A great majority of security flaws are introduced during development, but most aren’t found until much later, when they’re costlier to fix. That delay is precisely why application security testing (AKA AppSec testing) needs to occur early, frequently, and at multiple layers.
SAST, DAST, and IAST are designed to do just that. But too often, they’re misunderstood or bolted on without strategy, leading to noise, gaps, and wasted time.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

This guide breaks down how each method works, where it fits in your pipeline, and how to combine them into a streamlined AppSec testing strategy.
What Is Application Security Testing?
Application Security Testing (AST) refers to the suite of tools and techniques used to identify, verify, and remediate vulnerabilities in software applications. These methods target different layers of risk, from code-level flaws to runtime misconfigurations. And they are critical for reducing security debt before it reaches production.
In DevSecOps, AST shifts security left by embedding tests directly into development and CI/CD workflows. That allows developers to catch issues earlier, while also supporting post-deployment scans that simulate real-world attack behavior.
The key approaches—Static (SAST), Dynamic (DAST), and Interactive (IAST)—each bring different strengths. Used together, they provide defense in depth:
- SAST reviews code without execution
- DAST simulates attacker behavior at runtime, and
- IAST monitors actual code paths inside the running app
Other testing types, such as Software Composition Analysis (SCA) and secrets scanning, are also part of modern AST strategies, targeting open-source risk and credential hygiene.
However, implementing all of these approaches effectively requires understanding when and how to use each one. Let’s break them down.
Static Application Security Testing (SAST)
SAST analyzes your code before it ever runs. Think of it as a white-box approach: it scans source code, bytecode, or binaries for known vulnerabilities and insecure coding patterns without executing the application. It’s typically integrated early in the SDLC, often triggered on code commit or during the build process.
How SAST Works
SAST tools parse your application’s internal structure, looking for flaws like hardcoded secrets, injection vulnerabilities, or insecure API calls. Some tools use abstract syntax trees and data flow analysis to understand how data moves through the code. The more advanced ones handle multiple languages, frameworks, and even binary analysis, making them versatile for polyglot environments.
This is where “shift-left” becomes real: by embedding SAST into CI/CD pipelines, teams can catch issues before they’re buried in technical debt. Developers get immediate feedback within their IDE or PR reviews, so they can fix problems when it’s fastest (and cheapest) to do so.
Strengths and Tradeoffs
SAST is strong at identifying structural weaknesses early and supporting secure coding practices. It provides full code coverage and doesn’t need a running environment, which makes it easy to automate. That makes it ideal for regulated environments where audit trails and compliance checks are needed right from development.
But there are caveats. False positives are a known challenge. Without runtime context, SAST can flag non-issues that drain developer time. It also struggles to analyze dynamically generated code or spot flaws in third-party binaries. And because it often requires tuning to reduce noise, specialized knowledge is often needed to get the most out of it.
When to Use It
Use SAST when you want early and automated feedback, enforce secure coding standards, or need a baseline layer of security for every commit. It’s essential for catching common errors before they’re shipped, and when paired with other testing methods, it becomes part of a reliable early-warning system.
Dynamic Application Security Testing (DAST)
While SAST inspects your code from the inside, DAST flips the perspective. It’s black-box testing, that is, it scans the application as a user or attacker would, from the outside in. Its focus is on what the running app exposes.
How DAST Works
DAST tools run against live applications in staging or production-like environments. They simulate real-world attack techniques, injecting crafted inputs to see how the app responds. If they detect behavior that deviates from expected norms (like exposing stack traces, failing to sanitize inputs, or leaking session data), they flag a vulnerability.
Because it tests the app at runtime, DAST can uncover flaws that static tools miss, such as authentication misconfigurations, insecure server settings, cookie handling issues, and logic errors that only emerge under live conditions. It’s especially effective at finding injection points (SQLi, XSS), path traversal, and API misuse.
Strengths and Tradeoffs
DAST excels at identifying real-world risk. It mimics the external attacker’s view and catches security flaws that aren’t obvious from source code alone. It’s language-agnostic, which is ideal for heterogeneous environments, and integrates well into pre-prod test phases.
But DAST has its own limits as well. It can’t see inside the code, so it often fails to pinpoint where the vulnerability lives. Because of this, remediation can be slower since you’re chasing symptoms instead of root causes. Some tools struggle with authentication flows or modern app architectures like SPAs and microservices unless specifically configured.
False positives are generally lower than SAST, but still a concern. And while modern tools are improving in speed and accuracy, running large-scale DAST scans can still be slow and require tuning for complex environments.
When to Use It
DAST belongs in your QA and staging phases, especially before production pushes. It’s a must for any application with a web or API interface and complements SAST by exposing what’s dangerous in practice, not just in theory. It’s also valuable for validating the real-world effectiveness of prior fixes.
Interactive Application Security Testing (IAST)
IAST aims to give you the best of both SAST and DAST. It analyzes code in real time as the application runs, combining internal visibility with dynamic context. Think of it as a runtime debugger for security vulnerabilities.
How IAST Works
IAST tools instrument your application using lightweight agents or sensors embedded into the app server or runtime environment. As functional tests or users interact with the application, the agent monitors how data flows, which parts of the code are executed, and where dangerous behaviors might occur.
This hybrid, “gray-box” approach gives IAST an inside-out view during actual execution. It identifies the code paths being hit, understands runtime configurations, traces stack information, and watches how inputs propagate through the system. That context allows it to identify exploitable vulnerabilities with much higher precision than static or dynamic testing alone.
Strengths and Tradeoffs
The main advantage of IAST is accuracy. Because it validates findings through actual execution paths, IAST dramatically reduces false positives and often pinpoints the exact location of a vulnerability, down to the line of code. This precision accelerates remediation and prevents alert fatigue.
IAST is also developer-friendly. Integrating with QA and CI/CD workflows enables it to deliver continuous feedback during testing without requiring dedicated scans or complex setup. Many tools also provide remediation guidance directly inside the developer environment.
Despite its benefits, IAST still has three key tradeoffs. First, it requires a functioning app, so it doesn’t work during early development phases. Second, its effectiveness is limited by test coverage. If a code path isn’t triggered, the agent can’t evaluate it. And third, it introduces runtime overhead, which needs to be benchmarked, especially in performance-sensitive apps.
Tooling maturity varies, and some IAST solutions have language or environment limitations. There’s also setup complexity to consider: instrumentation must be configured properly, and tuning is often required to optimize for performance and accuracy.
When to Use It
IAST works best in QA or test environments where you already have functional or integration tests running. It’s a natural fit for DevSecOps teams who want precise, low-noise vulnerability detection as part of every build or staging deployment. And in combination with SAST and DAST, it helps round out a truly layered testing approach.
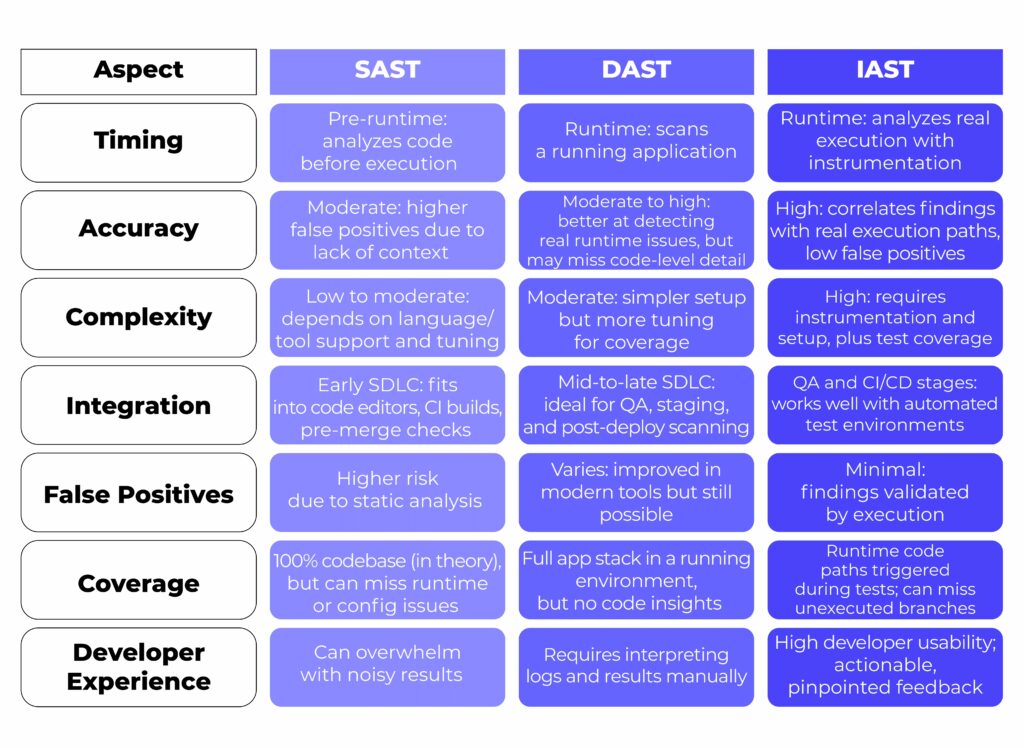
SAST vs. DAST vs. IAST: A Side-by-Side Comparison
Each application security testing method—SAST, DAST, and IAST—has strengths, limitations, and ideal use cases. The table below distills their core differences to help you evaluate which to use, when, and why.
Strategic Use of AST in DevSecOps Pipelines
To build secure software fast, AppSec testing can’t be an afterthought. It needs to be layered, automated, and tightly integrated into your CI/CD workflows.
Here’s how to make SAST, DAST, and IAST work together.
Layered Testing, Not a One-Size-Fits-All Tool
Each testing method solves a different part of the problem.
SAST is your early warning system. It scans source code and configuration before anything runs, flagging issues like hardcoded secrets, unsafe functions, or broken access controls. You catch bugs before they’re committed to your main branch, where they become harder to unwind.
DAST takes over in staging. It looks at the application the way an attacker would and probes for runtime issues—think input validation failures, session mismanagement, or unprotected APIs—that aren’t visible from source code alone. DAST is essential for surfacing vulnerabilities introduced by runtime behavior or misconfigured environments.
IAST sits between the two. It instruments your running application to observe actual execution paths during testing. This gives you near real-time insight into how user inputs interact with code and configurations, highlighting real, exploitable vulnerabilities without the false positive noise of static scanning.
Used together, these tools provide a layered defense:
- SAST during development
- IAST during QA or integration testing
- DAST just before release
This stack gives you full visibility from codebase to runtime behavior.
Secure Every Stage of the SDLC
- Code and commit: Run SAST at the commit or pull request stage to catch insecure code patterns before they merge. Tools like Semgrep and CodeQL integrate with GitHub Actions and GitLab pipelines to provide real-time feedback during code review.
- Build and test: Use IAST during QA or integration testing. As your test suite runs, IAST instruments the app to analyze live code execution and flag vulnerabilities in real time. DAST can be run pre-release to simulate external attacker behavior. Tools like ZAP, Seeker, and Contrast Assess work well here.
- Pre-production and staging: Before pushing to production, run DAST scans in a staging environment that mirrors your live stack. These scans uncover runtime issues like misconfigurations, broken authentication, and unprotected endpoints that static tools miss.
- Automate everything: Trigger SAST, DAST, and IAST scans using CI/CD tools like Jenkins, GitHub Actions, or CircleCI. Set quality gates or fail thresholds to block releases with critical findings. Feed results back to developers automatically to keep remediation cycles tight.
Example DevSecOps Stack
| SDLC Stage | Testing Type | Tools (Examples) |
| Code Commit | SAST | Semgrep, CodeQL, SonarQube |
| Build & Test | IAST | Contrast Assess, Seeker, JFrog Xray (IAST module) |
| Staging | DAST | OWASP ZAP, Burp Suite, Netsparker |
| CI/CD Automation | SAST, DAST, IAST | GitHub Actions, GitLab CI, Jenkins, CircleCI |
Choosing the Right Approach for Your Team
Security testing isn’t one-size-fits-all. The right mix of SAST, DAST, and IAST depends on how your teams work, what you’re building, and what’s at stake.
1. Team Structure and Skills
Smaller teams with limited AppSec expertise often benefit from tools that offer lower noise and more developer-friendly outputs. IAST is strong here as it reduces false positives and provides actionable, in-context feedback. SAST, while powerful early in the SDLC, can overwhelm with alerts unless carefully tuned. DAST may require more security know-how to interpret results and configure scans effectively.
If your developers are already CI/CD-savvy and comfortable owning security scans, prioritize SAST. For teams relying more on QA or AppSec specialists, DAST and IAST may offer stronger runtime insights with less configuration burden during early development.
2. Risk Tolerance and Compliance Pressure
Industries under strict regulation, such as finance, healthcare, defense, often need a mix of testing types to satisfy auditors and reduce breach risk. SAST catches compliance red flags like hardcoded credentials and outdated libraries. DAST ensures you’re not leaking data at runtime. IAST proves coverage with traceable, in-context findings.
If you’re aiming for ISO 27001, SOC 2, or PCI-DSS compliance, a layered testing approach becomes table stakes. IAST’s ability to correlate findings with real execution paths helps justify coverage during audits.
3. Language, Architecture, and Application Type
Your tech stack also plays a role. SAST is language-dependent, so multi-language applications may need multiple scanners. DAST and IAST are more agnostic, but DAST works best on traditional web applications, while IAST shines with microservices, APIs, and modern frameworks.
If you’re dealing with single-page apps, RESTful APIs, or serverless environments, IAST can observe interactions that SAST and DAST might miss. Conversely, if your app is legacy-heavy and hard to instrument, SAST + DAST may be more practical.
4. Managing Security Debt
The later you catch issues, the more expensive they are to fix. SAST pushes detection far left, enabling devs to fix vulnerabilities during implementation. DAST and IAST act as backstops during staging. Application Security Posture Management (ASPM) tools can correlate findings, prioritize risks, and prevent issues from slipping through release gates.
Embedding tools into your IDE, Git provider, and build system ensures security doesn’t become another silo. It becomes part of the developer’s daily feedback loop.
5. Budget and Scalability
SAST is generally affordable and scales well across multiple repositories. DAST may require more operational tuning and infrastructure to support concurrent scans. IAST’s agent-based model can have licensing or performance overhead, but it reduces triage time, which saves engineering cycles in the long run.
If you’re running hundreds of apps across multiple environments, investing in ASPM platforms helps consolidate tooling, cut redundant scans, and improve remediation efficiency.
How GlobalDots Can Help
GlobalDots helps organizations cut through the noise of tool overload and get real value from security testing.
We offer vendor-neutral guidance to help you select the right tools, whether you need SAST, DAST, IAST, or all three. Our team supports custom implementations across cloud-native environments, ensuring testing fits your architecture, tech stack, and team workflows.
Integration is seamless as we focus on embedding security into your CI/CD without slowing down releases. And once you’re live, we help continuously monitor your security posture, connecting testing insights to broader risk and compliance efforts.
Conclusion: Make Testing Work for You
SAST, DAST, and IAST each solve different problems. Used together, they provide broader coverage and faster feedback.
GlobalDots helps you implement them without slowing down delivery. From developer enablement to continuous tuning, we make AppSec testing practical, not painful.
Let’s talk
Schedule a consultation






