Sign up to our Newsletter
There are endless security risks in the Tech world of today: cars are being hacked, IoT is used in DDoS attacks and ransom Malwares are holding hostage computers. But perhaps one of the most concerning threat out there is the Zero-Day Attack.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Tweet this: Zero-Day Attack: Attack that targets a previously unknown vulnerability
A Zero-Day Attack is a type of attack that uses a previously unknown vulnerability. Because the attack is occurring before “Day 1” of the vulnerability being publicly known, it is said that the attack occurred on “Day 0” – hence the name. Zero-Day exploits are highly sought after – often bought and sold by private firms or entities anywhere from $5,000 to Millions of Dollars, depending on what applications and operating systems they target – as they almost guarantee that an attacker is able to stealthily circumvent the security measures of his or her target. Private security firms aside, software vendors will also usually offer a monetary reward among other incentives to report zero-day vulnerabilities in their own software directly to them.
1.5 Million Dollars for iPhone Vulnerabilities
Take as an example the world’s most successful smartphone – Apple’s security is far from being hack-proof. iOS 10 has already been jailbroken, although the jailbreak isn’t yet available to the masses. That means there are vulnerabilities in the code, or potential Zero-Day Attacks, that hackers can use to get access to the phone. And a company that sells such exploits has raised its bug bounty for iPhone zero-day attacks — the kind of vulnerabilities that Apple hasn’t yet discovered — to $1.5 million. Zerodium is the exploit broker that’s willing to pay $500,000 more than last year’s $1 million bounty for similar hacks. As Wired reports, the money will go to anyone who can perform a remote jailbreak of an iPhone running iOS 10.
Tweet this: Zerodium offers $1.5 mil for jailbreaking an iPhone running iOS 10
Zero-Day DDoS – The Early Days
But What are Zero-Day DDoS attacks? Zero-Day DDoS attacks are basically the same thing, attack vectors that uses a previously unknown Denial of Service vulnerability. One of the first and certainly one of the most famous Zero-Day DDoS attacks, was the teardrop attack. In the mid-late 1990s, a very simple vulnerability in with TCP/IP in certain operation systems was discovered. Back then, DDoS attacks were a lot less common, and used for far fewer purposes. Nowadays, people use DDoS attacks for things like extortion and hacktivism, but back in those days DDoS attacks were used to annoy people that you didn’t like on the Internet. In the case of the Teardrop attack, if the recipient of the attack was running a vulnerable operating system, their system would just crash and require a reboot. The premise behind the attack was quite simple. The attacker generates packets that are fragmented with malformed offsets, causing the operating system to not know how to reassemble the packet. In Windows 3.1, 95, NT, and Linux versions prior to 2.0.32 and 2.1.63, this caused the system to simply crash.
Tweet this: One of the 1st and most notorious zero-day DDoS attacks: Teardrop & Ping-Of-Death
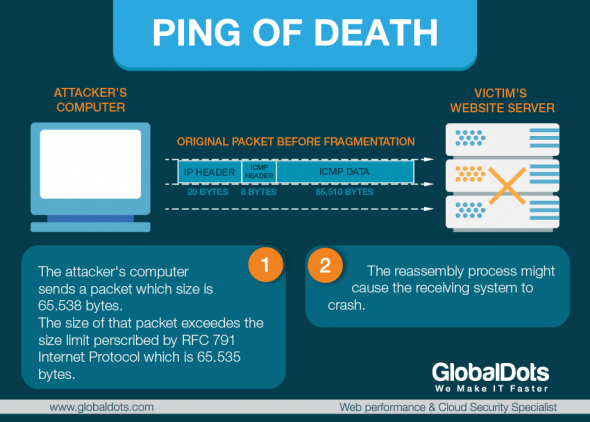
Another extremely notorious Zero-Day DDoS attack was the Ping of Death. In the late 90s, a vulnerability in many operating systems was discovered. Basically, if the operating system had to process a packet whose size was greater than 65536 bytes it would cause issues such as buffer overruns, kernel panics, full system reboots and system hangs. The reason for this is due to the fact that the way to cause a remote crash was to send an ICMP echo request (ping) to an IP address, specifying a certain packet size. In Windows 95 and NT, it was just one simple command to crash a remote system that was vulnerable:
ping -l 65536 10.100.101.102
Will The Internet Break?
Those were the early days of Zero-Day DDoS attacks. Today’s attacks are developing in a worrying pace. New Zero-Day DDoS attacks are emerging not just in terms of protocol exploit but also on the technical side. The latest to feature both is demonstrated in the last wave of attacks against internet address-translation service Dyn, Krebs Security and French ISP OVH. These attacks combined to new features: Mirai, a malware that helps round up IoT devices and infect them so they can carry out coordinated DDoS attacks of enormous scale and new zero-day DDoS attack vector observed for the first time. The new technique is an amplification attack, which utilizes the Lightweight Directory Access Protocol (LDAP): one of the most widely used protocols for accessing username and password information in databases like Active Directory, which is integrated in most online servers.
The severity of such a combined Zero-Day technique with Zero-Day DDoS have brought many to ask: “Is the Internet about to break?”. Well, perhaps not just yet, but it is a valid question regarding the future and the ability of a new Zero-Day DDoS attack to one day bring the internet to it’s knees.
Contact us today to make a security scanning of your infrastructure.