Application security isn’t just a developer’s concern or a security team’s checklist anymore. It’s a full-spectrum challenge that cuts across the software lifecycle, from the code you write to the containers you deploy to the pipelines and people in between.
In 2024 alone, researchers flagged over 40,000 software vulnerabilities, most of which were inherited through third-party code and poorly managed dependencies.
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

Software supply chain attacks have evolved too. Adversaries are increasingly targeting CI/CD systems, misconfigured registries, and public code repositories. A single compromised engineer or exposed token can now poison an entire build.
That’s why today, security is everyone’s responsibility. Developers, ops teams, product managers, and execs all have a role to play.
This guide outlines the most critical application security best practices so everyone responsible can build and maintain secure, resilient software in today’s cloud-native, continuous delivery world.
What is Application Security?
Application Security, or AppSec, is the practice of being proactive with security by embedding secure tools and processes into every stage of the software development lifecycle (SDLC).
Rather than a reactive patchwork of security fixes, it’s a continuous, lifecycle-based approach that ensures applications are resilient to threats by default.
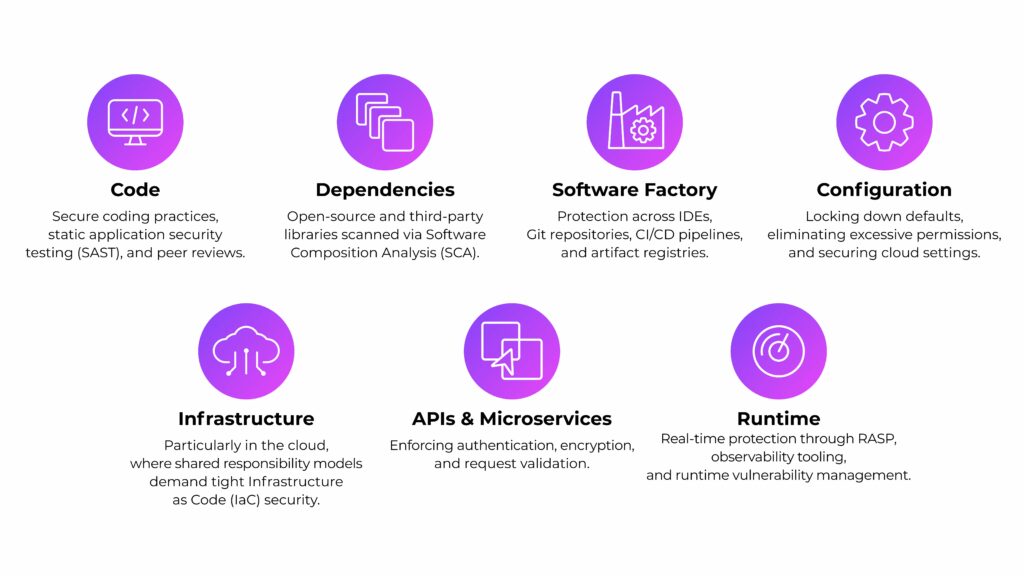
To defend modern applications, AppSec focuses on:
- Code: Secure coding practices, static application security testing (SAST), and peer reviews.
- Dependencies: Open-source and third-party libraries scanned via Software Composition Analysis (SCA).
- Software Factory: Protection across IDEs, Git repositories, CI/CD pipelines, and artifact registries.
- Configuration: Locking down defaults, eliminating excessive permissions, and securing cloud settings.
- Infrastructure: Particularly in the cloud, where shared responsibility models demand tight Infrastructure as Code (IaC) security.
- APIs & Microservices: Enforcing authentication, encryption, and request validation.
- Runtime: Real-time protection through RASP, observability tooling, and runtime vulnerability management.
This matters now more than ever because:
- Cyberattacks are becoming increasingly sophisticated, targeting everything from open-source libraries to CI/CD pipelines.
- Web applications are now the de facto perimeter of most organizations, directly interfacing with the public internet and backend systems, and
- Applications are mostly composed of third-party code, leading to inherited vulnerabilities from external libraries, dependencies, and SaaS integrations.
AppSec builds and operates secure software in an environment where risk is constant and attackers are creative. It’s a mindset, a toolkit, and a mandate.
Secure by Design: Start Early
Security isn’t something you bolt on before production. You build it in from day one. That’s the philosophy behind “Secure by Design,” often referred to as “shifting security left” in the development lifecycle. Instead of catching vulnerabilities at the tail end of delivery, this approach brings security practices into the earliest planning and coding stages, when issues are cheaper and easier to fix.
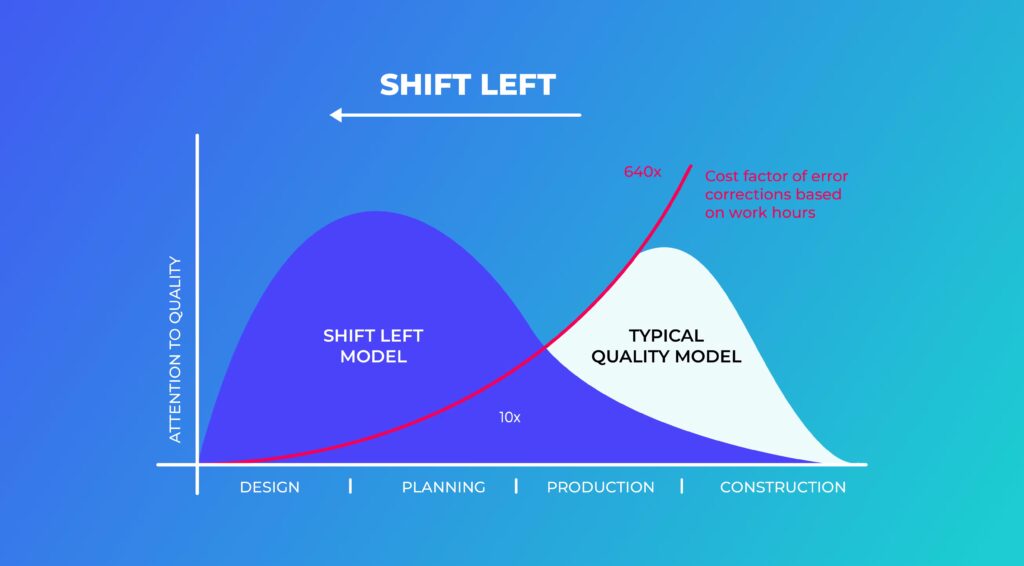
Here’s how to shift security left effectively:
Adopt Secure Coding Guidelines
Secure coding lays the foundation for AppSec. Developers should write code that anticipates real-world threats: SQL injection, cross-site scripting (XSS), and other common attack vectors. This means validating inputs, encoding outputs, avoiding hardcoded secrets, and keeping sensitive data out of logs and error messages.
But good intentions aren’t enough. Security must be embedded into daily development workflows. Tools like SAST should run automatically during pull requests, alerting developers to risky code before it gets merged. Frameworks often provide built-in protections. Use them instead of reinventing security mechanisms.
Even small decisions, such as using data transfer objects (DTOs) to limit data exposure in APIs, can make a significant difference. Regular peer reviews with a security lens help catch what automation might miss. You don’t want to slow down development. Instead, you want to make secure decisions as a habitual practice.
Align these practices with resources like the OWASP Top 10 (discussed below) to keep teams focused on the most common and critical risks.
Perform Threat Modeling in the Planning Stage
Before the first line of code is written, security risks should already be top of mind. During the planning and design phase, teams perform threat modeling to visualize how attackers might exploit a system and identify weak points early.
This isn’t just theory. Threat modeling actually provides a structured approach to architectural decisions, helping to outline security requirements early. It forces developers, architects, and security teams to think like adversaries. Ask, “Who might attack? What would they target? And how are they going to succeed?”
Address these risks at the design stage and you can often eliminate entire classes of vulnerabilities before they ever exist. It’s one of the highest-leverage practices in all of AppSec.
Train Developers & Equip Them with Security Playbooks
Developers are your first line of defense, and often the last chance to stop a bug before it becomes a breach. But they can’t write secure code if they don’t know how.
You need:
- Ongoing training on secure coding practices and common attack patterns.
- Bite-sized, role-specific resources like cheat sheets and “definition of done” security checklists.
- Integrated feedback loops—via Application Security Posture Management (ASPM) platforms or IDE plugins—that explain why something’s a risk and how to fix it.
Even basic improvements in awareness, such as understanding how SQL injection or insecure deserialization occurs, can significantly reduce vulnerabilities. Combine education with automation to nudge developers toward secure defaults without blocking their flow.
During Development: Secure SDLC
Secure SDLC in the heart of development is a shift that’s already happening in leading engineering teams. Security scans now run during pull requests, IDEs flag insecure patterns as you type, and infrastructure misconfigurations are caught before the first deployment.
For example, SAST tools analyze code for vulnerabilities without running it.
They catch:
- Hardcoded credentials
- Insecure input handling
- SQL injection and XSS risks
- Memory and buffer issues
Integrating SAST into your CI pipeline or pull request process helps detect vulnerabilities early, while code is still fresh in a developer’s mind. The faster the feedback, the faster the fix.
Important note here: Make sure your scanner works with the languages your team actually uses. And don’t treat these tools as gatekeepers. Use them as early warnings, ideally paired with remediation advice that your team can act on.
Here are more ways to secure your SDLC during the development phase:
1. Know What You’re Shipping
Most modern apps are assembled, not built from scratch. Open-source components might make up 80–90% of your codebase.
If a library ships with a known vulnerability and your scanner doesn’t flag it, you’re deploying someone else’s exploit.
That’s where Software Composition Analysis (SCA) comes in. It cross-references your packages and versions with vulnerability databases like the NVD or GitHub Security Advisories, so you can:
- Block vulnerable dependencies during PR review
- Prioritize patching based on severity
- Understand license risks across your supply chain
Your team should always run SCA scans during every build. Don’t let a stale dependency compromise your whole system.
2. Detect Secrets Before They Leak
It only takes one leaked API key to give attackers persistent access.
Secrets detection tools catch credentials before they get committed—across code, config files, and pipelines. Integrate them into pre-commit hooks or CI checks. They’ll help your team:
- Avoid pushing credentials to Git
- Spot reused or outdated tokens
- Flag secrets hardcoded into IaC templates
Secrets don’t belong in source control. Use a proper secrets manager, and back it up with scanners that help enforce this in practice.
3. Never Skip Configuration Hygiene
Misconfigurations are one of the most overlooked sources of risk.
In cloud-native environments, configuration is code; therefore, treat it with the same level of scrutiny. IaC templates define your virtual private clouds (VPCs), roles, policies, and container settings. Any insecure default or overly permissive rule can open the door.
Embed security scanning for IaC tools like Terraform, CloudFormation, and Kubernetes YAML into your CI pipeline, so you can catch misconfigurations before they’re deployed.
ASPM platforms can help track config drift, enforce baselines, and alert you when someone modifies a production setting that violates policy.
After Deployment: Monitor, Protect, and Respond
Once your app is live, it’s exposed to real-world users and real-world attackers. Threats evolve, vulnerabilities emerge, and even the best “Shift Left” strategy can’t catch everything before deployment.
That’s where post-deployment security comes in. Protecting a live application requires visibility into what’s happening at runtime, the ability to block threats in real time, and systems that help you learn and respond faster (the merging of runtime protection, observability, and alerting).
Runtime Protection to Detect and Block Threats as They Happen
While pre-deployment tools analyze code, Runtime Application Self-Protection (RASP) works inside the running application. It monitors behavior in real time and can take immediate action, like blocking suspicious requests or killing a malicious session.
Unlike external defenses, RASP has access to the app’s internal context: code execution paths, data flows, and system interactions. That gives it a powerful vantage point to:
- Prevent SQL injections and XSS from executing
- Stop zero-day exploits before a patch is available
- Log granular details for root cause analysis
Think of it as a runtime bodyguard inside the building that understands both the application’s logic and its attack surface.
Web Application Firewalls: The First Line of Runtime Defense
Where RASP works from within, Web Application Firewalls (WAFs) act as gatekeepers, patrolling the castle walls. They sit between your app and the internet, filtering incoming traffic for known attack patterns.
Modern WAFs can block:
- Injection attacks (SQL, XSS)
- Protocol abuse (HTTP smuggling, request floods)
- Known exploit payloads targeting exposed libraries
They’re especially useful when patching isn’t possible immediately. A well-tuned WAF rule can mitigate an exploit in hours, not days.
And because WAFs can be centrally managed, they’re a scalable way to enforce policies across multiple apps and APIs.
Observability and Alerting: Know What’s Happening, Act Fast
Deploying protections is only part of the story. You need visibility into what’s happening across your app ecosystem and a way to act quickly when something goes wrong.
Start with robust logging: authentication events, user actions, system errors, and WAF/RASP signals. Good logs are the raw material for detecting threats, auditing incidents, and understanding impact.
Add observability tools (like Azure Monitor, Datadog, or New Relic) to stitch together a live picture of your systems. Observability isn’t just about performance; it helps security teams spot anomalies, detect drift in infrastructure, and pinpoint unusual behavior.
Finally, build a real-time alerting pipeline. Connect your logs to a SIEM (e.g., Azure Sentinel) and set up triggers for:
- Repeated failed login attempts
- Requests with known attack signatures
- Sudden spikes in traffic or error rates
- Configuration changes outside of approved pipelines
Don’t just alert internal teams. For major incidents—especially breaches or exposure of sensitive data—notify affected users and stakeholders quickly and clearly.
ASPM: The Glue That Ties It All Together
ASPM platforms play an important role post-deployment. They aggregate data from multiple sources—SAST, SCA, IaC scans, WAFs, RASP, observability tools—and help security teams to track security posture across the SDLC, detect misconfigurations or drift after release, and coordinate response and remediation activities.
When implemented well, ASPM becomes your central control tower, monitoring the full attack surface and surfacing the insights that matter most.
Mapping to the OWASP Top 10 (2025)
The OWASP Top 10 is one of the most trusted frameworks for identifying the most critical web application security risks. While the 2025 edition is still in progress, the 2021 version remains the current benchmark.
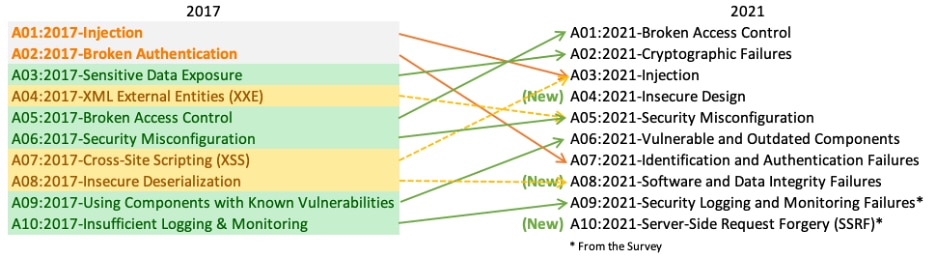
More than a checklist, the Top 10 reflects the vulnerabilities that are most often exploited in real-world breaches.
When you compare common AppSec practices across the software lifecycle to OWASP’s risk categories, clear patterns emerge. Shifting left with code analysis tools and secure design prevents risks before deployment. Runtime tools and observability catch what slips through and adapt to evolving threats.
| AppSec Practice | OWASP Top 10 Risks Addressed (Examples) | How It Helps | Phase |
| Static Code Analysis (SAST) | A01, A02, A03, A04, A05 | Finds insecure coding patterns, hardcoded secrets, logic flaws | Development (Shift Left) |
| Dependency Scanning (SCA) | A06 | Flags vulnerable open-source components | Development (Shift Left) |
| Secrets Detection | A02, A05 | Identifies exposed credentials and API keys | Development & Pre-commit |
| Configuration Hygiene (IaC Sec) | A05 | Prevents insecure infrastructure defaults and drift | Development (Shift Left) |
| RASP (Runtime Protection) | A01, A03, A05, A06 | Monitors and blocks live attacks during execution | Runtime |
| WAFs (Traffic Filtering) | A03 (especially SQLi, XSS) | Blocks malicious payloads at the edge | Runtime |
| Logging & Observability | A01, A03, A07, A09 | Detects abnormal activity, accelerates incident response | Runtime |
No single tool solves everything. But collectively, these practices create a layered defense that addresses each OWASP category through prevention, detection, or response.
Other OWASP Projects That Strengthen Your Strategy
While the Top 10 is the flagship resource, OWASP maintains a broader ecosystem of projects that reinforce secure development and operations:
- OWASP Testing Guide: A comprehensive resource for designing effective security tests.
- OWASP Cheat Sheet Series: Practical implementation tips for secure coding practices.
- OWASP Code Review Guide: Focused on reviewing software for design and implementation flaws.
- Threat Modeling and Secure Design Guides: Help teams build threat awareness into the architecture phase.
- Top 10s for Specific Domains: OWASP now includes lists for API security and GenAI/LLMs, which is important as your stack diversifies.
These aren’t static documents. Many are actively maintained and incorporate community feedback, making them especially valuable when exploring unfamiliar risks or new technologies.
Here’s how OWASP’s categories play out in real-world mitigation:
- Injection (A03): Defend against SQL and XSS attacks by using parameterized queries, input validation, and modern ORMs. WAFs provide a frontline defense, but secure code is the foundation.
- Security Misconfiguration (A05): Scan containers and IaC templates regularly. Ensure least-privilege access. IaC scanning tools can catch overly permissive defaults before deployment.
- Vulnerable Components (A06): Patch frequently. Automated SCA tools can monitor for Common Vulnerabilities and Exposures (CVEs) in open-source packages.
- Authentication Failures (A07): Use strong password policies, sessions with limited scope and duration, and enable MFA wherever possible.
- Logging and Monitoring Failures (A09): Aggregate logs, alert on anomalies, and test your detection logic. Tools like Azure Sentinel or Splunk can surface incidents in time to respond.
Mapping your practices to OWASP’s categories makes gaps in your security posture obvious. If you’re investing in secure design but have no observability into runtime behavior, you’re likely exposed to A09 (monitoring failures) and A01 (access control). If you’re scanning code but ignoring dependency updates, A06 will catch you off guard.
Building a DevSecOps Culture with Automation
By this point, it’s clear that security can’t be something you bolt on after release. But embedding it across the lifecycle—without slowing development to a crawl—requires cultural change, automation, and a shared sense of ownership.
That’s the core of DevSecOps. Security becomes part of the pipeline, codified, testable, and version-controlled, just like everything else. Vulnerability scans run as part of CI. IaC security checks gate deployments. Alerts feed into tools your developers already use. And all of it’s tracked—MTTR, fix rate trends, test coverage—so you know if your process is actually working.
But DevSecOps is also about people. When engineering and security teams use the same tools and share KPIs, it’s easier to collaborate than to clash. The result? Fewer silos, faster fixes, and security that scales with your codebase.
How GlobalDots Helps You Secure Every Stage
Tooling only gets you so far. What teams need is guidance; someone to help them architect an AppSec program that’s as fast and adaptable as their software delivery.
That’s where GlobalDots comes in. We help companies embed security into every phase of development, from threat modeling and IaC scanning to runtime protection and post-release monitoring. Whether you’re modernizing a fragmented stack or scaling your AppSec operations, our advisory and engineering teams bring the experience to align tools, workflows, and goals.
From CI/CD-integrated testing to zero-friction runtime defenses, we help you shift security both left and right, with the speed and flexibility your teams need to deliver safely, every time.
Conclusion: Security is a Lifecycle
Application security isn’t a one-and-done affair. It’s a system (or culture) that evolves with your development practices, threat landscape, and business goals. When you treat security as a lifecycle, you move from reactive patching to proactive risk reduction.
The frameworks exist. The tooling is mature. What most teams need is clarity, orchestration, and a partner who can help put it all together.
Let’s talk. If you’re ready to make security a seamless part of how you build and run software, book a consultation or demo with GlobalDots.






