Sign up to our Newsletter
Achieving and maintaining a comprehensive cybersecurity posture is critical for modern enterprises.
In this article we discuss how organizations can use DNSSEC to protect themselves from DNS cyber attacks.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Domain Name System (DNS)
To understand Domain Name System Security Extensions (DNSSEC), it helps to have a basic understanding of the Domain Name System (DNS).
The proper functioning of the Internet is critically dependent on the DNS . Every web page visited, every email sent, every picture retrieved from a social media: all those interactions use the DNS to translate human-friendly domain names (such as icann.org) to the IP addresses (such as 192.0.43.7 and 2001:500:88:200::7) needed by servers, routers, and other network devices to route traffic across the Internet to the proper destination.
For example, if you request an address such as www.globaldots.com, DNS will translate it to something like 198.102.746.4. These internet phonebooks greatly influence the accessibility of Web locations which is exactly why DNS is crucial for any organization that relies on the Internet to connect to customers, partners, suppliers and employees.
The top level of the DNS resides in the root zone where all IP addresses and domain names are kept in databases and sorted by top-level domain name, such as .com, .net, .org, etc.
When the DNS was first implemented, it was not secured, and soon after being put into use, several vulnerabilities were discovered. As a result, a security system was developed in the form of extensions that could be added to the existing DNS protocols.
DNS offers a very attractive attack target, here’s why:
- The DNS “attack surface” is broad. Attackers can compromise the DNS system via registrars, access to zone files, or through numerous means of hijacking and man-in-the-middle attacks.
- DNS is a rich target – a successful attack can deliver unrestricted access to networks and data as well as provide the potential for extreme disruption to critical systems.
- DNS is often poorly protected. Most organizations haven’t put a lot of work into securing their DNS.
Domain name system security extensions (DNSSEC) are a set of protocols that add a layer of security to the domain name system (DNS) lookup and exchange processes, which have become integral in accessing websites through the Internet.
DNSSEC
DNS Security Extensions (DNSSEC) were originally introduced in 1997 to address the security limitations of the original DNS protocol.
In a nutshell, DNSSEC provides authenticity of DNS records by leveraging a public key infrastructure (PKI). To do so, each domain maintains a private and public key pair. Each DNS record served is then signed with the private key, with the signature published in a resource record digital signature (RRSIG) record. As a result, a client can confirm the authenticity of the received record by checking this RRSIG against the domain’s public key (published in a separate DNSKEY record).
DNSSEC creates a secure domain name system by adding cryptographic signatures to existing DNS records. These digital signatures are stored in DNS name servers alongside common record types like A, AAAA, MX, CNAME, etc. By checking its associated signature, you can verify that a requested DNS record comes from its authoritative name server and wasn’t altered en-route, opposed to a fake record injected in a man-in-the-middle attack.
To facilitate signature validation, DNSSEC adds a few new DNS record types:
- RRSIG – Contains a cryptographic signature
- DNSKEY – Contains a public signing key
- DS – Contains the hash of a DNSKEY record
- NSEC and NSEC3 – For explicit denial-of-existence of a DNS record
- CDNSKEY and CDS – For a child zone requesting updates to DS record(s) in the parent zone.
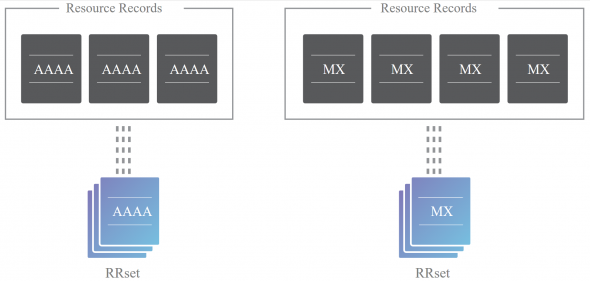
The first step towards securing a zone with DNSSEC is to group all the records with the same type into a resource record set (RRset). For example, if you have three AAAA records in your zone on the same label (i.e. label.example.com), they would all be bundled into a single AAAA RRset.
It’s actually this full RRset that gets digitally signed, opposed to individual DNS records. Of course, this also means that you must request and validate all of the AAAA records from a zone with the same label instead of validating only one of them.
Similar to HTTPS, DNSSEC adds a layer of security by enabling authenticated answers on top of an otherwise insecure protocol. Whereas HTTPS encrypts traffic so nobody on the wire can snoop on your Internet activities, DNSSEC merely signs responses so that forgeries are detectable. DNSSEC provides a solution to a real problem without the need to incorporate encryption.
DNSSEC adds two important features to the DNS protocol:
- Data origin authentication allows a resolver to cryptographically verify that the data it received actually came from the zone where it believes the data originated.
- Data integrity protection allows the resolver to know that the data hasn’t been modified in transit since it was originally signed by the zone owner with the zone’s private key.
DNSSEC implementation
In order for the Internet to have widespread security, DNSSEC needs to be widely deployed. DNSSEC is not automatic: right now it needs to be specifically enabled by network operators at their recursive resolvers and also by domain name owners at their zone’s authoritative servers. The operators of resolvers and of authoritative servers have different incentives to turn on DNSSEC for their systems, but when they do, more users are assured of getting authenticated answers to their DNS queries. Quite simply, a user can have assurance that they are going to end up at their desired online destination.
While DNSSEC is a good way to prevent many types of attacks, and despite several critical CVEs reported (one of the most famous is Dan Kaminsky’s cache poisoning attack, also known as the “Kaminsky bug”), its adoption statistics show that it is still not supported by many registrars around the world, and its adoption is really slow.
Many ISPs and key players in the infosec community still have doubts about DNSSEC being the right tool to secure the entire DNS ecosystem, due to the complex changes it involves for both registrars and DNS server providers.
Next-generation DNS implements all the practices recommended by DHS and ICANN; and provides the administrative security controls recommended by DHS to prevent unauthorized access to the zone files and DNS control settings.
These include:
- Single sign-on
- Two-factor authentication
- Strong password enforcement
- Session time outs
- Activity logging, and
- Role-based access controls (RBAC)
Additionally, some DNS vendors offering DNSSEC have removed obvious barriers that prevent businesses from implementing what have been more complex, but necessary security measures. Organizations shouldn’t have to give up performance when enabling DNSSEC, that means not compromising on traffic management functionality, and no performance impact. If you’d like to take it a step further, look into dedicated DNS, a redundant DNS solution that also supports DNSSEC.
Conclusion
All organizations are at risk of a cyberattack, and DNS offers a very attractive attack target. When you analyze your cybersecurity posture, keep DNSSEC in mind to better prepare your organization for all possible cyber threats. If you’re still not sure you’ll be able to protect your organization, contact us today to help you out with your performance and security needs.