Sign up to our Newsletter
A revolution is occurring as you read this. There has been a huge increase in the adoption of APIs and API-based applications. This surge in API use has opened up many opportunities, alongside a new world of vulnerability, allowing greater connectivity and accessibility, but also posing prevalent security threats.
APIs facilitate ease for interfacing between systems, they drive and connect web and mobile applications, SaaS apps, microservices environments, and IoT devices. Because they are so versatile, practical, and diverse, they also constitute a serious security breach in the absence of sufficient protection.
How One AI-Driven Media Platform Cut EBS Costs for AWS ASGs by 48%

Gartner predicts that by 2022 API abuse cases will become the most-frequent attack vector.
Last year alone there were over 5,100 breaches (a 33% increase from 2018), exposing 7.9B records (according to security magazine). Large organizations such as Facebook, Snapchat, Verizon, PayPal, Uber (and the list goes on) have all been hacked due to serious breaches in their APIs.
As they increase in functionality, API’s become more complex, and that means more weak points. Critical information passes through APIs, and this sensitive information allows the execution of operations against corporate servers and databases.
APIs are built by developers driven by innovation, not security people, they don’t think like attackers, and can therefore unintentionally overlook unique vulnerabilities in your APIs, creating opportunities for attackers and putting your organization at risk.
According to OWASP, 9 of the top 10 most critical web application security risks now include API components. Now you might be thinking, our business has a Web Application Firewall (WAF) and that get’s the job done, right?
Here’s why WAF isn’t enough:
- Cannot ensure up-to-date protection in a dynamic ever-changing environment
- The proxy-based architecture provides protection for limited attack types, not API threats
- Not comprehensive enough to understand the logic and unique behavior of every API
This is the part where we present our solution to the problem.
Currently, the only tool in the world that can detect API breaches and neutralize them in real-time. An API protection platform that continuously adapts to your agile environment, automatically distinguishing between malicious attacks and benign development changes.
One that can deploy in a matter of minutes, through a quick non-intrusive integration, and without any configuration.
How does it work?
Full visibility of all your APIs
Automatically and continuously discovers all public, private, and partner-facing APIs and applications across environments. Eliminates blind spots, determines sensitive data exposure, and keeps you protected, even as your environment evolves and changes.
Zero-Day Attacks Protection
Detect and prevent targeted attack attempts at the source level and eliminate the root of the attacks in real-time using big data and patented AI to identify attackers early (during reconnaissance).
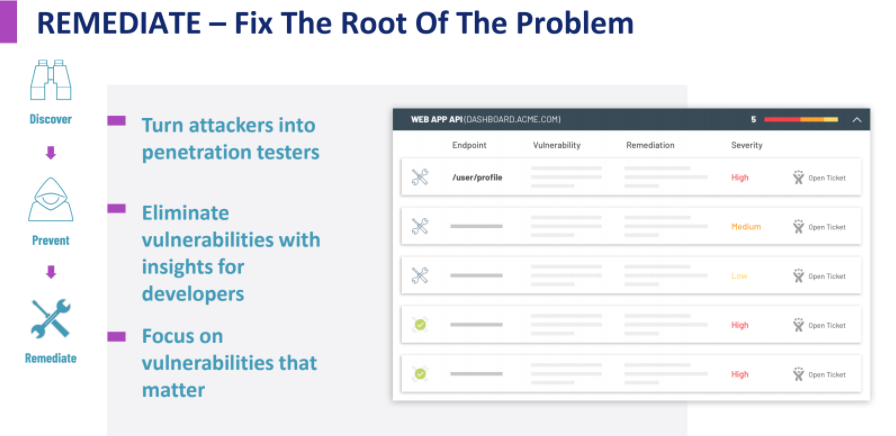
Eliminate Risks
Remove vulnerabilities and strengthen security with actionable insights for security teams and developers to identify and prioritize.
Protect your SaaS, web, and mobile applications from API breaches with the power of artificial intelligence and big data.
Get in touch with us to learn more about how we can keep your organization safe from API security threats.







