Cloud-native environments are growing more complex and distributed. This growth makes security and performance observability even more critical to modern DevSecOps strategies.
Enter eBPF (Extended Berkeley Packet Filter), a revolutionary technology that can run sandboxed programs in a privileged context such as the operating system kernel, which enables enhanced:
Book a demo today to see GlobalDots is action.
Optimize cloud costs, control spend, and automate for deeper insights and efficiency.

- Runtime observability
- Threat detection, and
- Proactive security enforcement
Its ability to extend kernel capabilities without modifying the source code revolutionized data capture, processing, and use.
But its real power plays out when you pair it with the context of cloud infrastructure, which provides unparalleled insights into network and application behavior, transforming DevSecOps. Here’s how.
Granular Insights with eBPF
At its core, eBPF provides a detailed data layer that spans network layers 3, 4, and 7. This way, users capture real-time information about network communication and match it with specific processes and applications.
For example, where traditional network monitoring tools reveal traffic volumes on port 443, eBPF will segment this data to show which applications are actually generating that traffic.
However, eBPF’s raw data isn’t enough on its own. If you pair this data with cloud context, like Kubernetes identities, namespaces, and APIs, eBPF can provide actionable insights about your network topology, such as:
- Identifying the exact resources and services in use
- Tracking application-level identity and behavior, and
- Detecting anomalies, such as unauthorized connections or unusual traffic patterns, as they happen
Such in-depth visibility allows organizations to respond quickly to performance issues and potential compromises, all while maintaining a clear understanding of their network architecture.
How eBPF Enhances Observability Without Compromising Performance
eBPF is designed to capture comprehensive system data with minimal overhead, making it ideal for cloud-native environments where performance is critical. Applying filters directly at the kernel level, eBPF reduces the noise associated with raw data ingestion while retaining the critical information that matters.
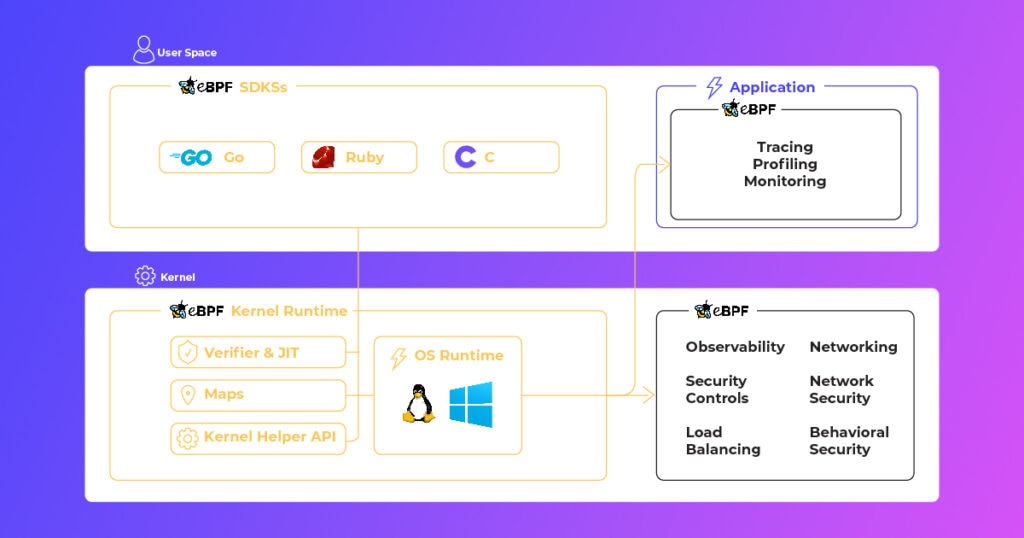
Concretely, this means teams can:
- Track system call events and network activity without degrading performance
- Visualize traffic routes end-to-end across containers, pods, and nodes
- Uniformly inspect TLS traffic at multiple layers, gaining visibility into encrypted communications
With these capabilities in place, you can monitor, analyze, and secure your cloud environments while maintaining efficiency.
Proactive Threat Detection and Automated Response
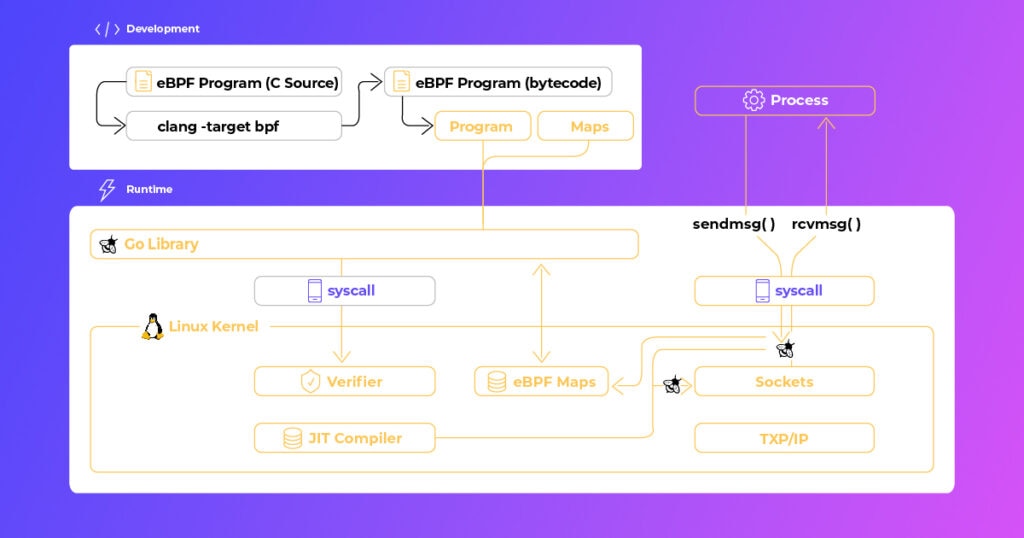
Another strong advantage of eBPF capturing data at the OS level is proactive threat detection, which, in turn, powers automated response.
It helps users detect abrupt behavior changes, such as traffic spikes within specific processes, out-of-pattern service-to-service communication trends, and potential exploitation attempts such as unauthorized API calls or unusual system calls.
But eBPF doesn’t stop at detection. Its architecture also supports proactive threat prevention. For example, teams can use eBPF to:
- Automatically block malicious processes or predefined system calls
- Terminate suspicious network packets in real-time, minimizing the attack surface
- Enforce prevention rules to secure workloads against emerging threats
eBPF’s granular control excels in bridging security and observability, making it a powerful ally for real-time threat response and risk mitigation.
Reduced Alert Noise and Improved Forensic Analysis
Alert fatigue is a real problem in DevSecOps. And it can be intensified with the abundant data that eBPF generates. With the right tools, it’s possible to filter and aggregate this data to deliver meaningful insights and avoid overwhelming users.
Image source: Upwind
When eBPF data is enriched with context, teams can focus on high-priority issues and pinpoint problem origins faster for more streamlined forensic investigations. It also helps with understanding the potential blast radius of compromised applications by analyzing process-level communication.
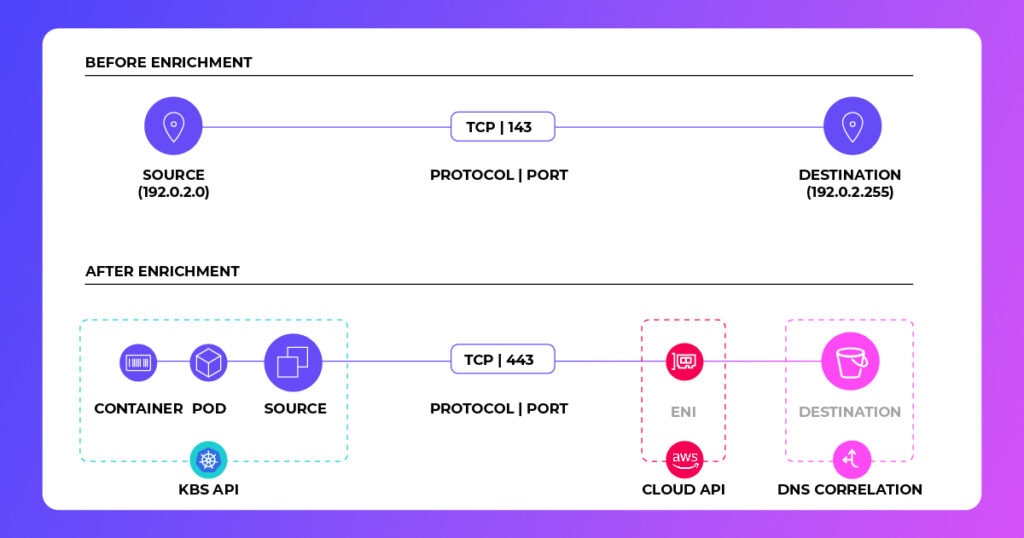
For example, if an application is compromised, eBPF data can reveal how far the threat might spread, which services are impacted, and what immediate actions are needed to contain the damage.
A Critical Tool for Modern DevSecOps
Experience has shown that cloud-native complexities demand an observability approach capable of diving right into the kernel — without taxing performance. That’s exactly what eBPF delivers: in-depth visibility for performance monitoring, threat detection, and proactive security enforcement. Earning it ‘core pillar’ status in modern DevSecOps.
To harness the full potential of eBPF, it needs to be integrated with vital cloud context to illuminate every essential detail of your network topology. This results in insights that empower security teams to address threats with speed and operational efficiency.
This blog post was written in collaboration with Upwind






