In January 2024, a misconfigured API exposed 650,000 private messages. These included passwords and internal communications. No exploit chain. No zero-day. Just a public-facing endpoint with no authentication.
This wasn’t an isolated incident. From T-Mobile and Twitter (now X) to Kronos Research and the US Treasury, attackers have consistently used APIs as entry points. They bypass traditional defenses by exploiting gaps in authentication, input validation, and inventory control.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

An API security audit is one of the few defenses built to catch these issues before attackers do. It inspects the full stack: your endpoints, tokens, configurations, and business logic. Done right, it surfaces silent failures and policy drift that routine scans often miss, and turns visibility into action.
What is an API Security Audit?
An API security audit is a structured assessment of your API surface, how it’s built, secured, and exposed. Its goal is to uncover vulnerabilities that traditional app security often misses.
A proper audit combines static and dynamic testing, config inspection, access review, and runtime analysis. It evaluates whether your API endpoints enforce authentication and authorization correctly, validate input reliably, and follow secure-by-design principles.
Audits typically follow frameworks like the OWASP API Security Top 10 or internal security policies. It finds flaws and maps them to real-world risk, prioritizes based on impact, and defines remediation steps.
At its core, an API audit is about answering a simple question: Can your APIs be trusted to handle the data and permissions they expose?
Why Audit APIs?
APIs are the weakest link in many security programs. Auditing isn’t optional anymore. It’s a response to real threats and operational complexity.
- Compliance pressure is rising: Regulations like PCI DSS 4.0, HIPAA, GDPR, and SOC 2 now include API-specific controls. Audits help prove encryption, access control, and logging are properly enforced and that documentation is current.
- Zero Trust requires validation: Audits verify that every request is authenticated, every token is checked, and no internal API is implicitly trusted.
- API sprawl is outpacing visibility: The average company manages over 500 APIs, many of which are undocumented or untracked. Without audits, shadow and zombie APIs remain invisible and exploitable.
- Breaches are exploiting business logic: Recent incidents show attackers aren’t just looking for open ports. They exploit broken auth flows, excessive data exposure, and access misconfigurations that standard scanners miss.
- Audits drive DevSecOps alignment: By exposing design-level risks early, audits feed secure coding practices, CI/CD integration, and continuous improvement. They turn reactive patching into proactive control.
When Should You Audit APIs?
Audits aren’t one-time events. They’re checks that need to happen at specific inflection points in the development and security lifecycle.
- During CI/CD: Automate static analysis, schema validation, and secrets detection to run with each commit. Run blocking checks before deployment, not after.
- Before major releases: Audit new endpoints, role logic, and third-party integrations before they hit production. Avoid introducing new risks during rollout.
- After an incident: If there’s a breach, a misused token, or suspicious behavior, trigger a targeted audit. Look for exposed endpoints, broken authorization, and privilege escalation.
- On a fixed schedule: Audit frequency should match risk:
- High-risk APIs: monthly scans, quarterly manual reviews
- Medium-risk: quarterly scans, biannual review
- Low-risk: twice-a-year scans, annual review
- After structural changes: Run audits after migrations, API version changes, or authentication upgrades. Even small changes to access control or data flow can introduce exposure.
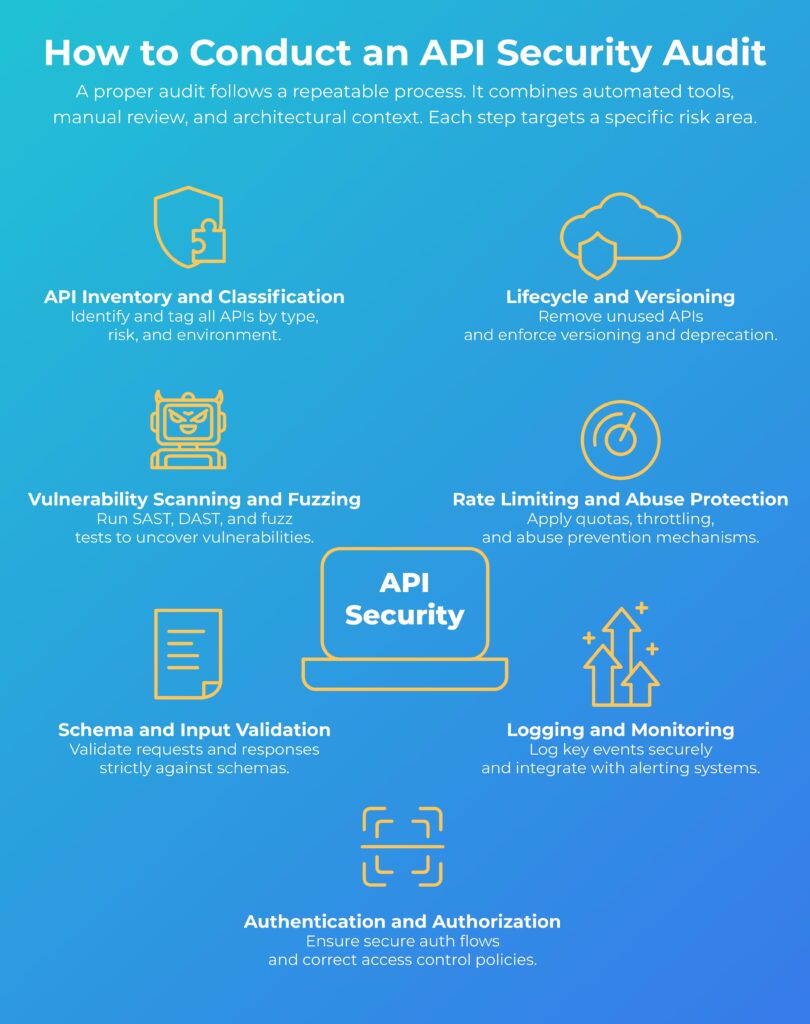
How to Conduct an API Security Audit
A proper audit follows a repeatable process. It combines automated tools, manual review, and architectural context. Each step targets a specific risk area.
API Inventory and Classification
Start by identifying every API in use. That includes internal, external, public, partner, and deprecated endpoints. Use OpenAPI or Swagger definitions where possible. Tag APIs by risk level, sensitivity, and environment. This provides scope and audit priority.
Vulnerability Scanning and Fuzzing
Run static analysis (SAST) to check for unsafe functions, insecure dependencies, and leaked secrets. Use dynamic testing (DAST) against running APIs to simulate attacks. Include fuzz testing to see how APIs respond to malformed inputs and edge cases.
Schema and Input Validation
Review the request/response models against defined schemas. Enforce strict validation on all parameters and payloads. Check for missing filters, lenient type handling, or overexposed data fields.
Authentication and Authorization
Verify that all endpoints require authentication. Inspect OAuth2 flows, token expiry, and refresh mechanisms. Confirm that RBAC or ABAC policies match intended access levels. Test for object- and function-level authorization gaps.
Logging and Monitoring
Check what’s logged, where it’s stored, and how long it’s retained. Logs should include auth events and anomaly triggers, but not leak secrets or PII. Ensure logs feed into a SIEM or alerting pipeline.
Rate Limiting and Abuse Protection
Review per-user and per-key rate limits. Check for throttling, IP reputation controls, and request quotas. Confirm different thresholds for internal vs. public APIs.
Lifecycle and Versioning
Identify unused or deprecated endpoints. Confirm versioning strategies are in place. Look for legacy APIs still in use and verify that deprecation plans are documented and enforced.
Tools for API Auditing
Choose tools based on scope, environment, and integration points. As no single tool does everything, you’ll want to have a combination of options for full coverage.
Open Source Tools
- OWASP ZAP: Dynamic testing. Finds injection points, missing headers, and exposed parameters.
- Burp Suite Community Edition: DAST with manual testing features. Widely used for API fuzzing and auth testing.
- Semgrep: SAST. Lightweight, fast, and CI-friendly. Great for catching hardcoded secrets and risky patterns.
- RateMyOpenAPI: Audits OpenAPI specs against security best practices.
- Akto (free tier available): Discovers shadow APIs. Includes passive monitoring and testing.
- Bandit: Python-specific static analysis.
- Nmap + OpenVAS: Used for service discovery and infrastructure-level vulnerabilities.
Commercial Tools
- Salt Security: Runtime protection and shadow API discovery at scale.
- Traceable: Monitors live traffic for anomalies and abuse patterns.
- Data Theorem: Covers code, runtime, and third-party API exposure.
- Checkmarx / Cycode / Jit: SAST with enterprise integrations and workflow support.
- StackHawk: CI-integrated DAST. Supports OpenAPI fuzzing and build gating.
- 42Crunch: Validates OpenAPI specs and enforces security rules.
- Probely / Astra / APIsec: Automated DAST with OWASP API Top 10 mapping.
- Contrast Security: Offers IAST and RASP with dev-friendly output.
- Akamai: API security and threat detection built into edge delivery and WAF platforms.
- Ox Security: Tracks security across the software supply chain with CI/CD integration.
- Snyk: Finds and fixes vulnerabilities in dependencies, container images, and IaC.
- Fossa: License compliance and open-source dependency risk analysis at scale.
DevOps & Monitoring
CI/CD
- GitHub Actions
- Jenkins
- GitLab CI
SIEM & Telemetry
- IBM Instana
- Splunk
- Elastic Stack
- Datadog
- Sumo Logic
- Coralogix
- OpenTelemetry
API Gateways
- Kong
- AWS API Gateway
- Zuplo
Use commercial tools for scale, but don’t ignore well-configured open-source setups. What matters is visibility and speed to action, not the brand name.
Mapping to OWASP API Top 10
The OWASP API Security Top 10 provides a structured way to prioritize audit findings and coverage. Map each issue found to one or more of these categories.
- API1:2023 Broken Object Level Authorization: Look for missing per-object access checks. Test ID manipulation across endpoints.
- API2:2023 Broken Authentication: Review token implementation. Check for missing expiry checks or token reuse.
- API3:2023 Broken Object Property Level Authorization: Validate field-level access. Prevent over-posting or exposure of internal attributes.
- API4:2023 Unrestricted Resource Consumption: Confirm rate limiting and quota enforcement.
- API5:2023 Broken Function Level Authorization: Restrict access to internal or admin functions. Verify routing logic.
- API6:2023 Unrestricted Access to Sensitive Business Flows: Review flows like checkout, balance transfer, or privilege escalation paths for abuse risk.
- API7:2023 Server-Side Request Forgery (SSRF): Test any endpoint that makes outbound calls based on user input.
- API8:2023 Security Misconfiguration: Check default configs, verbose error messages, or unpatched services.
- API9:2023 Improper Inventory Management: Compare documented APIs against actual traffic. Identify shadow and zombie APIs.
- API10:2023 Unsafe Consumption of APIs: Treat third-party API responses as untrusted. Validate input before use.
Tie each audit finding to its OWASP category. This helps security leads prioritize fixes, track coverage, and explain risk in consistent terms.
Automating and Integrating API Security Audits into DevOps
API audits should not be siloed or reactive. You have to embed them into your software delivery lifecycle to detect issues before they reach production. Here’s how, plus the tools you’d need to make it work.
CI/CD Integration
Use static analysis, OpenAPI validation, and secrets detection as pre-commit checks. Block builds on failed tests.
Tools: Semgrep, Jit, Checkmarx, 42Crunch, GitHub Actions, Ox Security, and Fossa.
Pre-Deployment
Run DAST and fuzzing tests in staging environments. Simulate abuse scenarios.
Tools: StackHawk, OWASP ZAP, Burp Suite, APIsec
Runtime Visibility
Feed API logs into your SIEM. Use anomaly detection and alerting. Track endpoint drift and detect misuse patterns.
Tools: Salt Security, Elastic Stack, Datadog, Traceable, Akamai, and Instana.
Continuous Inventory
Monitor for shadow APIs, orphaned endpoints, and undocumented routes.
Tools: Akto, Data Theorem, API Gateway logs
Governance
Tie test results to Jira tickets or GitHub issues. Use scorecards to track security posture over time.
Frameworks: OWASP API Top 10, NIST SSDF, PCI DSS 4.0
Automating API security should not replace audits; rather, it enables you to run them more frequently and with higher consistency, providing better feedback loops.
How GlobalDots Can Help
Most teams don’t have dedicated AppSec coverage for APIs. That’s where we come in.
GlobalDots delivers hands-on API security assessments aligned to OWASP, Zero Trust, and compliance frameworks. Our team helps you:
- Build or clean up your API inventory
- Identify auth gaps, broken flows, and business logic exposures
- Set up runtime monitoring and posture dashboards
- Map audit findings to controls like PCI, HIPAA, and SOC 2
- Design CI/CD-ready security processes
We work across vendors and tech stacks. You won’t get pushed onto a platform. You’ll get clear findings, practical remediations, and a plan to keep improving.
Need help running your first full-stack audit or tightening up what you already have? Request a consultation.
Conclusion
APIs carry your business logic, user data, and integration points. They’re also where attackers look first.
An API security audit gives you a structured way to find what’s exposed, what’s broken, and what needs fixing.
Make audits part of your lifecycle. Run them during CI/CD, before launches, and after any incident. Track them against OWASP, compliance frameworks, and your own internal policies. Automate where you can, and revisit what matters most.
Talk to us today
GlobalDots can help you get started, scale your efforts, or benchmark where you stand






