The recent two decades have changed how applications are built, delivered, and used. We used to have isolated networks with predictable entry points, but today, that has been replaced with a dynamic, interconnected web of APIs.
The consequence of this is the dissolution of the traditional security perimeter. Today, protecting a single network boundary doesn’t cut it any longer. Instead, you must secure a complex web of interactions across distributed systems, where every connection is a potential vulnerability.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

How do security teams ensure the safety of users, applications, and data in such a borderless IT environment? The answer begins with rethinking how you approach security.
How the Threat Landscape Changed in 20 Years
Enterprise applications are no longer confined to on-premises infrastructure. Critical business workloads now use a combination of on-premises systems, cloud platforms, and SaaS solutions, all held together by APIs that facilitate seamless communication between them. This has been great for user experiences, but it has also come at a cost: new, not fully understood security vulnerabilities.
One such vulnerability has to do with how APIs bypass traditional defenses, often exposing sensitive business logic to attackers. We also have microservices whose increased usage has further expanded the attack surface by creating more opportunities for attackers to exploit weaknesses and move laterally within networks.
Credential compromises add to this complexity, too, by allowing threat actors to infiltrate systems undetected. These trends have rendered outdated security strategies inadequate as they struggle to keep up with sophisticated threat actors’ new techniques.
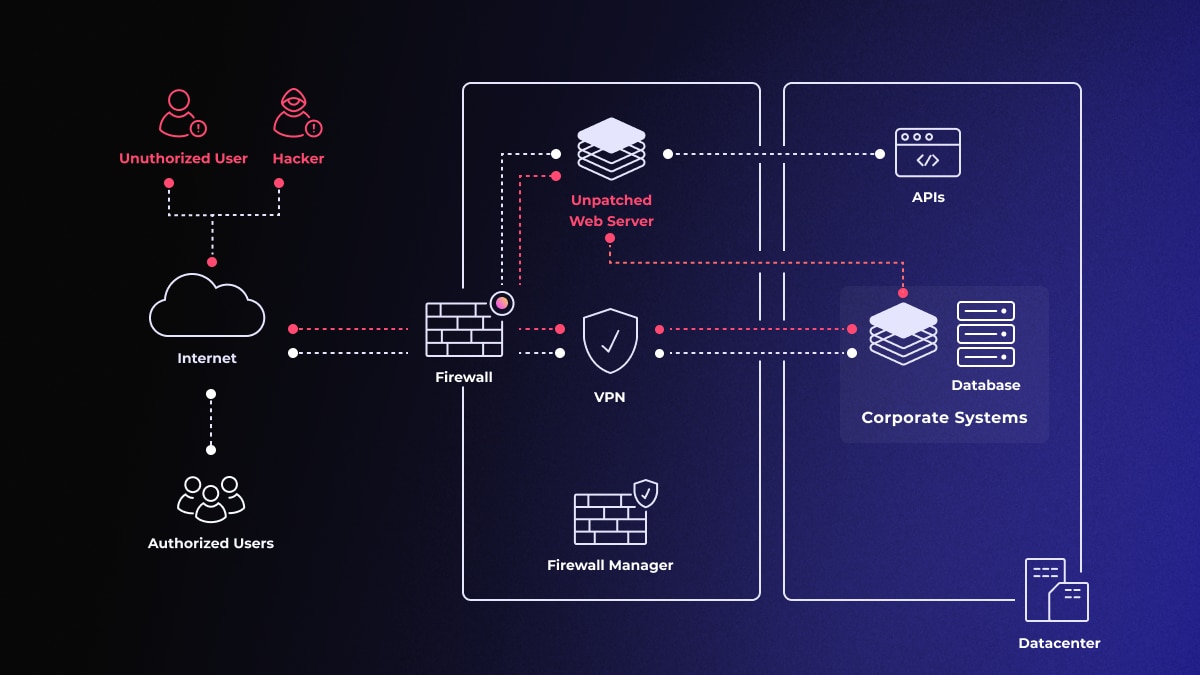
Once the security perimeter is breached, infiltrating the entire enterprise environment is possible (Source: Akamai)
Security teams haven’t been idle, though. They’ve implemented strategies like more firewall layers within the internal network. However, solving firewall issues with more firewalls only slows down the attacker. And worse, it ruins the user experience by impacting performance, not to mention the additional administrative cost for security teams.
So, what’s the solution for a perimeterless enterprise environment?
Modern Security Elements for a Perimeterless Environment
A modern security framework must focus on resilience, visibility, and adaptability. To achieve this, your security architecture should include:
1. Zero Trust Network Access (ZTNA): Traditional security often grants implicit trust to users within a network location. With ZTNA, every user, device, and application trying to access resources is given zero trust and must be continuously verified. By removing implicit trust and enforcing strict access controls, ZTNA reduces credential-based attacks and ensures access is granted only when conditions align with security policies.
2. Microsegmentation: This security technique divides workloads into smaller, isolated segments. Each segment operates independently, limiting the potential for lateral movement in case of a breach. For example, if an attacker compromises one application, they are prevented from accessing others within the network. This granular isolation safeguards critical assets and minimizes the impact of an intrusion.
3. API Security: APIs power modern applications but are vulnerable to misuse. Continuous discovery and monitoring of APIs are essential to identify shadow and zombie APIs that might be exploited. Behavioral analysis adds another layer by detecting anomalies, such as unauthorized access or data scraping, which signal misuse or malicious intent.
4. Behavioral Analytics: Machine learning establishes usage baselines and flags deviations from the baseline that signal potential attacks. For instance, an unusual spike in API calls from a single user might indicate an attempted breach.
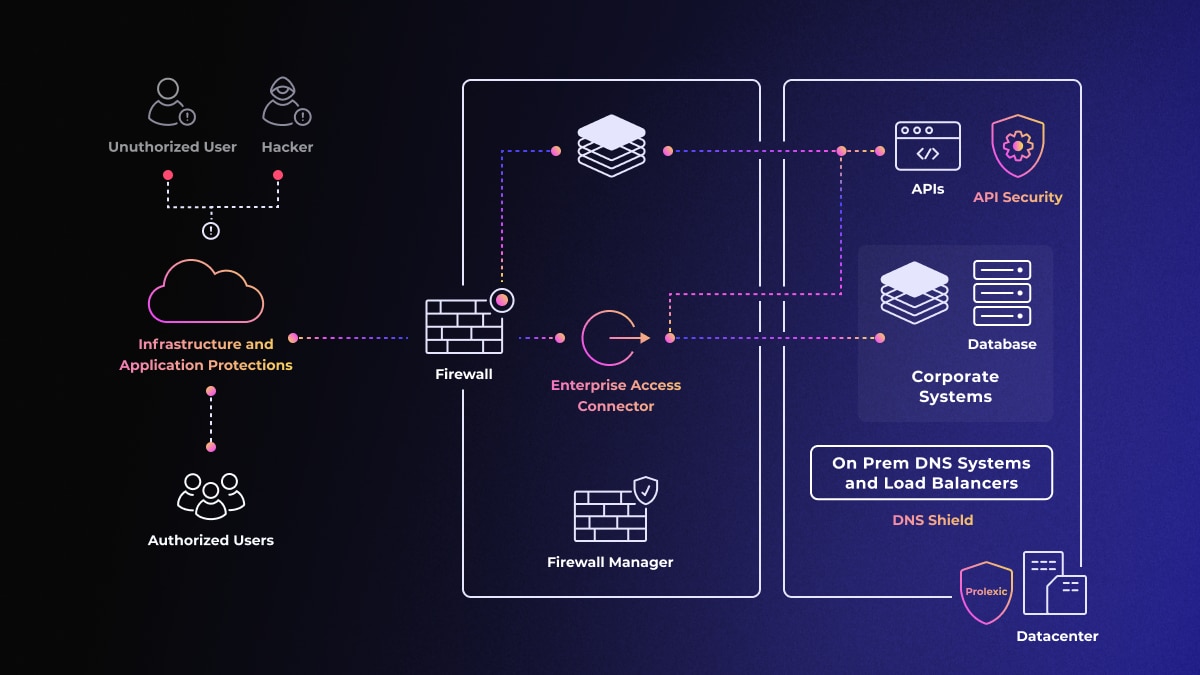
Source: Akamai
This modern security architecture depends on a robust, layered defense-in-depth strategy. ZTNA and microsegmentation work together to limit lateral movement and protect critical systems. This ensures that you’re not just reacting to threats; you expect or anticipate them, keeping your applications, users, and data resilient.
Understanding Real-World Risks
We already know that APIs bypassing traditional perimeter defenses are a problem. That’s why we have Web Application and API Protection (WAAP) platforms to offer foundational safeguards. But WAAP frequently struggles to contextualize API interactions, making distinguishing between legitimate and malicious requests a major challenge.
APIs without robust validation mechanisms leave critical business logic vulnerable to external threats. Attackers can exploit these weaknesses to bypass security controls, execute unauthorized commands, or access sensitive resources — as was the case with two California college students and internet-connected laundry machines.
Such vulnerabilities demand comprehensive protections that extend beyond the usual security. Poorly secured APIs invite misuse and pose substantial business risks that conventional defenses often overlook.
This highlights the broader risks associated with unsecured APIs. Attacks like broken Object-Level Authorization (BOLA) or data scraping subtly exploit business logic, often seamlessly blending with legitimate activity to evade detection. These tactics expose the limitations of existing tools in addressing nuanced threats.
Actionable Steps to Modernize Security
To thrive in today’s application-centric world, adopt these measures:
1. Conduct Regular Security Audits
Start by evaluating your APIs, workloads, and user access controls. Scan for shadow APIs—those deployed outside standard procedures—and zombie APIs that remain active but unused. You can use automated tools to inventory these APIs and enforce security policies. Ensure you also set up regular reviews for user access permissions to close gaps attackers could exploit here.
2. Implement Continuous Monitoring
Deploy monitoring tools that provide real-time visibility into network traffic and application activity. Anomaly detection systems within monitoring tools can flag unusual patterns, like sudden spikes in API calls or unauthorized logins. If you combine this with log analysis to correlate events across your environment, you’ll most definitely have actionable insights before issues escalate.
3. Adopt Scalable Defense Mechanisms
Ensure your defenses scale with your infrastructure to protect against volumetric attacks like DDoS. Deploy DDoS mitigation platforms that dynamically absorb massive traffic spikes and use software-defined networking (SDN) in hybrid or multi-cloud setups to centralize traffic control and isolate threats.
4. Shift Security Left
Integrate security into your development pipeline to catch vulnerabilities early. Use tools like static application security testing (SAST) and dynamic application security testing (DAST) to identify issues as you write code. For example, test APIs during development to find authentication flaws or risky business logic. Shifting left reduces risks and costs by addressing vulnerabilities before deployment.
Your Next Steps
As we embrace an application-centric IT environment, security teams must focus on proactive strategies that prioritize visibility, scalability, and resilience.
If you’d like to dig deeper into this, let us know. GlobalDots connects you with innovative tools to tackle modern security challenges head-on. With advanced capabilities, these tools enable you to extend visibility across all API traffic locations, uncover shadow and zombie APIs, and gain actionable intelligence. You can also implement role-based access control, automated response systems, and seamless integration into your IT and security stack. These features allow you to proactively detect and mitigate API vulnerabilities while scaling security measures to meet changing needs.






