27th February, 2020
5 Min read
Book a Demo
New business initiatives and processes have created broader attack surfaces. Applications, users, and devices are moving outside of the traditional corporate zone of control, dissolving what was once the trusted perimeter, and enterprise security and networks must evolve to protect the business.
Providing employees with secure access to enterprise applications deployed behind the firewall is a core requirement for all businesses. Enterprises must also deal with the riskier proposition of providing access to a varied list of contractors, suppliers, partners, customers, and developers.
Reduce your AWS costs by over 50%
Discover your Cloud Saving Potential – Answer just 5 simple questions. AppsFlyer, Playtika, Lufthansa, IBM, top leading companies are already using our FinOps services.

Regardless of where these applications are hosted—whether in a public cloud or private data center—this is a complex, cumbersome task requiring on-premise hardware and software such as application delivery controllers (ADC), virtual private networks (VPN), identity and access management (IAM) systems, and more.
Yet with all of these technologies, enterprises are still exposed to a variety of security risks stemming from the fact that access to internal applications opens up the entire network to attack.
In this article we explain zero trust framework and what benefits it offers.
Zero trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter. No single specific technology is associated with zero trust; it is a holistic approach to network security that incorporates several different principles and technologies.
Zero Trust was created by John Kindervag, during his tenure as a vice president and principal analyst for Forrester Research, based on the realization that traditional security models operate on the outdated assumption that everything inside an organization’s network should be trusted.
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.”
Under the assumption that every user, request, and server is untrusted until proven otherwise, a zero trust solution dynamically and continually assesses trust every time a user or device requests access to a resource. This approach prevents attackers from exploiting weaknesses in the perimeter to gain entry, and, once inside, move laterally to access confidential applications and data.
The bottom line is data authentication is the foundation of Zero Trust. Users, endpoints, email and cloud applications have become communication channels that serve as attack vectors. In a Zero Trust model where you cannot trust anyone or any device, focusing the perimeter around data protection with intelligent authentication is the best security approach. Therefore, agencies must have a clear understanding of their users and their roles, their data, and their technology assets before beginning to implement Zero Trust.
Zero Trust is not dependent on a location. Users, devices and application workloads are now everywhere, so you cannot enforce Zero Trust in one location – it must be proliferated across your entire environment. The right users need to have access to the right applications and data.
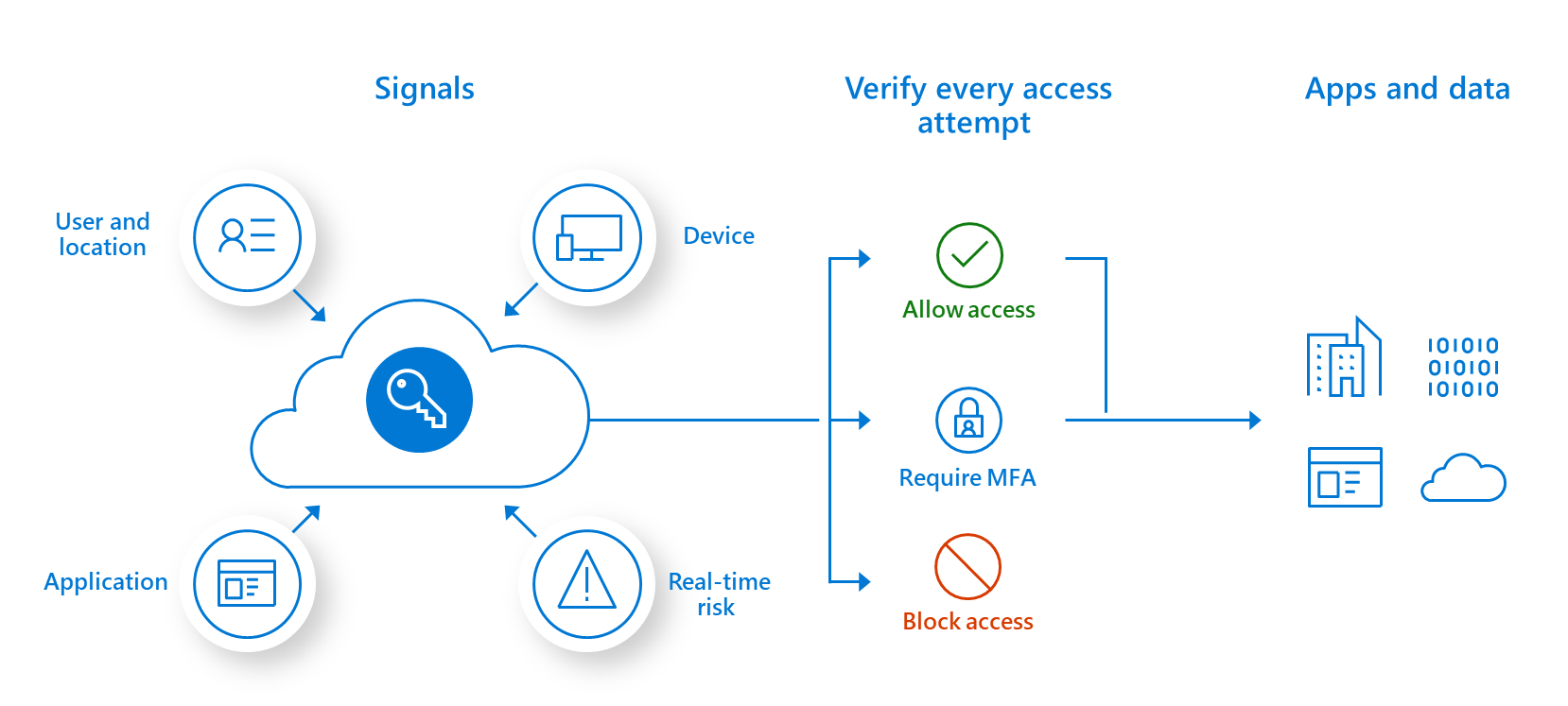
In addition to controls on user access, zero trust also requires strict controls on device access. Zero trust systems need to monitor how many different devices are trying to access their network and ensure that every device is authorized. This further minimizes the attack surface of the network.
A Zero Trust model replaces perimeter-centric security architecture. It ensures that security and access decisions are dynamically enforced based on identity, device, and user context. A Zero Trust security framework also dictates that only authenticated and authorized users and devices can access applications and data. At the same time, it protects those applications and users from advanced threats on the Internet.
Cloud-based zero trust solutions represent a new security paradigm specifically designed to secure applications in the cloud and in your data center. These solutions assume that there is no perimeter and that the environment is hostile.
This cloud-based zero trust architecture provides a single point of control and authentication to give end users SSO capabilities across all of their on-premise and cloud applications. Everything looks the same to the end user. Organizations moving to the cloud now have efficient and effective security for their cloud- based solutions.
At the same time, because a zero trust environment follows least access principles, it allows IT to offer each user with access to specific applications and data. Security managers no longer fear offering access to customers, partners, and suppliers because it can be tailored and tightly controlled.
In the past, organizations have had to make tradeoffs between strong security and a good, productive user experience.
Highly secure passwords are typically complicated and difficult to remember. They reduce productivity as users spend time reentering multiple, lengthy passwords — not to mention troubleshooting password problems with IT. When users attempt to remember complex passwords by writing them down, or use easy-to-remember passwords, they compromise security.
Zero trust solutions offer secure access, productivity, and ease of use. Simple, convenient MFA provides stronger security without the need to recall labyrinthine passwords. SSO (single sign-on) further enhances the user experience and improves employee productivity by allowing users to log in to all of the applications which they require and have access to, without needing to reauthenticate each time or getting sidetracked by syncing issues.
Solutions that require authentication for both the device and the user further enhance security because they require authentication using something the user knows (e.g., login and password) and something the user owns (e.g., device and security key).
Continuously adapting your enterprise’s approach to security in response to evolving business and threat landscapes is imperative. Transitioning to a Zero Trust security architecture enables you to simply and effectively safeguard your applications, users, and devices.
With zero trust cybersecurity solutions, organizations can not only obtain the security they need to protect their resources and data in today’s distributed organization, they can also realize substantial business benefit.
To learn more about how a zero trust model can benefit your business, improve perimeterless enterprise operations, and bolster your organization’s security posture, please contact us today.
Schedule a call with our experts. Discover new technology and get recommendations to improve your performance.