As teams ship faster in cloud-native environments, the attack surface grows just as quickly. This makes application security a moving target.
Yet most AppSec programs still feel like patchwork. Teams rely on ad hoc policies, chase compliance, or struggle to scale controls across the SDLC.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Application security frameworks change that. They give you a structure to build on, whether you’re maturing your AppSec practice or syncing engineering with security goals. This guide breaks down the major frameworks and how to put them to work in real-world pipelines.
What Is an Application Security Framework?
An application security framework is a structured set of guidelines, practices, and controls that help organizations build and maintain secure software. It maps out what to do, when to do it, and how to do it, across development, deployment, and operations.
Frameworks vary in depth and focus. Some prioritize high-level governance and maturity modeling, while others offer detailed checklists for technical controls. But the right one will depend on your team’s responsibilities, your regulatory environment, and your current AppSec maturity.
Most notable ones include:
- OWASP SAMM: A maturity model for assessing and improving AppSec programs over time. It’s modular, domain-based, and supports continuous improvement.
- OWASP ASVS: A detailed set of security controls that can be used for technical assessments, especially by developers and testers.
- OWASP LLM Top 10: A newer guidance resource targeting risks specific to large language model applications.
- ISO/IEC 27034: An international standard for integrating security into application lifecycle processes.
While each framework serves a different need, they all share a goal: to help you move from reactive patching to proactive, predictable, and measurable security.
Why Use an AppSec Framework?
Catching vulnerabilities is just one part of security in modern development. There’s also systemizing how security decisions get made, tracked, and improved over time. That’s what frameworks bring to the table.
Without a central, shared structure, AppSec will mostly rely on individual heroics or isolated tooling. But that doesn’t scale, for most teams. A proper framework will turn security into a program with repeatable processes, clear ownership, and measurable outcomes.
4 Benefits of Using a Framework
1. Standardization
Frameworks like OWASP SAMM and ASVS give teams a consistent vocabulary for discussing risk, controls, and progress. This way, it’s easier to bake into code reviews, CI/CD pipelines, architecture planning, and compliance audits.
2. Alignment with Compliance
Many frameworks already map security practices to common compliance requirements, whether that’s ISO 27001, SOC 2, GDPR, or industry-specific regulations. You don’t need to start from scratch for each.
3. Roadmap for Maturity
Instead of treating security as a binary “secure/insecure” state, frameworks like SAMM offer maturity models that show how to evolve from ad hoc efforts to fully integrated AppSec. This helps with budgeting, hiring, and justifying priorities to leadership.
4. Shift-Left Enablement
When you embed controls early in the SDLC, frameworks enable DevSecOps and proactive defense. That’s critical when software supply chains and cloud-native environments introduce new attack surfaces.
That said, you should note that using a framework doesn’t mean checking boxes. It means choosing a structure that fits your environment and using it to grow in a deliberate and transparent way.
Overview of Leading Application Security Frameworks
There’s no shortage of security frameworks out there, but not all are built for modern software delivery. Below is a breakdown of the most relevant ones for application security, especially in agile, DevOps, and cloud-native environments.
OWASP SAMM (Software Assurance Maturity Model)
Focus: Governance, strategy, and AppSec program maturity
Best for: Security leaders and AppSec program managers
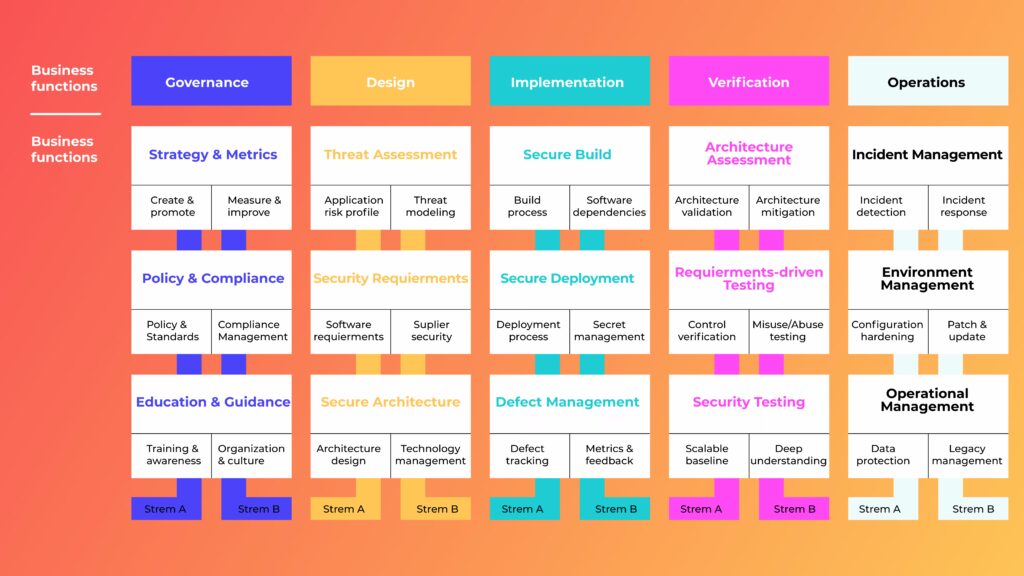
SAMM is a maturity model designed to help organizations benchmark and improve their secure software practices across 15 activities grouped into 5 business functions (Governance, Design, Implementation, Verification, Operations). Each activity has three maturity levels with defined objectives, making it ideal for long-term program building.
Why it matters: SAMM gives you a structured way to plan, measure, and evolve your security posture at the program level.
When to use SAMM: When you need AppSec governance, resource planning, and improvement tracking across teams and time.
OWASP ASVS (Application Security Verification Standard)
Focus: Technical controls and code-level security requirements
Best for: Development teams, architects, security engineers
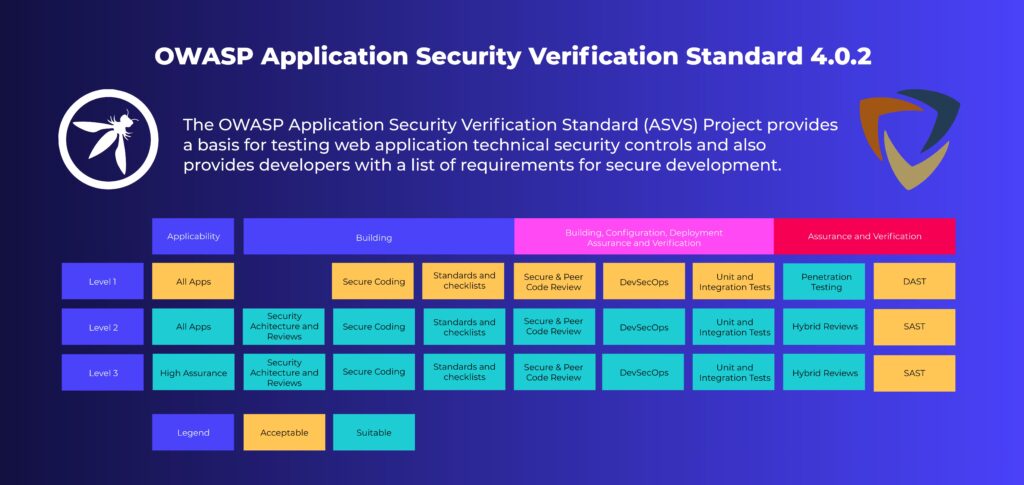
ASVS is a catalog of detailed security requirements grouped into 14 control areas (e.g., authentication, access control, data protection). These controls are structured across three verification levels (1–3), depending on application sensitivity.
Why it matters: ASVS bridges the gap between high-level policy and hands-on development. It’s useful for building security into SDLC activities like code review, test plans, and secure architecture.
When to use ASVS: When you need implementation guidance, technical checklists, or clear definitions of “done” for security.
OWASP LLM Top 10 (New)
Focus: AI and LLM-specific security risks
Best for: Teams working with generative AI features or LLM integrations
This newer OWASP project identifies the top 10 vulnerabilities in large language model use, from prompt injection to insecure plugin design. While not yet a full framework, it’s becoming essential reference material for AppSec in AI-driven applications.
When to use OWASP LLM: When evaluating risk in AI-powered features, especially customer-facing ones.

NIST SP 800-53
Focus: Broad security and privacy controls for federal and enterprise systems
Best for: Compliance-heavy orgs (e.g., government contractors, regulated industries)
NIST 800-53 is a control catalog that covers everything from application security to physical access. It’s comprehensive, but can be overwhelming without tailoring. Many orgs use it as a backbone for compliance-driven security architecture.
When to use NIST 800-53: When aligning to federal standards or building a unified control baseline across business units.
Comparison Table: AppSec Frameworks at a Glance
| Framework | Primary Focus | Best For | Maturity Modeling | Control Coverage | Implementation Level |
| OWASP SAMM | Governance, program maturity | CISOs, AppSec leaders | ✅ | Moderate | High-level strategy |
| OWASP ASVS | Technical control verification | Devs, engineers, architects | ❌ | Deep | Code/config level |
| OWASP LLM | AI-specific risks | AI-focused development teams | ❌ | Narrow (AI) | Architecture/design |
| NIST 800-53 | General security & compliance | Government, regulated sectors | ❌ | Broad | Organizational/system |
Frameworks in Practice: Integrating Security into Development
Understanding a framework is one thing; operationalizing it in fast-moving engineering environments is another. The good news is today’s frameworks are built to complement how modern teams already work.
Here’s what putting them into practice looks like.
Secure SDLC: Bake It In, Don’t Bolt It On
Frameworks like SAMM and ASVS are most effective when mapped to your existing SDLC. That means:
- Aligning maturity objectives (SAMM) with planning and sprint cadences
- Integrating verification controls (ASVS) into coding, review, and QA workflows
- Tying threat modeling and architecture reviews into the design phase, not just the tail end
This adds structure (not friction) so secure development becomes part of how things get done, not a separate checklist.
Shift-Left and Shift-Right: A Full-Lifecycle Mindset
Modern frameworks support both early-stage and post-deployment security:
- Shift-left: ASVS requirements embedded in developer IDEs, pre-merge checklists, or IaC templates
- Shift-right: SAMM’s “Operations” function maps to logging, monitoring, and incident response
- Drift detection: OWASP SAMM 2.0 encourages tracking deviation from expected secure states, especially in infrastructure and CI/CD
All these help your team catch issues before production and respond with confidence after deployment.
Developer-Centric Threat Modeling
ASVS and SAMM don’t dictate one threat modeling method, but they both recognize its importance.
For developer-first adoption, teams often use lightweight methods like STRIDE or abuse case brainstorming. These can be adapted into sprint planning, with security leads or champions guiding the conversation. The idea is to encourage design-time thinking about misuse and attack vectors without requiring formalized workshops every time.
Pro tip: OWASP Threat Dragon and Microsoft Threat Modeling Tool are two dev-friendly options that integrate into agile workflows.
Tooling Alignment: Make the Framework Work for You
The most effective implementations map security controls and maturity goals to real tools already in use, like:
- SAST/DAST/SCA tools for code and dependency analysis
- Secrets scanners and CI pipeline linters
- IaC policy enforcers
- Policy-as-code platforms (e.g., OPA, Rego) for repeatable control checks
- Developer portals or internal wikis for housing ASVS control mappings and secure coding standards
Frameworks do not replace your tools. Instead, they’re the blueprint that tells you where tools fit, what gaps remain, and how to drive improvement over time.
How to Choose the Right Application Security Framework
There’s no single “best” AppSec framework—only the one that fits your organization’s structure, workflows, and risk posture.
Choosing well means understanding what each framework is optimized for and being honest about your team’s current capabilities and needs. Here’s how to break down that decision.
1. Start with Your Primary Driver
Why are you seeking a framework in the first place?
- To align with compliance or audit requirements? Frameworks like ISO/IEC 27034 or NIST 800-53 offer more formal structures that resonate with auditors and regulatory bodies.
- To build internal maturity over time? OWASP SAMM is purpose-built for this, giving you a detailed map of where you are now and what ‘better’ looks like.
- To harden applications through practical security controls? ASVS is highly actionable, technical, and perfect for teams that want concrete, testable requirements.
- To educate developers and standardize secure coding? Consider using ASVS paired with an internal secure coding playbook mapped to its levels.
Clarify your goal, then shortlist frameworks built to serve it.
2. Assess Your Team’s Structure and Resources
A robust AppSec framework is only valuable if your team can adopt and sustain it.
- Do you have a dedicated security team? You’ll likely benefit from SAMM’s governance and process maturity modeling.
- Is security embedded in engineering teams, or still siloed? ASVS can help create shared language and expectations across roles.
- Do you have the cycles for regular assessments and maturity scoring? SAMM involves structured self-assessments—real value, but also a time commitment.
- Is the goal better visibility across a large org or multiple business units? SAMM or ISO/IEC 27034 may be better suited than purely technical checklists.
Choose something your teams can realistically implement, then grow into.
3. Consider Integration with Your Tech Stack
Some frameworks lend themselves more easily to automation.
- Need API security coverage? ASVS includes specific verification items tailored to modern API and microservices architectures.
- Using GitHub Actions, GitLab CI, or Jenkins? You can map ASVS controls or NIST control families to pipeline gates.
- Rely heavily on Infrastructure as Code? Use SAMM’s “Secure Build” and ASVS’s deployment controls to guide policy-as-code rulesets.
Your choice should reinforce, not fight against, how your teams already ship software.
4. Match the Framework to Your Risk Appetite
Some organizations are more risk-tolerant than others, often by necessity:
- Highly regulated industries (finance, healthcare, defense) should consider NIST 800-53 or ISO/IEC 27034 alongside OWASP frameworks.
- Startups and fast-moving teams may prioritize ASVS for lightweight adoption, then layer in SAMM as they scale.
- Multi-cloud or hybrid orgs need a framework that’s platform-agnostic—SAMM’s process lens is often better than hardcoded tech assumptions.
Let your threat profile and governance obligations guide depth and formality.
5. Don’t Overcommit; Start Small and Layer
You don’t need to implement an entire framework overnight. In fact, you shouldn’t.
Instead:
- Use ASVS Level 1 as a secure-by-default baseline for all projects.
- Run a SAMM assessment on one product team to benchmark maturity and identify low-effort wins.
- Align sprint-level tasks with a single domain (e.g., Secure Design or Secure Deployment).
- Map controls to existing workflows, not theoretical ones.
You can expand from there with evidence, buy-in, and iterative wins.
Implementing an Application Security Framework
Selecting a framework is only the beginning. Implementation is where AppSec programs succeed or stall.
Too often, frameworks are introduced as top-down mandates, disconnected from the day-to-day workflows of development and operations teams. A successful rollout requires buy-in, thorough planning, and seamless integration into existing engineering workflows.
Here’s how to approach it strategically.
1. Get Cross-Functional Alignment Early
Rolling out a security framework affects engineering, security, compliance, and business teams. Each has different priorities. Getting alignment from the start helps avoid friction later. A shared kickoff with clear goals and ownership makes it easier to set expectations before you start enforcing controls.
2. Start with a Pilot, Don’t Roll Out Org-Wide Yet
Don’t roll out org-wide on day one. Pilot the framework with a team that has real security needs and is open to iteration. This lets you validate assumptions, tune processes, and build internal proof before scaling to the rest of the org.
3. Map Framework Domains to Your SDLC and Toolchain
Map framework domains (like “Secure Architecture” or “Security Testing”) to existing checkpoints in your dev lifecycle. Automate where possible, whether that’s tagging Jira tickets, adding pipeline gates, or exporting logs for compliance. The smoother it fits into daily work, the more likely it is to stick.
4. Communicate Progress, Not Just Rules
Policy mandates won’t drive adoption. Visible progress will. Use metrics that matter to engineers and execs alike: reduced critical bugs in prod, time saved via automation, or stronger maturity scores over time. Make the journey collaborative and show where it’s working.
5. Plan for Ongoing Tuning
Your architecture, risks, and team structures will change. So should your framework alignment. Set a cadence for reassessment and updating controls. Pull in new teams gradually and share lessons learned. The goal is a living, evolving system, not a static checklist.
Measuring Success
Framework adoption is a long-term investment in maturity. But without clear indicators, it’s hard to know if you’re making progress.
Start with a maturity assessment, such as the OWASP SAMM model, to baseline where you are and identify where to grow. Reassess periodically to track improvements and uncover gaps as your architecture and team evolve.
Complement this with operational metrics: time to remediate vulnerabilities (MTTR), security coverage in CI/CD, incident frequency, and number of policy exceptions. These indicators help translate abstract security goals into tangible performance improvements, making it easier to maintain momentum and justify continued investment.
How GlobalDots Can Help
Application security frameworks only work when they’re practical. That’s where GlobalDots comes in. We help translate models like OWASP SAMM and ASVS into workflows your teams can actually follow.
We help you choose the right framework for your architecture, risk profile, and delivery cadence. From custom workshops to integration support, we align controls with your existing SDLC and toolchain, including CI/CD pipelines, IaC scans, SCA, and more.
Our approach goes beyond implementation. We stay engaged to automate compliance evidence, track maturity, and adapt the framework as your environment changes.
Security isn’t static, and your framework shouldn’t be either.
Conclusion
Application security frameworks bring structure to the chaos, clarifying ownership, aligning teams, and anchoring security in day-to-day practice.
But they’re only effective when they move beyond theory.
Let’s talk
Schedule a consultation and see how we can help turn your AppSec program into a business advantage.






