APIs are now the top attack vector in enterprise apps. In 2024 alone, breaches tied to APIs cost an average of $4.88 million, and that number is rising fast.
Attackers exploit gaps in API authentication, input validation, and outdated endpoints to compromise systems. Legacy controls no longer suffice, and the OWASP API Top 10 outlines risks that most organizations still miss.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

This checklist provides a clear and practical way to assess your API posture quickly. Use it for internal audits, CI/CD hardening, or onboarding. It’s built for security teams that need to act, not just plan.
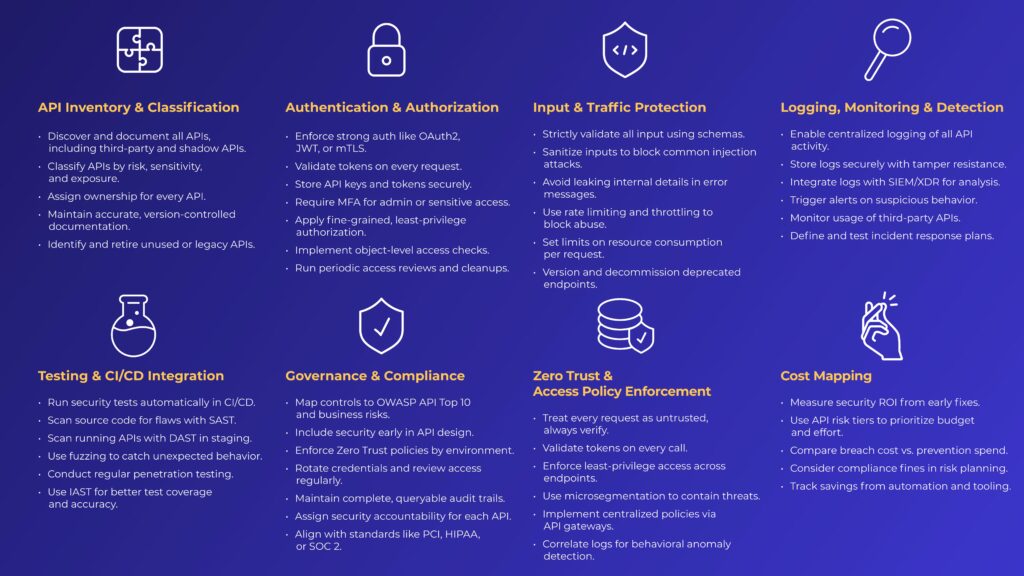
1. API Inventory & Classification
- All APIs are identified and documented: Use automated discovery tools to surface known, unknown (shadow), and deprecated APIs. Include third-party and partner APIs.
- Each API is classified by risk and environment: Tag APIs based on data sensitivity, function, and exposure (internal, public, partner). Prioritize high-risk endpoints for audit and monitoring.
- Ownership is clearly defined: Assign each API to a product or engineering owner to ensure accountability for maintenance and security posture.
- Documentation is accurate and machine-readable: Use OpenAPI/Swagger specs. Include auth methods, input schemas, rate limits, and error definitions. Keep versioned and under source control.
- Zombie APIs are identified and sunset: Monitor usage to flag inactive or legacy endpoints. Securely decommission them before they become attack vectors.
2. Authentication & Authorization
- Strong authentication protocols enforced: Require OAuth 2.0, JWT, OpenID Connect, or mTLS for all endpoints. Don’t allow custom or basic auth.
- Tokens validated on every request: Check for signature, issuer, and expiration. Use short-lived tokens with refresh workflows.
- API keys and tokens stored securely: Use vaults like AWS KMS or HashiCorp Vault. Never expose secrets in frontend code or repos.
- MFA required for admin or sensitive APIs: Support TOTP, FIDO2, or SMS-based MFA to reduce account takeover risk.
- Fine-grained authorization per endpoint: Apply RBAC/ABAC with least-privilege defaults. Scope access by role, method, and data sensitivity.
- Authorization logic includes object-level checks: Prevent broken object-level authorization (BOLA). Users must not access objects they don’t own, even if they can guess the ID.
- Access reviews are run regularly: Audit access permissions quarterly. Remove stale privileges, unused service accounts, and orphaned tokens.
3. Input & Traffic Protection
- Strict input validation on all endpoints: Validate query strings, headers, and payloads using schema definitions (e.g., JSON Schema). Reject unexpected types, formats, or keys.
- Sanitization applied to all inputs: Strip or neutralize dangerous content to prevent XSS, SQL injection, command injection, XXE, and similar attack vectors.
- Error responses don’t leak internals: Avoid exposing stack traces, library versions, or sensitive data. Standardize error messaging.
- Rate limiting and throttling configured: Apply per-user or per-key rate caps. Use burst detection and exponential backoff to mitigate brute-force and DoS attempts.
- Resource consumption limits enforced: Protect against abuse by setting ceilings on payload size, CPU, memory, and concurrent requests. Flag anomalies.
- Deprecated endpoints versioned and sunset: Notify users early. Track usage to ensure decommissioning doesn’t break clients. Remove once inactive.
4. Logging, Monitoring & Detection
- Centralized logging is enabled: Capture request data, headers, auth attempts, and error codes. Mask PII and secrets before writing logs.
- Logs stored securely with tamper protection: Retain logs per compliance policy (typically 6–12 months). Use append-only storage or WORM-compliant services.
- Integrated with SIEM or XDR tools: Send logs to systems like Splunk, Datadog, or Elastic. Normalize and enrich logs to support threat detection.
- Automated alerts for abnormal activity: Trigger alerts on spikes in traffic, repeated auth failures, or unexpected IPs or geographies.
- Monitoring includes third-party API usage: Treat external APIs as potential risk surfaces. Track their usage, error rates, and behavior changes.
- Incident response procedures defined: Document response plans for common attack types. Assign roles and run periodic simulations.
5. Testing & CI/CD Integration
- Security testing is integrated into CI/CD: Run security checks on every commit or build. Block releases on critical issues.
- Static analysis (SAST) scans source code: Catch hardcoded secrets, injection flaws, and insecure patterns before deployment.
- Dynamic testing (DAST) scans running APIs: Test exposed endpoints for XSS, SQLi, auth bypass, and misconfigurations in staging/pre-prod.
- Fuzz testing detects edge-case handling failures: Send malformed or unexpected inputs to uncover logic or parser issues missed by other tools.
- Penetration testing performed regularly: Simulate real-world attacks on high-risk APIs. Cover business logic, chaining attacks, and rate abuse.
- Interactive testing (IAST) used where possible: Combine static and dynamic insight for better context and lower false positives.
6. Governance & Compliance
- Each control mapped to OWASP API Top 10: Use the latest edition as a baseline for policy, testing, and reporting. Prioritize risks like BOLA, broken auth, and excessive data exposure. In addition, extend the audit to include controls tailored to your specific API use cases, data sensitivity, and business logic.
- Security requirements built into the design phase: Include threat modeling, misuse case reviews, and secure-by-default design patterns.
- Zero Trust enforced by environment: Apply least privilege, microsegmentation, and continuous validation per API environment (dev, staging, prod).
- Access reviews and key rotations scheduled: Rotate secrets and credentials regularly. Review access scopes quarterly, especially for third-party integrations.
- Audit trails maintained and queryable: Ensure every action — especially around auth, token use, and privilege escalation — is logged and attributed.
- Security ownership assigned and tracked: Designate accountable teams for each API’s security posture and compliance status.
- Compliance frameworks aligned: Map security measures to frameworks like PCI DSS, HIPAA, GDPR, or SOC 2 based on your industry and exposure.
7. Zero Trust & Access Policy Enforcement
- Every request is treated as untrusted by default: Apply Zero Trust to all APIs, regardless of source — internal or external.
- Token validation happens on every request: No assumptions based on session or IP. Re-authenticate continuously.
- Least-privilege access is enforced across endpoints: Scope permissions narrowly. Use RBAC/ABAC at method and data level.
- Microsegmentation limits lateral movement: Isolate API resources by function, environment, or data domain. Contain breaches before they escalate.
- API gateways used as policy enforcement points: Centralize controls like rate limiting, mTLS, and authentication. Layer with additional security, because gateways alone aren’t enough.
- Requests logged and correlated for anomaly detection: Enrich API logs with identity and behavior metadata for cross-system threat analysis.
8. Cost Mapping
- Security ROI tracked over time: Measure how early fixes in CI/CD reduce breach risk and remediation cost downstream.
- API risk tiering guides budget and effort: Allocate pentests, manual review, and monitoring based on risk level, not just usage volume.
- Incident costs vs. prevention investments analyzed: Weigh the financial impact of a breach ($4.88M avg. in 2024) against the cost of testing, training, and tooling.
- Compliance penalties and audit prep considered: Account for fines (GDPR, PCI) and reputational damage in your risk model.
- Automation efficiency quantified: Track time saved by automating scanning, key rotation, and access reviews. Factor that into headcount and roadmap planning.
Conclusion
API security is a board-level issue with real financial stakes. Attackers often exploit gaps faster than teams can patch them.
This checklist helps you identify those gaps before they become incidents. Use it as a standing reference during audits, threat modeling, onboarding, and CI/CD hardening. Print it. Share it. Embed it into your process.
Need help applying it? GlobalDots offers free API security posture audits and secure API design workshops for teams building high-scale, high-risk systems.






