the application requirements, architecture and design phases, security should be kept in mind. Security protections need to be built into software and all applications and configurations should be tested thoroughly for vulnerabilities. Using a Web Application Firewall (WAF) is highly recommended. The WAF can provide virtual patching and rules can be programmed into the WAF to protect against new vulnerabilities. WAF is like another line of defense against threats to data and against denial of service attacks. WAFs have been designed specifically to examine the contents of the application layer of IP packets. The proper deployment and management of WAF is a significant factor in whether or not they are affective in stopping attacks. We will inspect this further in the section that deals with questions you can ask your service provider about WAF.
There is no, however, one security solution for all and each company should asset its own risks to find out what fits it best, and what other security practices should be incorporated.
On-Premises Hardware
Installing and implementing on-premises devices, relying on hardware, or on firewalls installed on premises in data centres is also what you, as an organisation, can opt on. This will require large up-front capital expenditures that will have their own life cycle. For example, two-to-three years for hardware. It will also require hiring experts with the right skill set to successfully use this hardware to mitigate risks. It can be costly and difficult, but it is an option. When used in-line, protection is always on and is in use whenever an attack starts. By definition, however, on premises hardware attempts to stop a DDoS attack only after it has entered the data centre. An attack can also bring down data centre infrastructure such as routers, network firewalls and load balancers. You can combine on-premises equipment with additional cloud-based service which is known as hybrid mitigation. Ideally, a hybrid solution means on-premises devices and cloud services are fully integrated and automated. The pricing of this can still be out of reach for smaller enterprises.
Cloud based services
Cloud based services live outside data centers, as explained before, and aim to secure the traffic before it even reaches the infrastructure. Vendors will typically have several points of presence that ingest traffic bound for the customer, mitigate attacks and send clean traffic on its way to the customer. Two types of cloud based anti DoS and anti DDoS services exist: those that route malicious traffic to a centralised location where this traffic is then filtered out, and those that utilize Content Delivery Networks (CDNs) to absorb and inspect malicious traffic across a distributed network of servers in different geographical regions.
Depending on a provider, you will get either a DDoS mitigation service or website protection service. DDoS mitigation providers use private data centres and have equipment, technology and human resource to escape DoS and DDoS attacks. They are equipped with high bandwidth that can process inbound floods and keep websites available. They can actually handle all types of attacks from simple floods to those that take advantage of HTTP, FTP and other non-web applications. These services can operate as “always-on” which means that they will continually monitor your traffic for suspicious behavior and protect you from taking a big hit on the network when the DDoS attack strikes.
They provide stronger protection against costly site downtime. Alternatively, these services can operate “on-demand” which means, first and foremost, greater affordability and then, better performance. They use standard IP routing protocols to intercept incoming traffic and inspect it for anomalies. They do not, however, inspect the outgoing traffic but allow it to take its normal path. Legitimate traffic is forwarded-on after it has been identified as legitimate, and malicious traffic is – scrubbed. When using an on-demand service, your company must define when to activate this service, and contact the vendor to activate the service.
While always-on services are more expensive, and their continuous traffic inspection can, at times, degrade site performance, on-demand solutions can prove to be unable to detect attacks that occur over time and leave organisations exposed to attacks that focus on data theft or brand damage. So, both types of services have some potential advantages and challenges to consider.
You can decide on using a website protection service. In this case, providers will utilise CDNs to provide both network and application layer security for your website or application. These networks will basically sit in front of your IT infrastructure that delivers traffic from your end-user to your websites and applications. The cloud platform will examine network traffic for known attack patterns and pass only legitimate traffic to the web app. These services can mitigate attacks that are new and not seen previously. They sometimes include WAF technology and protect against additional application vulnerabilities. As CDNs are already built to handle large volume of traffic, they will make it a difficult task for an attacker to pass through. They will also offer acceleration services to improve end-to-end performance of an application and reduce performance impact. A potential problem, as there is always a smaller disadvantage to consider, is that some of these solutions will come from a smaller vendor that just doesn’t have the sufficient infrastructure required for global protection or for protection against large DDoS attacks. Also, those that do not include WAF may not provide sufficient protection against many application layer attack.
Chapter 7: How to Choose a DoS/DDoS Protection Solution
At the Network Layer
Defending against DoS attacks occurring at the network layer requires a network architecture that can absorb large blasts of traffic and that filters all traffic so that only web traffic is permitted onto the network. Every business is different and requires a different approach. These are the key questions to ask when it comes to choosing a DDoS mitigation solution:
Does it offer positive protection?
Many DDoS attacks at the network level can be stopped by only allowing legitimate HTTP traffic onto the network. The solution should drop all other non-application traffic or UDP packets without application payloads.
Does the solution absorb all attack traffic?
Not all attacks target web applications or services. Attacks sometimes attempt to sneak in throught FTP or non-web ports; look for a solution taht can evaluate all of your traffic in order to protect the site more effectively.
Is the solution always on?
Security controls only protect your website or application if they are up and running. You need to determine the availability level promised by the solution and how it’s delivered. Does the solution provider guarantee availability with a service level agreement?
Does the solution deliver scalable bandwidth to handle the volume of the attack?
A variety DDoS attack might produce the amount of traffic a site normally receives in two years. To keep the site available, the solution needs to handle all that traffic. Many cloud service providers give you access to the extra bandwidth you need to absorb an attack when you need it. Ask the provider what peak flows it can accommodate.
Does the solution stop attacks before they reach your data center?
Cloud solutions are designed to stop an attack before it ever reaches your data center. This means you need not be concerned about DDoS attacks impacting your data center. On-premises devices protect you once the attack reaches the device, which means the attack will invade your data center.
Does the solution impact performance?
Ecommerce and media streaming applications demand excellent performance. The more traffic and the more attack types, the more rules you need and the more hardware is necessary; look for a solution that’s architected for both performance and security.
At the Application Layer
Managing firewall is one of the most challenging processes in defending against application layer attacks. It requires making a lot of complex rule changes during a DDoS attack, or maybe you have decided to move these processes to a cloud based DDoS mitigation service, so you needn’t worry about it yourself. Either way, the key thing you should consider is that WAF can be targeted and overwhelmed just like any other network component. It needs to have extra capabilities and architectural protections. WAFs perform deep packet inspection of HTTP/S requests/responses and their payload to identify and protect against attacks. WAF rules examine the formats of requests and addresses and determine whether they match certain patterns that signify the attack. What you need to know is if WAF offers:
- Rules that identify known issues – attacks that come from automated tools that don’t use browsers, attacks that have been around for a long time such as SQL injection attacks…
- Rules for emerging attacks – attacks that are evolving, that are creating new rules, at least to some point
- Custom rules – also known as virtual patches that prevent the attackers from exploiting the vulnerability until you are able to put the patch in place
- Rules for situational awareness – rules to alert you about a particular activity that needn’t be blocked necessarily but it may become suspicious when combined with other actions
Even if you have decided for a cloud service that includes WAF, you can ask how flexible and comprehensive are the WAF rules. Also you should look for a WAF that provides the following types of controls:
- Black lists – a negative security model, a list of IP addresses to be blocked
- White lists – a positive security model, a list of IP addresses or IP address ranges to be allowed
- Geo blocking filters – filtering traffic from specific geographic locations to mitigate localised DDoS attacks
One of the suggestions, according to OVUM research, is also to evaluate DDoS mitigation providers against 10 enterprise criteria: 1) depth of experience, 2) provision of dedicated mitigation network capacity, 3) proven ability and global resources to mitigate the Internet’s largest and most complex attacks, 4) innovation in DDoS mitigation technology, 5) human expertise on the front lines of DDoS, 6) speed to mitigation and service level agreement guarantees, 7) mitigation at the SSL layer, 8) flexibility of service delivery, 9) threat intelligence, 10) real time network visibility.
Chapter 8: DDoS Mitigation Service Providers
According to Forrester’s report, the most significant companies that are DDoS service providers include Akamai, Cloud Flare, DOSarrest Internet Security, F5 Networks, Imperva, Level 3 and Verisign, according to their 36 criteria evaluation, and from a crowded field of competitors. Akamai, Cloud Flare, Imperva, CenturyLink and Verisign came up front as leaders.
The rise in DDoS attacks has also seen the rise of the DDoS protection service providers. As already mentioned, they will provide either an “always-on” or “on demand” service, or a hybrid service that offers the best of both worlds. All vendors in the market share core similarities, but some have advanced features over others. They differ in what attack types they defend, in response tactics and in types of protected network protocols. Also, some employ more talented sales, professional services and technical stuff and maintain good network of technology partners, resellers, and system integrators. The criteria for evaluating service providers include current offering, strategy and market presence. Also, their geographical presence is important.
For example, Akamai has points of presence and data centres in North America, Western Europe, South and North Asia. CenturyLink is present in North America, Western Europe and North Asia. CloudFlare owns servers in North America, Western Europe, Latin America, North and South Asia. They also differ in the number of data centres and servers they own in different cities across the globe. Service providers are evaluated for products they release and for the versions of these products that they release at different dates. You can read below the Forrester Wave infographic that rates these service providers according to mentioned criteria for the year 2015, below.
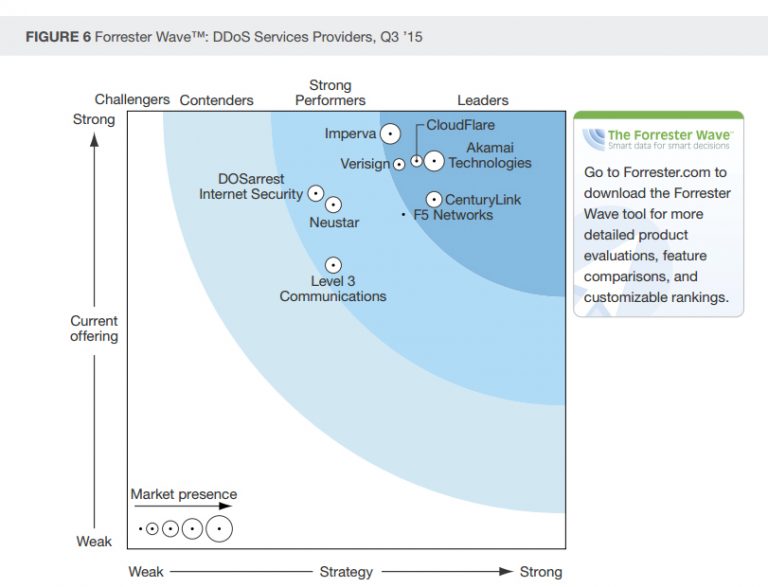
We will quickly mention services from leaders in the “wave” (Forrester Wave): Akamai, CloudFlare and Imperva Incapsula and their historic impact. We’ll also mention other industry leaders.
Akamai Prolexic
Akamai prides on a global DDoS mitigation network, comprised of six scrubbing centers located strategically around the world to protect Internet-facing infrastructures against all known types of DDoS attacks at the network, transport and application layers. Their DDoS filtering techniques, advanced routing, and anti-DoS hardware devices remove DDoS traffic close to the source of the botnet activity. For non-routed DDoS protection, as well as DNS protection, their 175,000 servers and 1,300 network locations in more than 100 countries claim to maintain website availability and performance during DDoS attacks. Akamai has successfully mitigated some of the world’s largest and most sophisticated DDoS attacks and has been active in this field since 2003. You can refer to Akamai’s infographic for suggested 4 criteria to evaluate DDoS mitigation providers.

Cloudflare
CloudFlare’s advanced DDoS protection, a service at the network edge, can be used to mitigate DDoS attacks of all forms and sizes including those that target the UDP and ICMP protocols, as well as SYN/ACK, DNS amplification and Layer 7 (application layer) attacks. CloudFlare offers the documentation that explains the anatomy of each attack method and how their network is designed to protect your web presence from threats. However, not even CloudFlare was always completely immune to attacks. In 2013, they have suffered a hit, while they were defending Spamhaus, an anti-spam organisation, against the attack that peaked at 300 Gbps and was one of the largest DDoS attacks recorded at the time. CloudFlare reckons 30,000 unique DNS resolvers have been involved in the attack against Spamhaus.

Imperva Incapsula
Imperva Incapsula service delivers a multi-faceted approach to DDoS defense, providing blanket protection from DDoS attacks to shield critical online assets. The Incapsula Website DDoS Protection solution is an always-on, cloud-based DDoS defense service that automatically detects and mitigates DDoS attacks launched at websites and Web applications. This DDoS protection service is built on top of the Incapsula Content Delivery Network (CDN) and leverages a PCI DSS compliant Web Application Firewall technology. Imperva also offers Infrastructure Protection, an on-demand security service that safeguards critical network infrastructure from volumetric and protocol-based DDoS attacks. Finally, Imperva Incapsula Name Server DDoS Protection service safeguards DNS servers from DDoS attacks. Deployed as an always-on service, it automatically identifies and blocks attacks seeking to target DNS servers, while also accelerating DNS responses. A detailed reading for each Imperva Incapsula product is offered here. Very recently, In June 2015, the Karger website was the target of a massive distributed-denial-of-service (DDoS) attack that was controlled by a botnet with zombie clients all over the world and defended against with solutions from Imperva Incapsula. Once the Imperva Incapsula web application firewall (WAF) and content delivery network (CDN) were deployed in front of the Karger site, it resulted in an immediate drop in unwanted traffic and in addition, site performance has since improved and it has not been attacked.

DOSarrest
DOSarrest is a cloud based DDoS technology service that since its inception in 2007, has developed, implemented and real world tested a wide range of proprietary methods and techniques to stop DDoS attacks. They do not (as it says on their website) rely on purpose built DDoS mitigation devices to stop all attacks. Their experience has taught them that no single DDoS mitigation device can stop all varieties of DDoS attacks in existence today.

F5 Networks
F5 Networks, Inc. is a multinational American company that specializes in application delivery networking (ADN) technology that optimizes the delivery of network-based applications and the security, performance, availability of servers, data storage devices, and other network resources. F5 is headquartered in Seattle, Washington, and has development, manufacturing, and sales/marketing offices worldwide. F5 originally manufactured and sold some of the industry’s first load balancing products. In 2010 and 2011, F5 Networks was on Fortune’s list of 100 Fastest-Growing Companies worldwide. The company was also rated one of the top ten best-performing stocks by S&P 500 in 2010.

Level 3
Level 3 Communications is an American multinational telecommunications and Internet service provider company headquartered in Colorado. It operates a Tier 1 network. The company provides core transport, IP, voice, video, and content delivery for medium-to-large Internet carriers in North America, Latin America, Europe, and selected cities in Asia.bLevel 3 is also the largest competitive local exchange carrier (CLEC) and the 3rd largest provider of fiber optic internet access (based on coverage area) in the United States. Currently, Level 3 has over 13500 employees.

Verisign
Verisign, Inc. is an American company based in Reston, Virginia, United States that operates a diverse array of network infrastructure, including two of the Internet’s thirteen root nameservers, the authoritative registry for the .com, .net, and .name generic top-level domains and the .cc and .tv country-code top-level domains, and the back-end systems for the .jobs, .gov, and .edu top-level domains. Verisign also offers a range of security services, including managed DNS, distributed denial-of-service (DDoS) attack mitigation and cyber-threat reporting.

aiScaler
aiScaler Ltd. is a multinational software company founded in 2008. It develops application delivery controllers designed to allow dynamic web pages to scale content by intelligently caching frequently requested content. aiScaler can be implemented at the customers datacenter, in a hosted environment, or through a CDN. The company maintains offices in the United States, Europe and China. They are currently stationed in Dublin.

Arbor Networks
Arbor Networks is a software company founded in 2000 and based in Burlington, Massachusetts, United States, which sells network security and network monitoring software, used – according to the company’s claims – by over 90% of all Internet service providers. The company’s products are used to protect networks from denial-of-service attacks, botnets, computer worms, and efforts to disable network routers.
Nexusguard
Nexusguard as a longtime leader in DDoS defense is at the forefront of the fight against malicious Internet attacks, protecting organizations worldwide from threats to their websites, services, and reputations. Continually evolving to face new threats as they emerge, they have the tools, insight, and know-how to protect their clients’ vital business systems no matter what comes their way.

Neustar
Neustar, Inc. is an American technology company that provides real-time information and analytics for the Internet, telecommunications, entertainment, and marketing industries, and a provider of clearinghouse and directory services to the global communications and Internet industries. Neustar is domain name registry for .biz, .us (on behalf of United States Department of Commerce), .co, and .nyc top-level domains.

Radware
Radware is an Israeli provider of integrated application delivery / load balancing and application & network security solutions for virtual and cloud data centers. It has regional headquarters in the U.S. in Mahwah, New Jersey, Asia Pacific headquarters in Shanghai, China and its international corporate headquarters are located in Tel Aviv, Israel. Radware has over 10,000 enterprise and carrier customers worldwide. Radware is a member of the Rad Group of companies and its shares are traded on NASDAQ.

Zenedge
Zenedge, unlike other Web Application Security solutions in the market, leverages patent-pending deep machine-learning capabilities to detect anomalies, dynamically alter security postures, and initiate auto-mitigation and automatic routing with minimal to zero human intervention. This allows the company to provide better cybersecurity and faster time to mitigation than traditional Cloud and on-premise cybersecurity vendors.

Staminus
Staminus, founded in 1998, provides industry-leading DDoS mitigation services to users and companies around the globe, with over 15 million IPs protected. As one of the most experienced DDoS mitigation firms in the industry, Staminus has evolved into the world’s most advanced and intuitive DDoS mitigation company.

Conclusion and Further Reading
DDoS attacks are difficult to determine. Botnets are necessary to create the attacks and the command and control (C&C) infrastructures of these botnets are designed to protect their owners and tools for denial of service attacks are becoming more available to masses. DDoS attacks cannot be fully avoided, nor can you fight them with a single method, and they are almost always successful if you do not have DDoS protection. Regular hosting environments are not built to absorb all of the extra traffic. The intensity of the packets launched at the site, however, can be lessened, and these methods are what is referred to as DDoS mitigation. The attack prevention also depends on the entire internet community to a point, and their keeping of machines up to date and using proper security tools. A distributed denial of service attack is one of the most complicated attacks to defend against today, and DDoS is what is called a denial of service attack “on steroids”. DDoS attacks have been launched in many ways throughout, and they are only getting more complex and innovative. Just as there has been major advancements in cyber security, those same innovations are also happening in the attacker world. Business continuity demands that you have a plan for when things go wrong.
Luckily, GlobalDots can help you protect your business from DDoS attacks of any size and intensity. Even with the most complex and sophisticated setups, GlobalDots can provide you with the technology stack that ensures that the most important aspects of your site are always up&running: deliverability, speed, availability, failover and web security (including web application protection, bot protection, DDoS protection and mitigation). Customers like Lufthansa, Bayer, Avast, Lamborghini and other leading brands and small-medium enterprises rely on GlobalDots services to keep their sites and applications fast & secure.
Contact us today to help you out with your performance and security needs.






