Halloween horror stories from the IT trenches and war rooms
When you help the world’s most important applications work flawlessly, you tend to experience a horror story or two. Dynatrace published an article recently where they go into ten scenarios/stories which were a complete IT disaster. For the purpose of this news release here on GlobalDots, here’s one we liked the most:
This Halloween “horror story” talks about a very successful email marketing campaign in Australia which was performing so well that most of the receivers of the email clicked the link included. The problem was – it was performing way to well. So well, actually, that their website crashed. A perfect example of a great offer, but poor IT execution.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.


Read more Halloween horror stories: Dynatrace Blog
Fastly and Netflix are introducing 100G cache servers
Whether it be of an article going viral or an attack on the website, traffic spikes are an everyday occurance. 100G cache servers will help companies like Fastly and Netflix better handle them.
Fastly is a content delivery network provider that recently announced a collection of new Points of Presence (PoPs) which brings them to 40 PoPs globally. Their “Project Doughnut” is designed to scale Fastly from 40G per cache to 100G per cache. Its request processing capacity and additional network capacity is also increased because of a higher number of port-dense networks switches. This doubles the count of cache servers in any of Fastly’s PoPs.
Netflix has it’s own global CDN called Open Connect and they’ve also recently decided to switch to the new 100GbE network interface technology to serve 100G cache servers. The team over at Open Connect is pursuing various new ideas to further save memory bandwidth improving the efficiency of LRO and optimizing the new TCP code.

Read more: Bizety
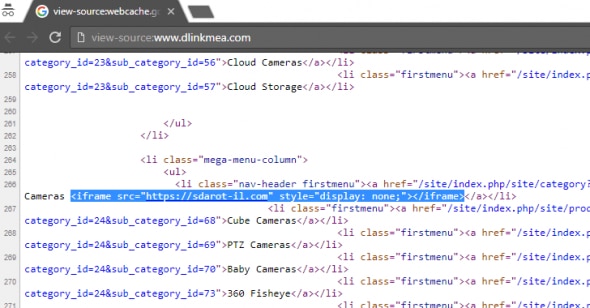
D-Link MEA site caught running a cryptocurrency mining script
Last month there was a story about The Pirate Bay and how they added a JavaScript-based cryptocurrency miner to its website without an opt-out option. This enabled them to utilize their visitors CPU power to mine Monero coins and gain extra revenue.
Now it seems D-Link’s official website for the Middle East is doing the same. Were they doing it intentionally or were they hacked is the actual question that no one has the answer to. Five days after a security company gave notice to D-Link, they redirected all traffic to their USA website without any response to the security firm.
Read more: The Hacker News
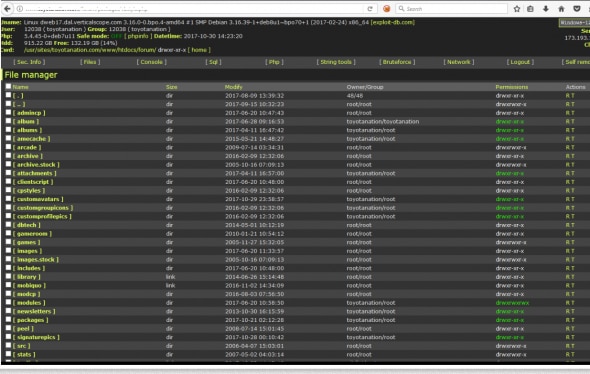
Another breach at Verticalscope will impact millions
Verticalscope is Canadian company that manages hundreds of popular Web discussion forums that cater to automotive, pets, sports and technology markets totaling more than 45 million user accounts. This breach, which resulted in 2.7 million user accounts with their appropriate names, IP addresses and email addresses being exposed is just their recent one. Previously in 2016, they’ve acknowledged that a hacking incident led to siphoning of 45 million user accounts.
The news about this breach came from Alex Holden, a security researcher who saw evidence of hackers selling access to Verticalscope and to a host of other sites operated by the company.
Read more: KrebsonSecurity
FireEye hacker arrested
In late July 2017 there was an anonymous hacker that claimed he had breached into Mandiant (a Virginia-based cybersecurity firm owned by FireEye). The hacker released 32 megabytes of data belonging to Perets, who is a Senior Threat Intelligence Analyst.
That alleged hacker has been arrested and taken into custody on Thursday by International law enforcement, as FireEye CEO Kevin Mandia informed the media.
“These attackers rarely, if ever get caught…Over my career, I have found it frustrating how little risk or repercussions exist for the attackers, who hide behind the anonymity of the internet to cause harm to good, well-intentioned people,”
– Kevin Mandia, FireEye CEO

Read more: The Hacker News






