APIs are the backbone of today’s interconnected software. They power everything from mobile apps and SaaS platforms to internal microservices and partner integrations. But their rapid growth has left many security teams flat-footed.
In 2025, many attackers prefer to exploit API misconfigurations hiding in plain sight. What used to be fringe cases (token leakage, zombie endpoints, and logic abuse) are now daily realities.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

This article defines the modern standard for protecting APIs at scale. From authentication to monitoring to governance, these best practices provide a clear and actionable reference for cloud-native and security-conscious teams.
Why API Security Best Practices Matter Now
Increased exposure, faster deployments among others have made APIs the #1 attack vector in cloud-native stacks.
Consider the data:
- 76 million T-Mobile users had their data exposed via misused APIs.
- Duolingo leaked user data through public-facing endpoints without proper rate limits or controls.
- Optus exposed 10 million customer records due to a neglected legacy API.
In all three cases, attackers exploited normal functionality that lacked security hardening.
The best practices we’re going to discuss are operational guardrails that reduce risk across the API lifecycle. The earlier and more systematically you apply them, the more resilient your environment becomes.
10 API Security Best Practices for Secure Applications in 2025
1. Know Your APIs
You can’t protect what you can’t see. Yet most organizations underestimate their API footprint, especially internal, deprecated, or third-party-connected endpoints.
Shadow APIs emerge when developers bypass formal release processes. And zombie APIs linger when endpoints are deprecated but never fully removed. Both are rarely tracked, often lack strong authentication, and sometimes run in debug mode or leak stack traces — conditions attackers specifically look for.
Dev, test, or staging environments can be exposed to the public internet or inadvertently linked to production assets. If you’re not consistently discovering and enforcing policy across all environments, these gaps remain invisible to security teams but fully visible to anyone scanning your infrastructure.
Best practices:
- Automated discovery: Use tools that passively and actively scan traffic to identify all API endpoints.
- Classification: Label each API by business criticality, data sensitivity (e.g., PII, payment, IP), and exposure level. This enables risk-based prioritization.
- Tag for ownership: Assign accountable teams. Security without ownership leads to drift.
This visibility is foundational. Without it, every downstream practice risks being incomplete.
2. Apply Strong Authentication and Authorization
Most major API breaches come down to access control failures. Either the API allows too much, or doesn’t verify enough. A public endpoint returning sensitive data without auth is a dangerous misdesign.
Best practices:
- Use OAuth 2.0 and JWTs for modern, token-based auth. Avoid custom schemes unless absolutely necessary.
- Enforce mutual TLS (mTLS) for internal service-to-service communication. It protects against man-in-the-middle attacks and impersonation.
- Implement role-based and attribute-based access control (RBAC/ABAC) at the method or resource level. Blanket access rules are risk multipliers.
- Audit token scopes and expiration regularly. Over-permissioned or never-expiring tokens are time bombs.
These controls should be tested, versioned, and validated just like the code they protect. If your API talks to the world, give it the same access controls you’d demand from a login screen.
3. Secure Tokens and Secrets
API security often breaks in the way secrets are stored, shared, and forgotten. Leaked AWS keys and hardcoded secrets, for example, continue to fuel breaches, especially in cloud-native DevOps pipelines.
Best practices:
- Never hardcode credentials into source code, config files, or environment variables checked into version control.
- Use vault-based secret managers like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault to generate and rotate secrets securely.
- Enforce rotation policies with short TTLs for API keys, tokens, and credentials. Automation helps reduce developer friction.
- Scan code repos (private and public) for exposed secrets. GitHub, GitLab, and Bitbucket have native tools or support third-party scanners.
Treat every secret as if it will eventually leak, and build your systems to minimize the damage when that happens. Think Murphy’s Law here.
4. Validate Inputs and Enforce Schemas
Your API is only as secure as what it accepts. Without strict input validation and schema enforcement, you open the door to injection attacks, data leakage, and service instability.
Best practices:
- Define strict request/response schemas using OpenAPI or JSON Schema. Reject any payload that deviates from spec.
- Validate all input fields for type, length, format, and allowed values. Especially for user-submitted data.
- Reject extraneous fields not defined in the schema. Many attackers use unexpected fields to probe for hidden behaviors or inject malicious content.
- Centralize input validation through middleware or gateways, not just at the business logic layer.
Schema validation is a security boundary. Enforcing it at the edge can prevent malformed requests from ever reaching your application layer.
5. Use Gateways for Enforcement and Visibility
Think of your API gateways as more than just traffic routers. When used properly, they become a policy engine, observability hub, and enforcement point for security controls.
Best practices:
- Terminate TLS at the gateway to inspect encrypted traffic and enforce security headers.
- Apply rate limits and quotas per user, IP, or token to mitigate brute-force attacks and abuse.
- Enforce authentication and schema validation before requests reach your services.
- Log traffic with context (user ID, origin, request path, method) to support audit trails and anomaly detection.
Note that a gateway doesn’t replace your backend’s logic or checks. It layers defenses where they’re easiest to maintain and monitor, which is at the edge of your API stack.
6. Load Testing and Cost Forecasting
Sustaining operations under stress is also an important aspect of API security. Many APIs can be brought down with basic volumetric abuse if backend services or rate limits aren’t tested under load.
Best practices:
- Conduct realistic load tests to model abuse scenarios, such as burst traffic, scraping, or brute force login attempts.
- Analyze downstream impacts on services like databases, identity providers, or third-party APIs.
- Forecast operational costs for API usage patterns and edge cases. Some attacks aim to spike your bill, not just your error rate.
- Simulate failure modes (e.g., token service unavailable) to validate fallbacks and error handling.
This isn’t performance testing for its own sake. It’s a way to identify denial-of-service vectors and budget risks before attackers do.
7. Monitor Runtime Behavior
Even the best-prepared APIs become vulnerable in production. Runtime monitoring fills the gap between prevention and detection, especially for logic abuse, credential misuse, or zero-day tactics.
Best practices:
- Baseline normal usage patterns by user, method, and endpoint. Track frequency, location, payload size, and sequencing.
- Alert on anomalies, not just known signatures. For example, low-volume probing across endpoints or irregular auth failures from known tokens.
- Correlate events across systems, such as API calls followed by database spikes or failed identity requests.
- Log context-rich data for forensic investigation: headers, IPs, tokens (masked), user IDs, and response times.
AI-based tools improve this dramatically. They detect misuse that traditional logging won’t catch, like a bot slowly mapping your business logic or a valid token being used at odd times from a new region.
8. Integrate Security into CI/CD
Waiting for production to catch issues is too late. API security must shift left, i.e., start at commit time and flow through build, test, and deploy stages.
Best practices:
- Run static analysis and secret scanning in pre-commit hooks and CI pipelines to catch hardcoded keys or unsafe patterns.
- Apply schema linting and policy validation before deploy, especially for OpenAPI/Swagger definitions.
- Automate security test stages using DAST, fuzzing, or integration security tests.
- Block deploys on high-risk findings and enforce peer reviews on any changes to authentication, access logic, or sensitive data flows.
These controls keep velocity high while reducing blind spots. If your team deploys daily, security needs to run at that speed too.
9. Govern API Lifecycle and Versioning
An API without governance is a liability waiting to be exploited. Or forgotten. Or worse, both. Proper lifecycle management ensures old endpoints don’t become attack surfaces.
Best practices:
- Maintain a central API catalog including internal, external, deprecated, and shadow APIs.
- Use versioning (e.g., /v1/, /v2/) to phase out older contracts safely without breaking consumers.
- Document deprecation timelines and usage policies, even for internal APIs.
- Validate runtime behavior against published specs and flag discrepancies.
Ownership matters. Assign clear responsibility for each API, from initial design to retirement. A forgotten endpoint is an open invitation.
10. Align to Zero Trust Principles
Zero Trust shifts the security model from “trusted networks” to “always verify.” That applies directly to APIs, especially as they connect services across clouds, partners, and remote teams.
Best practices:
- Authenticate every request, regardless of source. Internal APIs should be treated the same as external ones.
- Enforce least privilege with scoped tokens and role-based access controls (RBAC). Don’t over-permission service accounts.
- Microsegment API access so that even if one service is compromised, lateral movement is contained.
- Log and verify behavior, not just credentials. A valid token used in an unusual sequence should trigger scrutiny.
Zero Trust is a mindset. And with APIs, that means assuming compromise and validating every interaction.
Align Your API Security Best Practices to OWASP API Top 10
The OWASP API Security Top 10 provides a threat model. Your best practices should align directly with those categories.
Here’s a simplified table to show the alignment:
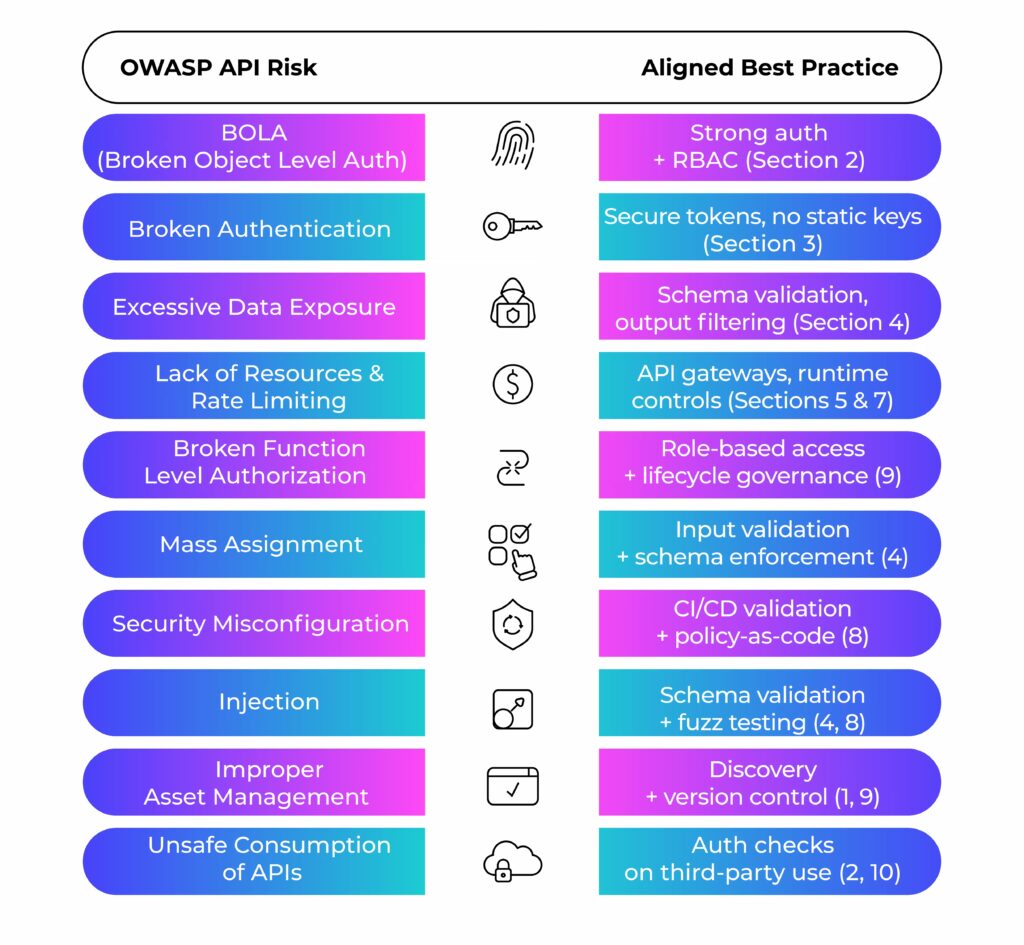
This mapping reinforces the idea that best practices are both defensive and proactive controls that align with known risks.
Key Takeaway: Secure APIs Don’t Happen by Default
The API attack surface is growing. So is the pressure to move fast.
But velocity and security can coexist when your team treats best practices as defaults, not afterthoughts.
Strong authentication, token management, schema enforcement, runtime visibility, lifecycle governance… These aren’t “nice-to-haves.” They’re your defense against real-world threats: credential abuse, business logic attacks, zombie APIs, and CI/CD missteps.
At GlobalDots, we help engineering and security teams integrate best-in-class tools across the API lifecycle. From auto-discovery and AI-powered detection to Zero Trust enforcement and performance-tuned gateways, we bring the components together, without slowing you down.
Let's talk
Reach out today to get a free consultation on your API security posture.






