The Internet of Things creates a reality where end users and simple citizens are much more stakeholders. Businesses need to change their way of working: be slower to make money, be better at building relationships and create a value driven business.
(Rob van Kranenburg)
Future cities are imagined to move the cloud network to real-world devices, to interlink the real world with the virtual. Internet of Things (IoT) describes objects, spaces and people that are tagged and given a unique number, an IP address. Transmitted wirelessly, through radio frequency identification (RFID) tags. Connected to satellite systems that constantly record the digital footprint of every – thing.

And yet, we are already entering the early stage of the Internet of Things (IoT) and this is changing how we do business, how we handle social affairs, how we communicate with each other, how we run a cloud. Or a farm?
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

The Internet of Cattle
An infographic from Cisco neatly describes a Dutch startup, Sparked, that used wireless sensors on cows. Each was embedded with an RFID tag, so that when one was sick or pregnant, it could send a message to the farmer. Each cow, according to the illustration, transmitted 200 mb of data per year.
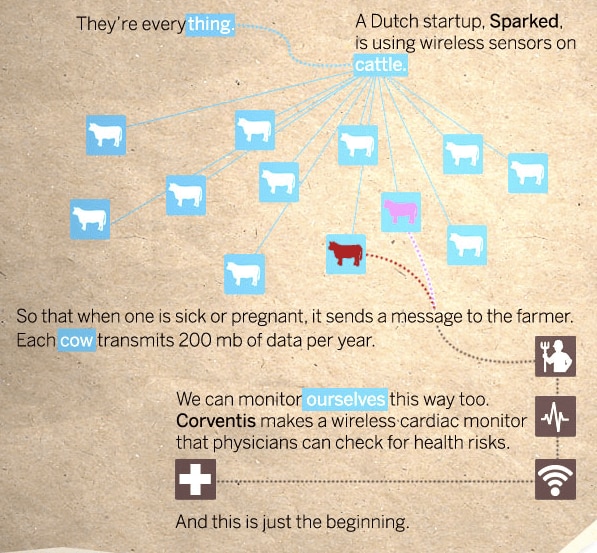
Now think, if this applied to all the cars and trucks on the road, to refrigerators, to each item that you bought in a grocery store. To each man that you greeted. And they all reported to a single control system? What would be the amount of data to process?
The IP addressability would become ubiquitous, which would require ubiquitous computing (also referred to as ubicomp) environment. The environment which is itself an interface. And the computer as a visible technology has disappeared. It is rather thoroughly integrated into everyday objects and activities.
Extelligence: Machine to Machine Communication
This computing would require some kind of an machine to machine, or a thing to thing interaction. Probably far less tolerant to a cloud outage than a human to machine interaction already is. Imagine what a five seconds denial of service could cause in the IoT scenario? And how low security would risk on far more catastrophic consequences if a hacker could, say, operate on your bedroom light, or a credit card?
The details from the Cisco illustration show how this machine to machine interaction could be used for the ultimate convenience of your common day. It accounts for everything from your car to a coffemaker.
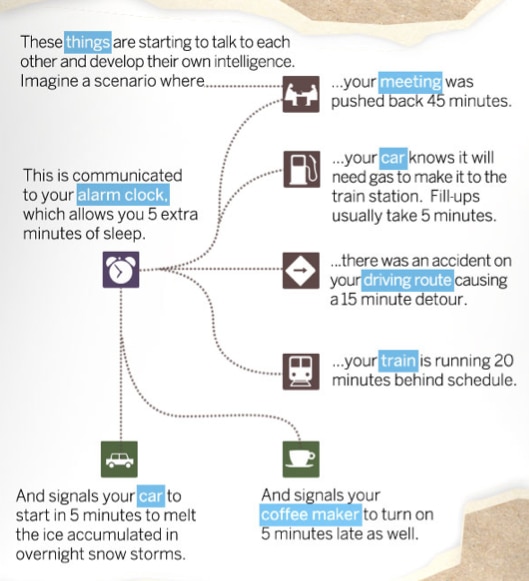
And, how far are we from this, in 2013?
According to Cisco, in 2008 already, the number of things connected to the Internet exceeded the number of people on earth. By 2015, they predict, there will be 25 billion devices, and by 2020, 50 billion things connected to the Internet. Our cameras are already one cubic millimeter in size. The number of possible Internet addresses (IPs) is already 100 times the number of every atom on the face of the earth.
To push things a bit further.
“From the Internet of Things (IoT), where we are today, we are just beginning to enter a new realm: the Internet of Everything (IoE),” Dave Evans writes, “where things will gain context awareness, increased processing power, and greater sensing abilities.” (http://blogs.cisco.com/news/how-the-internet-of-everything-will-change-the-worldfor-the-better-infographic/) He continues: “Given the tremendous anticipated growth of the Internet over the next 10 years, it is critical for business and government leaders, as well as citizens, to begin preparing for what is to come. “
According to somewhat refreshed table from Cisco, and as explained by Evans, “by 2020, with an Internet that has an estimated 50 billion things, the number of connections balloons to 13,311,666,640,184,600. And adding just one more thing (50 billion + 1) will increase the number of connections by another 50 billion!”
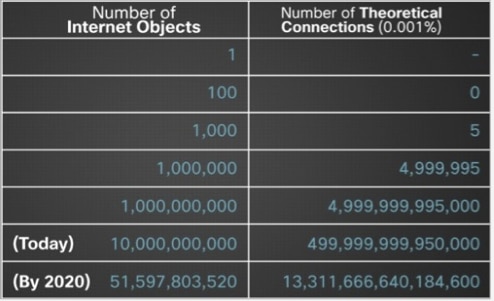
Table source: http://blogs.cisco.com/news/internet-of-everything-its-the-connections-that-matter/
To conclude. For your business, for the economy, for the ubiquitous environment, for your company value over the next decade, what will matter the most are – the connections. Among people, process, data and things, every thing.






